Mass-Customized Malware Lures: Don't trust your cat!
Usually, we find that e-mail used to trick users to malicious or spam sites is either not customized at all, or manually tailored for a particular recipient. A couple years ago at our RSA panel with Alan Paller and Ed Skoudis, I eluded to "mass customized" malware. Malware that automatically harvests social networking accounts or other open source information to find out how to best target you. For example, the malware may see that you "Like" Star Trek on Facebook and then will send you a link to a new movie trailer.
For a while now, I am seeing simple e-mails that appear to be doing something like that. The emails follow the same pattern. The "Real Name" displayed is the name of a person I know. The from e-mail address however has no relation to the person, and is usually some kind of free email 'yahoo'/'gmail' style address. The body of the e-mail itself is just a one liner with a link.
I did suspect Facebook as the source of the information. For most of the "senders" I had gotten these e-mails from in the past, there are other ways then Facebook that link me to them. But wasn't sure about it until now, when I received the e-mail below.
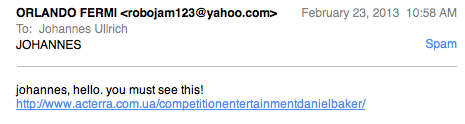
"Orlando Fermi" is the name for the Facebook page of my cat. I don't think there is anything else that links me to this particular name. The URL no longer works (for me at least... getting a 404 right now). But I would suggest you don't try it out.
In the past these e-mail led to various exploit kits, and on occassion spam. But it may also happen that an exploit kit will redirect you to spam if it doesn't have the right exploit for you. My cat's Facebook profile is public (sort of on purpose) and well, Mr. Fermi is a pretty mean cat so I wouldn't click on any link he sends me anyway which is one reason I didn't fall for this one.
And BTW: If you do happen to visit RSA: Ed, Alan and myself will have this years panel on Wednesday 9:20am in room 134. Lots of interesting stuff this year about targeted attacks, DDoS attacks and things like mobile malware stealing two factor auth tokens. (as usual, check the program guide for changes in room/time).
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
| Application Security: Securing Web Apps, APIs, and Microservices | San Diego | May 5th - May 10th 2025 |


Comments
;)
Rob
Feb 25th 2013
1 decade ago
I also find out that if you misspell your name by adding a special character like 'æ, ô, ö' then you can see where they got your name.
pêt lover
Feb 26th 2013
1 decade ago