Windows Defender Chrome Extension Detection
With the recent Cyberhaven Extension(2) attack, looking for specific Chrome extensions installed can be very helpful. If you are running Defender with enhanced vulnerability management, Defender automatically catalogs installed extensions by going to Vulnerability Management -> Inventories and selecting Browser Extension from the Defender Console. Also, you can do Hunt Queries on the DeviceTvmBrowserExtensions table.
For those who do not have this feature, you can still look for malicious extensions by searching for the Chrome Extension ID. This ID is used for the folder name on the computer and is easy to find. If you have other Chrome variant browsers, this query will also catch extensions in them. The query at the bottom(1) covers all the IDs listed in the article for Cyberhaven.
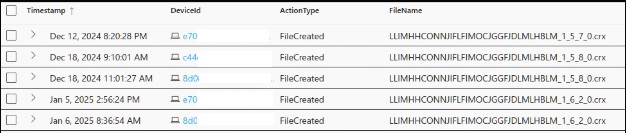
For this extension, the malicious version was 1.5.7
In the example above, we can see that version 1.5.7 was installed on Dec 12th and updated to 1.6.2 on Jan 5th.
There are several write-ups with more IOCs about this (2). The below query is a Zeek DNS query for Defender for the C&C domain.
DeviceNetworkEvents
| where ActionType == 'DnsConnectionInspected'
| extend json = todynamic(AdditionalFields)
| extend query = tostring(json.query)
| where query == "cyberhavenext.pro"
or query == "api.cyberhaven.pro"
|summarize by DeviceName
If you happen to have a user affected by this, they need to reset their passwords and session to anything sensitive they have accessed during that time.
(1)
DeviceFileEvents
|where FolderPath contains "nnpnnpemnckcfdebeekibpiijlicmpom" or
FolderPath contains "kkodiihpgodmdankclfibbiphjkfdenh" or
FolderPath contains "oaikpkmjciadfpddlpjjdapglcihgdle" or
FolderPath contains "dpggmcodlahmljkhlmpgpdcffdaoccni" or
FolderPath contains "acmfnomgphggonodopogfbmkneepfgnh" or
FolderPath contains "mnhffkhmpnefgklngfmlndmkimimbphc" or
FolderPath contains "cedgndijpacnfbdggppddacngjfdkaca" or
FolderPath contains "bbdnohkpnbkdkmnkddobeafboooinpla" or
FolderPath contains "egmennebgadmncfjafcemlecimkepcle" or
FolderPath contains "bibjgkidgpfbblifamdlkdlhgihmfohh" or
FolderPath contains "befflofjcniongenjmbkgkoljhgliihe" or
FolderPath contains "pkgciiiancapdlpcbppfkmeaieppikkk" or
FolderPath contains "llimhhconnjiflfimocjggfjdlmlhblm" or
FolderPath contains "oeiomhmbaapihbilkfkhmlajkeegnjhe" or
FolderPath contains "ndlbedplllcgconngcnfmkadhokfaaln" or
FolderPath contains "epdjhgbipjpbbhoccdeipghoihibnfja" or
FolderPath contains "cplhlgabfijoiabgkigdafklbhhdkahj" or
FolderPath contains "jiofmdifioeejeilfkpegipdjiopiekl" or
FolderPath contains "hihblcmlaaademjlakdpicchbjnnnkbo" or
FolderPath contains "llimhhconnjiflfimocjggfjdlmlhblm" or
FolderPath contains "ekpkdmohpdnebfedjjfklhpefgpgaaji" or
FolderPath contains "epikoohpebngmakjinphfiagogjcnddm" or
FolderPath contains "miglaibdlgminlepgeifekifakochlka" or
FolderPath contains "eanofdhdfbcalhflpbdipkjjkoimeeod" or
FolderPath contains "ogbhbgkiojdollpjbhbamafmedkeockb" or
FolderPath contains "bgejafhieobnfpjlpcjjggoboebonfcg" or
FolderPath contains "igbodamhgjohafcenbcljfegbipdfjpk" or
FolderPath contains "mbindhfolmpijhodmgkloeeppmkhpmhc" or
FolderPath contains "hodiladlefdpcbemnbbcpclbmknkiaem" or
FolderPath contains "lbneaaedflankmgmfbmaplggbmjjmbae" or
FolderPath contains "eaijffijbobmnonfhilihbejadplhddo" or
FolderPath contains "hmiaoahjllhfgebflooeeefeiafpkfde"
(2)https://arstechnica.com/security/2025/01/dozens-of-backdoored-chrome-extensions-discovered-on-2-6-million-devices/
(3)https://secureannex.com/blog/cyberhaven-extension-compromise/
--
Tom Webb
@tom_webb@infosec.exchange

Comments