Malicious Or Not? You decide...
On of the hardest tasks in security, and probably fundamentally an impossible task is to figure out if something is not malicious. Even the code you wrote yourself, once it exceeds a certain complexity, could include backdoors that you as the author missed. They may come in the form of vulnerabilities, or maybe it was bad advice that you followed (ever copied code from Stackoverflow?). Never mind malicious libraries or compilers.
Earlier today, a reader sent me a file asking just that question. Carlos received an anti-malware warning flagging a file as malicious. According to Virustotal, ESET-NOD32 flags it as "a variant of Win32/KingSoft.D potentially unwanted". This is a pretty weak signature. Virustotal also stated that the file is "Probably harmless" and that "There are strong indicators suggesting that this file is safe to use."
Next, I uploaded it to hybrid-analysis. Hybrid-Analysis returned the following risk assessment:
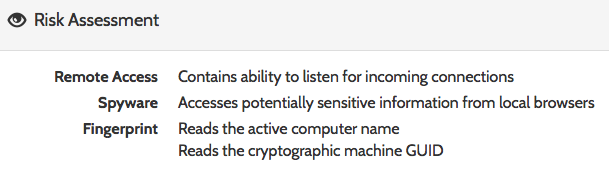
This looks quite a bit more malicious.
Some additional Google searches revealed that the file is likely part of "WPS Office," a free Chinese office suite that appears to be included for free with some HP Laptops.
My advice to Carlos was that the file is likely not malicious, but as long as he doesn't need WPS Office, he is probably better off deleting it to save some disk space. In short: bloatware.
What would your advice be? Here are the links to the results from Hybrid Analysis and Virustotal:
https://www.hybrid-analysis.com/sample/e3d74b6eb7f941125c35ae0ab2c5bd8d7116e6794f38b3879bddeb4b1570a433?environmentId=100
https://virustotal.com/en/file/e3d74b6eb7f941125c35ae0ab2c5bd8d7116e6794f38b3879bddeb4b1570a433/analysis/
| Application Security: Securing Web Apps, APIs, and Microservices | San Diego | May 5th - May 10th 2025 |


Comments
Anonymous
Feb 6th 2017
8 years ago
A valid signature isn't proof it is non-malicious, but valid signed executables that are malicious are uncommon. And if a stolen cert is caught being used to sign malicious, it gets revoked rather quickly. This is a year old again and the signature is still valid.
Those two facts alone would have me say non-malicious.
Anonymous
Feb 6th 2017
8 years ago
you are the best :)
great work
Anonymous
Feb 7th 2017
8 years ago
Anonymous
Feb 7th 2017
8 years ago
If it is NOT something you need/use is inherently a security risk (one more attack vector).
Anonymous
Feb 7th 2017
8 years ago
Anonymous
Feb 8th 2017
8 years ago