Apple Patches Everything. Releases iOS 17.1, MacOS 14.1 and updates for older versions fixing exploited vulnerability
Apple released iOS, iPadOS, macOS, tvOS, and Safari updates today. The iOS/macOS updates go back two "generations". This is particularly important for iOS 15, which now receives a patch for CVE-2023-32434, a vulnerability already exploited against earlier versions of iOS. This is also the only issue addressed for these earlier iOS versions.
Apple does not pre-announce these updates. But was expected to release this update yesterday to fix compliance issues unrelated to security vulnerabilities.
For Apple's original announcements, see https://support.apple.com/en-us/HT201222
| iOS 17.1 and iPadOS 17.1 | iOS 16.7.2 and iPadOS 16.7.2 | iOS 15.8 and iPadOS 15.8 | macOS Sonoma 14.1 | macOS Ventura 13.6.1 | macOS Monterey 12.7.1 | tvOS 17.1 | watchOS 10.1 | Safari 17.1 |
|---|---|---|---|---|---|---|---|---|
| CVE-2023-32434 [important] *** EXPLOITED *** Kernel An integer overflow was addressed with improved input validation. An app may be able to execute arbitrary code with kernel privileges. Apple is aware of a report that this issue may have been actively exploited against versions of iOS released before iOS 15.7. |
||||||||
| x | ||||||||
| CVE-2023-41072 [moderate] Contacts A privacy issue was addressed with improved private data redaction for log entries. An app may be able to access sensitive user data |
||||||||
| x | x | |||||||
| CVE-2023-42857 [moderate] Contacts A privacy issue was addressed with improved private data redaction for log entries. An app may be able to access sensitive user data |
||||||||
| x | x | |||||||
| CVE-2023-40449 [important] CoreAnimation The issue was addressed with improved memory handling. An app may be able to cause a denial-of-service |
||||||||
| x | x | x | x | x | ||||
| CVE-2023-40413 [important] Find My The issue was addressed with improved handling of caches. An app may be able to read sensitive location information |
||||||||
| x | x | x | x | x | x | |||
| CVE-2023-40416 [important] ImageIO The issue was addressed with improved memory handling. Processing an image may result in disclosure of process memory |
||||||||
| x | x | x | x | x | ||||
| CVE-2023-40423 [important] IOTextEncryptionFamily The issue was addressed with improved memory handling. An app may be able to execute arbitrary code with kernel privileges |
||||||||
| x | x | x | x | x | ||||
| CVE-2023-42849 [moderate] Kernel The issue was addressed with improved memory handling. An attacker that has already achieved kernel code execution may be able to bypass kernel memory mitigations |
||||||||
| x | x | x | x | x | x | |||
| CVE-2023-40408 [moderate] Mail Drafts An inconsistent user interface issue was addressed with improved state management. Hide My Email may be deactivated unexpectedly |
||||||||
| x | x | x | x | |||||
| CVE-2023-42846 [moderate] mDNSResponder This issue was addressed by removing the vulnerable code. A device may be passively tracked by its Wi-Fi MAC address |
||||||||
| x | x | x | x | |||||
| CVE-2023-42847 [moderate] Passkeys A logic issue was addressed with improved checks. An attacker may be able to access passkeys without authentication |
||||||||
| x | x | |||||||
| CVE-2023-42845 [moderate] Photos An authentication issue was addressed with improved state management. Photos in the Hidden Photos Album may be viewed without authentication |
||||||||
| x | x | |||||||
| CVE-2023-42841 [important] Pro Res The issue was addressed with improved memory handling. An app may be able to execute arbitrary code with kernel privileges |
||||||||
| x | x | x | x | |||||
| CVE-2023-41982 [moderate] Siri This issue was addressed by restricting options offered on a locked device. An attacker with physical access may be able to use Siri to access sensitive user data |
||||||||
| x | x | x | x | |||||
| CVE-2023-41997 [moderate] Siri This issue was addressed by restricting options offered on a locked device. An attacker with physical access may be able to use Siri to access sensitive user data |
||||||||
| x | x | x | x | |||||
| CVE-2023-41988 [moderate] Siri This issue was addressed by restricting options offered on a locked device. An attacker with physical access may be able to use Siri to access sensitive user data |
||||||||
| x | x | x | ||||||
| CVE-2023-40445 [moderate] Status Bar The issue was addressed with improved UI handling. A device may persistently fail to lock |
||||||||
| x | ||||||||
| CVE-2023-41254 [moderate] Weather A privacy issue was addressed with improved private data redaction for log entries. An app may be able to access sensitive user data |
||||||||
| x | x | x | x | x | ||||
| CVE-2023-40447 [critical] WebKit The issue was addressed with improved memory handling. Processing web content may lead to arbitrary code execution |
||||||||
| x | x | x | x | x | x | |||
| CVE-2023-41976 [critical] WebKit A use-after-free issue was addressed with improved memory management. Processing web content may lead to arbitrary code execution |
||||||||
| x | x | x | x | x | x | |||
| CVE-2023-42852 [critical] WebKit A logic issue was addressed with improved checks. Processing web content may lead to arbitrary code execution |
||||||||
| x | x | x | x | x | x | |||
| CVE-2023-41983 [moderate] WebKit Process Model The issue was addressed with improved memory handling. Processing web content may lead to a denial-of-service |
||||||||
| x | x | x | x | |||||
| CVE-2023-41977 [moderate] Safari The issue was addressed with improved handling of caches. Visiting a malicious website may reveal browsing history |
||||||||
| x | x | |||||||
| CVE-2023-32359 [moderate] WebKit This issue was addressed with improved redaction of sensitive information. A user's password may be read aloud by VoiceOver |
||||||||
| x | ||||||||
| CVE-2023-30774 [moderate] App Support This issue was addressed by removing the vulnerable code. Parsing a file may lead to an unexpected app termination or arbitrary code execution |
||||||||
| x | ||||||||
| CVE-2023-40444 [important] AppSandbox A permissions issue was addressed with additional restrictions. An app may be able to access user-sensitive data |
||||||||
| x | ||||||||
| CVE-2023-41989 [moderate] Emoji The issue was addressed by restricting options offered on a locked device. An attacker may be able to execute arbitrary code as root from the Lock Screen |
||||||||
| x | ||||||||
| CVE-2023-42854 [important] FileProvider This issue was addressed by removing the vulnerable code. An app may be able to cause a denial-of-service to Endpoint Security clients |
||||||||
| x | x | x | ||||||
| CVE-2023-42844 [moderate] Foundation This issue was addressed with improved handling of symlinks. A website may be able to access sensitive user data when resolving symlinks |
||||||||
| x | x | x | ||||||
| CVE-2023-38403 [critical] iperf3 The issue was addressed with improved checks. A remote user may be able to cause unexpected app termination or arbitrary code execution |
||||||||
| x | x | |||||||
| CVE-2023-42850 [moderate] LaunchServices The issue was addressed with improved permissions logic. An app may be able to access sensitive user data |
||||||||
| x | ||||||||
| CVE-2023-42861 [moderate] Login Window A logic issue was addressed with improved state management. An attacker with knowledge of a standard user's credentials can unlock another standard user's locked screen on the same Mac |
||||||||
| x | ||||||||
| CVE-2023-40405 [important] Maps A privacy issue was addressed with improved private data redaction for log entries. An app may be able to read sensitive location information |
||||||||
| x | ||||||||
| CVE-2023-42856 [moderate] Model I/O The issue was addressed with improved memory handling. Processing a file may lead to unexpected app termination or arbitrary code execution |
||||||||
| x | x | x | ||||||
| CVE-2023-40404 [important] Networking A use-after-free issue was addressed with improved memory management. An app may be able to execute arbitrary code with kernel privileges |
||||||||
| x | ||||||||
| CVE-2023-42438 [moderate] Safari An inconsistent user interface issue was addressed with improved state management. Visiting a malicious website may lead to user interface spoofing |
||||||||
| x | ||||||||
| CVE-2023-40421 [moderate] talagent A permissions issue was addressed with additional restrictions. An app may be able to access sensitive user data |
||||||||
| x | x | x | ||||||
| CVE-2023-42842 [moderate] Terminal The issue was addressed with improved checks. An app may be able to access sensitive user data |
||||||||
| x | ||||||||
| CVE-2023-4733 [moderate] Vim A use-after-free issue was addressed with improved memory management. Processing malicious input may lead to code execution |
||||||||
| x | ||||||||
| CVE-2023-4734 [critical] Vim A use-after-free issue was addressed with improved memory management. Processing malicious input may lead to code execution |
||||||||
| x | ||||||||
| CVE-2023-4735 [moderate] Vim A use-after-free issue was addressed with improved memory management. Processing malicious input may lead to code execution |
||||||||
| x | ||||||||
| CVE-2023-4736 [moderate] Vim A use-after-free issue was addressed with improved memory management. Processing malicious input may lead to code execution |
||||||||
| x | ||||||||
| CVE-2023-4738 [moderate] Vim A use-after-free issue was addressed with improved memory management. Processing malicious input may lead to code execution |
||||||||
| x | ||||||||
| CVE-2023-4750 [moderate] Vim A use-after-free issue was addressed with improved memory management. Processing malicious input may lead to code execution |
||||||||
| x | ||||||||
| CVE-2023-4751 [moderate] Vim A use-after-free issue was addressed with improved memory management. Processing malicious input may lead to code execution |
||||||||
| x | ||||||||
| CVE-2023-4752 [moderate] Vim A use-after-free issue was addressed with improved memory management. Processing malicious input may lead to code execution |
||||||||
| x | ||||||||
| CVE-2023-4781 [moderate] Vim A use-after-free issue was addressed with improved memory management. Processing malicious input may lead to code execution |
||||||||
| x | ||||||||
| CVE-2023-41975 [moderate] WindowServer This issue was addressed by removing the vulnerable code. A website may be able to access the microphone without the microphone use indicator being shown |
||||||||
| x | x | x | ||||||
| CVE-2023-41077 [moderate] Image Capture The issue was addressed with improved checks. An app may be able to access protected user data |
||||||||
| x | ||||||||
| CVE-2023-40401 [moderate] Passkeys The issue was addressed with additional permissions checks. An attacker may be able to access passkeys without authentication |
||||||||
| x | ||||||||
| CVE-2023-40425 [important] Sandbox A privacy issue was addressed with improved private data redaction for log entries. An app with root privileges may be able to access private information |
||||||||
| x | ||||||||
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
Sporadic scans for "server-info.action", possibly looking for Confluence Server and Data Center Vulnerability CVE-2023-22515
I noticed many scans for "/server-info.action" showing up in our "First Seen URLs" report. This URL didn't ring a bell at first but may be associated with CVE-2023-22515, a recent vulnerability in Confluence Server and Data Center.
Atlassian published an advisory describing this vulnerability on October 4th [1]. The vulnerability is a broken access control vulnerability. Initially exploited against a small number of sites, exploit code is now widely available. The trivial exploit will allow an unauthenticated user to create an admin account. For example, a request to exploit this issue may look like:
POST /setup/setupadministrator.action HTTP/1.1
Host: [target host]
Accept: */*
Connection: keep-alive
X-Atlassian-Token: no-check
Content-Length: 131
Content-Type: application/x-www-form-urlencoded
username=test&fullName=test&email=test&password=test&confirm=test
However, this isn't the only URL that is available for exploitation. Rapid7 first noted, and Atlassian later confirmed, that the vulnerability may also be exploited via the "/server-info.action" endpoint [2].
Today, I noticed that we did see some probes for the "server-info.action" URL in addition to the "setupadministrator.action" URL.
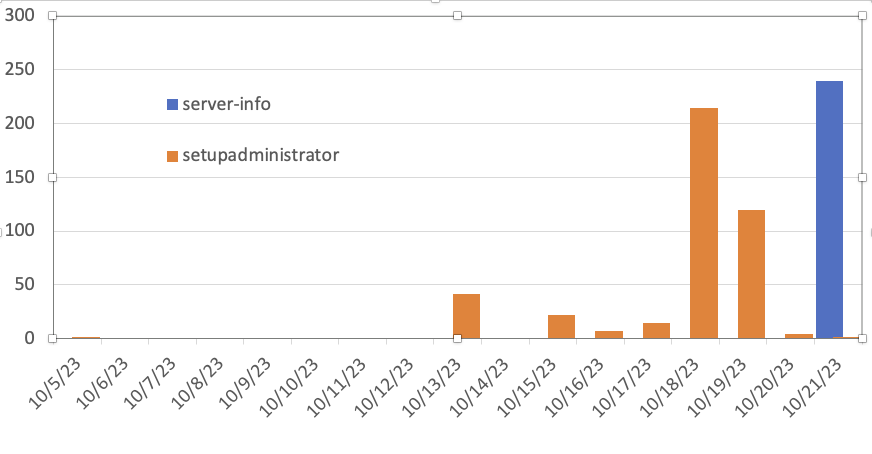
Please ensure that any filter you use covers both URLs and, even better, do not allow access to any Atlassian product from the open internet.
[1] https://confluence.atlassian.com/security/cve-2023-22515-privilege-escalation-vulnerability-in-confluence-data-center-and-server-1295682276.html
[2] https://www.rapid7.com/blog/post/2023/10/04/etr-cve-2023-22515-zero-day-privilege-escalation-in-confluence-server-and-data-center/
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|

Comments