DShield Sensor JSON Log Analysis
This is a review and analysis of some of my json DShield logs for a 9-day period. For this, I created some parsers using jq [1] and MS PowerBI which I described here to parse GeoIP [2] with the script previously posted here. This is the highlights from this timeframe 5 - 13 Dec 2022:
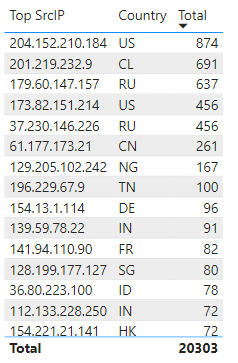
Top IP Overall
Top IP by Day
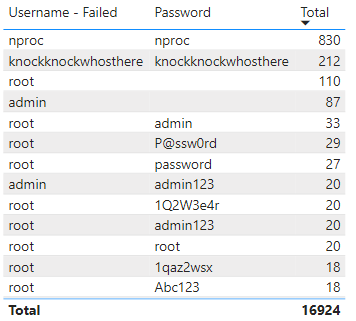
The most popular username/password in this 9-day period is knockknockwhosthere:
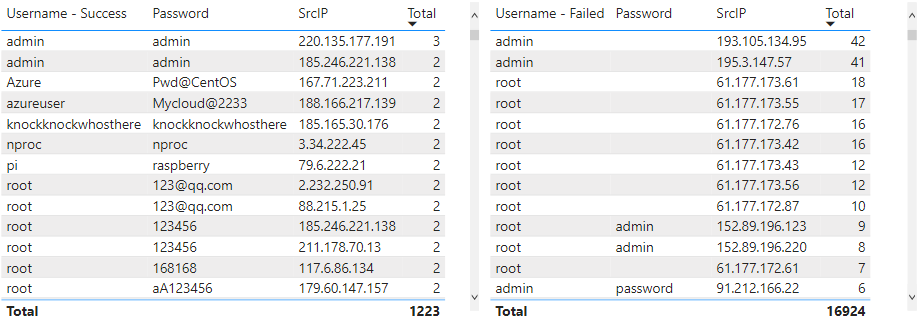
Successful Login by Username/Password
Failed Login by Username/Password
Comparing the usernames and passwords by IP address, the results were interesting. Several of the sources attempted multiple times to login without using any passwords.
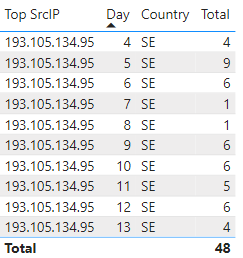
Reviewing top IP 193.105.134.95 has been reported over 150K to DShield since March 10, 2022 and was seen daily by the honeypot:
Initial Connection to Honeypot (Connect)
Here is an example of parsing cowrie logs using jq for the initial connection to the sensor
cat cowrie.json.2022-12-05 | jq 'select (.eventid == "cowrie.session.connect")' | jq '.src_ip + "," + (.src_port|tostring)+ "," + (.dst_port|tostring) + "," + .session + "," + .protocol + "," + .timestamp + ",1"' | tr -d '"'\
| tr -d '"' \
| sed '1i\SrcIP,SrcPort,DstPort,Session,Protocol,Timestamp,Total' >> connect.csv
Next time I will explore in details the commands, ssh versions and files sent to the DShield sensor.
[1] https://stedolan.github.io/jq/download/
[2] https://powerbi.microsoft.com/en-us/downloads/
[3] https://isc.sans.edu/diary/29370
[4] https://isc.sans.edu/diary/28872
[5] https://isc.sans.edu/ipinfo.html?ip=193.105.134.95
[6] https://handlers.sans.edu/gbruneau/scripts/process_geoip.sh
-----------
Guy Bruneau IPSS Inc.
My Handler Page
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu



Comments