VMware Security Advisory VMSA-2021-0010
VMware has issued a critical security advisory VMSA-2021-0010 (CVSSv3 score ranging from 6.5-9.8). The products affected are VMware vCenter Server and VMware Cloud Foundation, and addresses CVE-2021-21985 and CVE-2021-21986 [1].
References:
[1] https://www.vmware.com/security/advisories/VMSA-2021-0010.html
-----------
Yee Ching Tok, ISC Handler
Personal Site
Twitter
Uncovering Shenanigans in an IP Address Block via Hurricane Electric's BGP Toolkit
Today’s diary features a tip-off by one of our ISC diary readers Earl. Earl discovered some dodgy domains within the IP address block of 95.181.152.0/24 via the Hurricane Electric’s BGP Toolkit [1]. A look at the output of the IP address block of 95.181.152.0/24 showed a variety of domains that were related to popular sites such as Steam, Epic Games and Instagram, albeit with an assortment of misspelled URLs.
Some sites have been reported as deceptive sites and triggered browser warnings, while some sites displayed default Plesk configuration pages. As I dove in further to the data in 95.181.152.0/24, I found an active Instagram phishing page that purportedly offers Instagram verification badges (with reference to Figure 1 below).
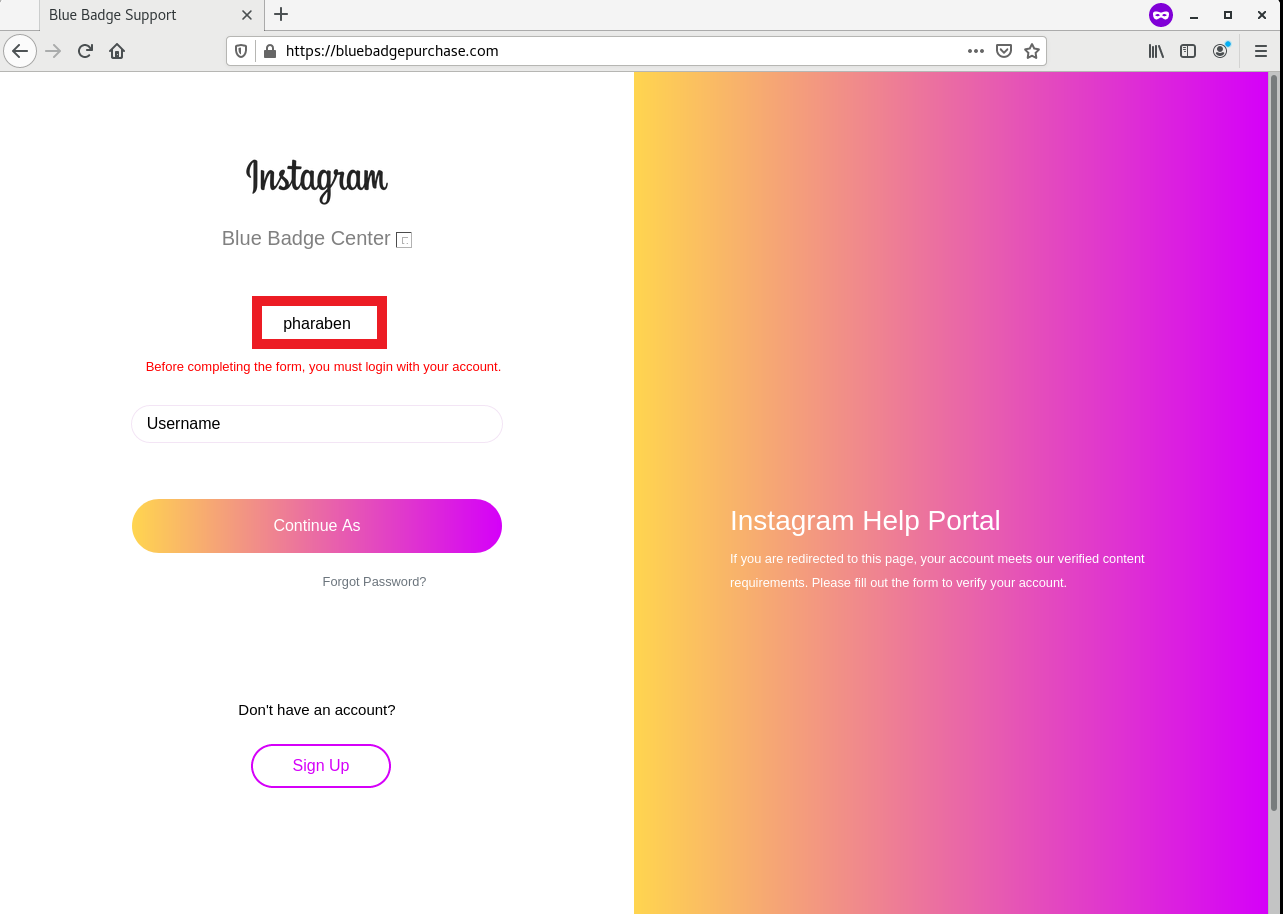
Figure 1: Screenshot of Instagram Verification Phishing Site
A closer look at the phishing page showed that various images used to construct the phishing page were taken from third-party image hosting sites (with reference to Figure 2). As I have mentioned in my previous diary entry [2], image hotlinking facilitates adversaries’ efforts in constructing phishing pages/e-mails. It was also interesting to note (from an OSINT perspective) that the default username shown in the page was “pharaben” (highlighted in red boxes in Figure 1 and 2).
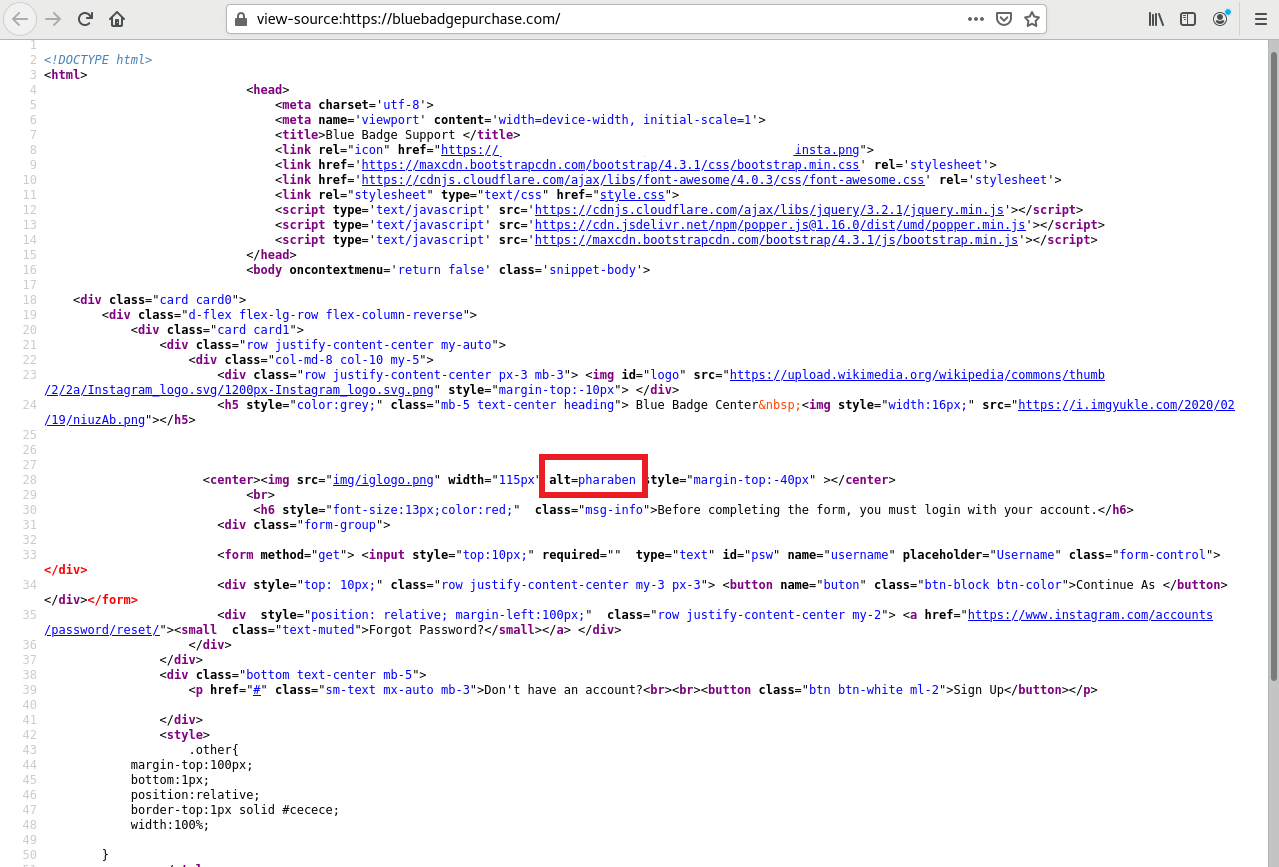
Figure 2: HTML Source of Phishing Site
This was most certainly an interesting finding with respect to this IP address block and the variety of phishing domain names associated with 95.181.152.0/24 using Hurricane Electric’s BGP Toolkit. While it can take some effort, this method could give some insight to IP address blocks and also uncover phishing sites proactively (and perhaps uncover cybercriminal activity or red teams).
The indicators of compromise of the phishing site are listed below.
Indicators of Compromise (IOCs):
hxxps:// bluebadgepurchase[.]com (please replace hxxps with https)
95.181.152[.]16
References:
[1] https://bgp.he.net/net/95.181.152.0/24#_dns
[2] https://isc.sans.edu/diary/27356
-----------
Yee Ching Tok, ISC Handler
Personal Site
Twitter

Comments