Traffic Analysis Quiz: Oh No... Another Infection!
Introduction
Today's diary is another traffic analysis quiz (here's the previous one) where you try to identify the malware based on a pcap of traffic from an infected Windows host. Download the pcap for today's quiz from this page, which also has a JPG image of the alerts list. Don't open or review the alerts file yet, because it gives away the answer.
As before, I'll provide the requirements for this quiz and give some background on the infection.
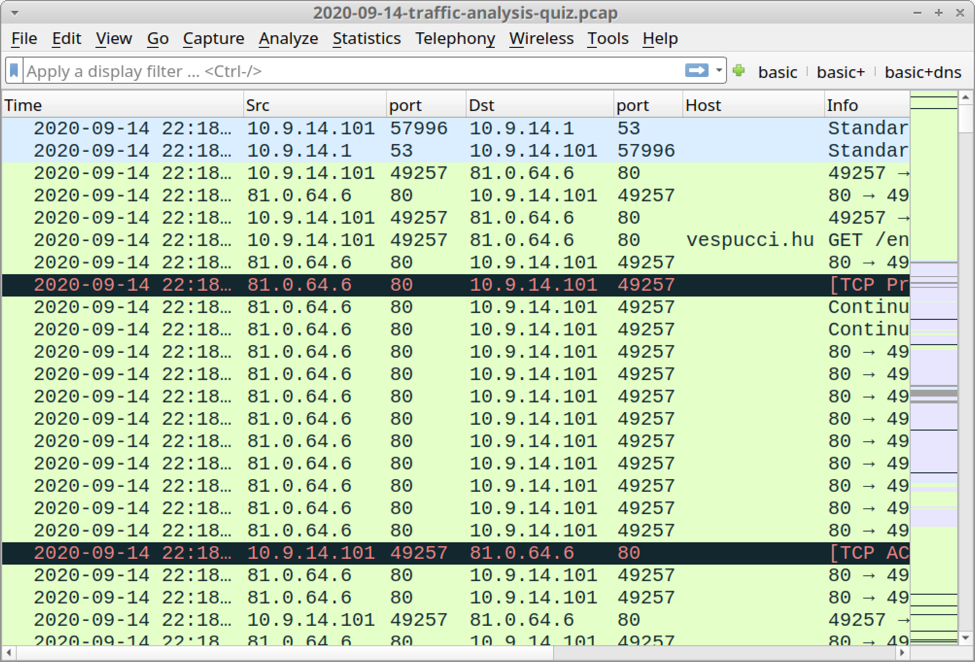
Shown above: Screenshot of the pcap for this quiz open in Wireshark.
Requirements
This type of analysis requires Wireshark. Wireshark is my tool of choice to review packet captures (pcaps) of infection activity. However, default settings for Wireshark are not optimized for web-based malware traffic. That's why I encourage people to customize Wireshark after installing it. To help, I've written a series of tutorials. The ones most helpful for this quiz are:
- Customizing Wireshark - Changing Your Column Display
- Using Wireshark - Display Filter Expressions
- Using Wireshark - Exporting Objects from a Pcap
Another requirement: use a non-Windows environment like BSD, Linux, or macOS. Why? Because this pcap contains HTTP traffic sending Windows-based malware. If you're using a Windows host to review the pcap, your antivirus (or Windows Defender) may delete the pcap or malware. Worst case? If you extract the malware from the pcap and accidentally run it, you might infect your Windows computer.
As always, beware, because there's actual malware involved here.
Background on the infection
This infection was caused by a link from an email that returned a Word document. Unfortunately, I do not have a copy of the email. The downloaded document has macros designed to infect a vulnerable Windows host.
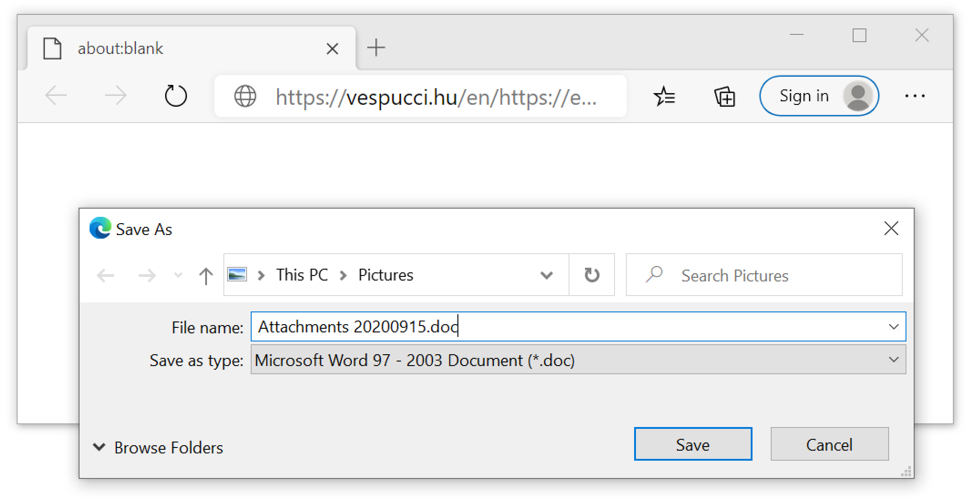
Shown above: Link from an email returning a Microsoft Word document.
Here is a link to any.run's sandbox analysis of a document retrieved from the initial URL. Normally, I state how this type of malware is ineffective against an up-to-date Windows 10 host running the latest version of Microsoft Office with default security settings.
However, I was able to download the Word document from this link without any warnings from Windows, and I merely had to click twice: once to get past Protected View, and one more time to enable macros. Tamper Protection and all other security measures were in place, but my Windows 10 lab host still became infected.
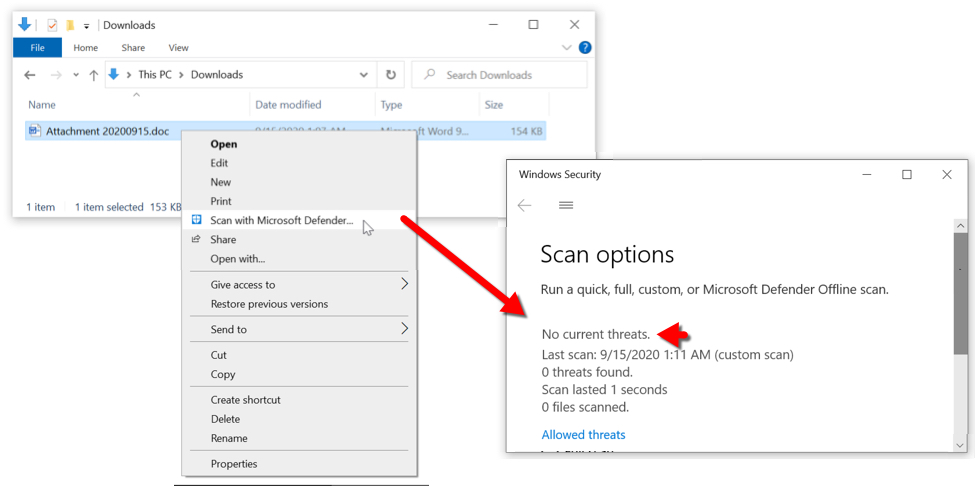
Shown above: After downloading the Word document, I checked it with Microsoft Defender, which said it was okay.
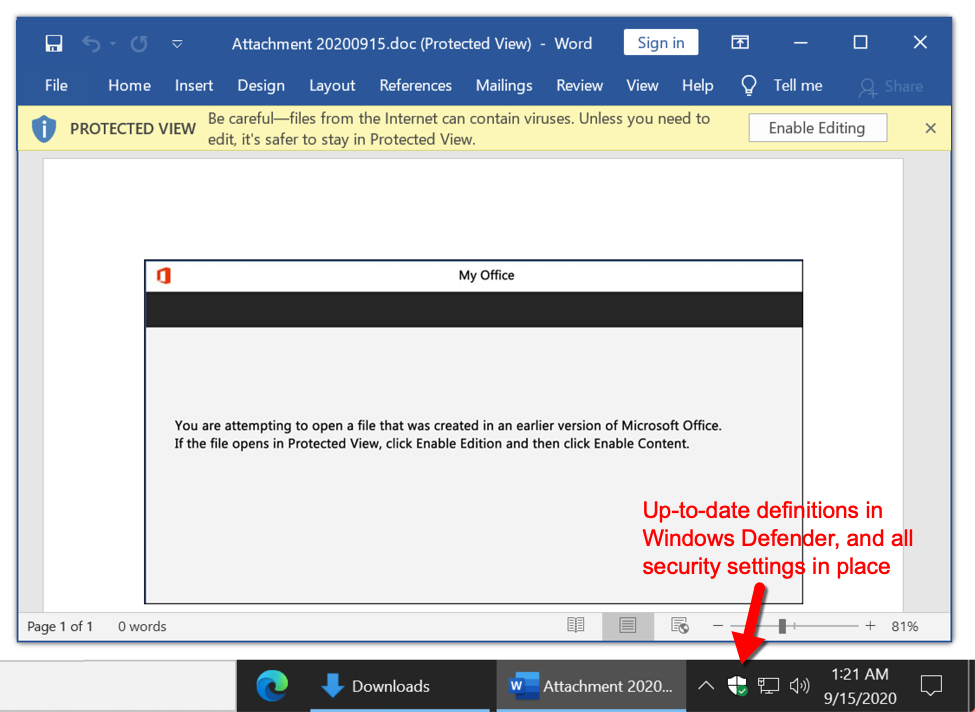
Shown above: Default security settings still allowed me to click twice and get past two warnings (exit Protected View, then enable macros).
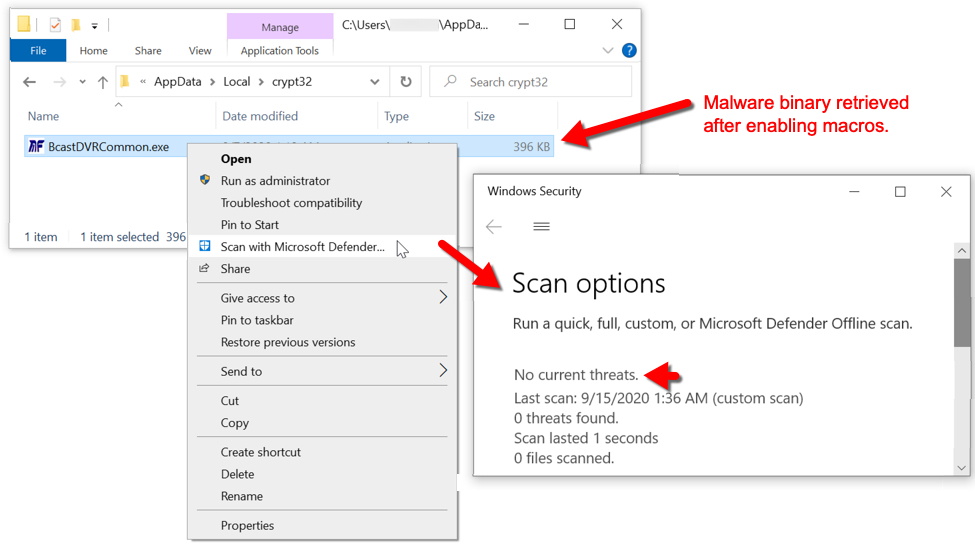
Shown above: Malware binary retrieved by Word macro was not detected or stopped by Microsoft's security measures.
This is a good example of how malware authors can evade security measures baked into Windows 10 and Microsoft applications. Of course, this type of email has to get through the spam and virus filters before this could happen... I mean, what are the odds?
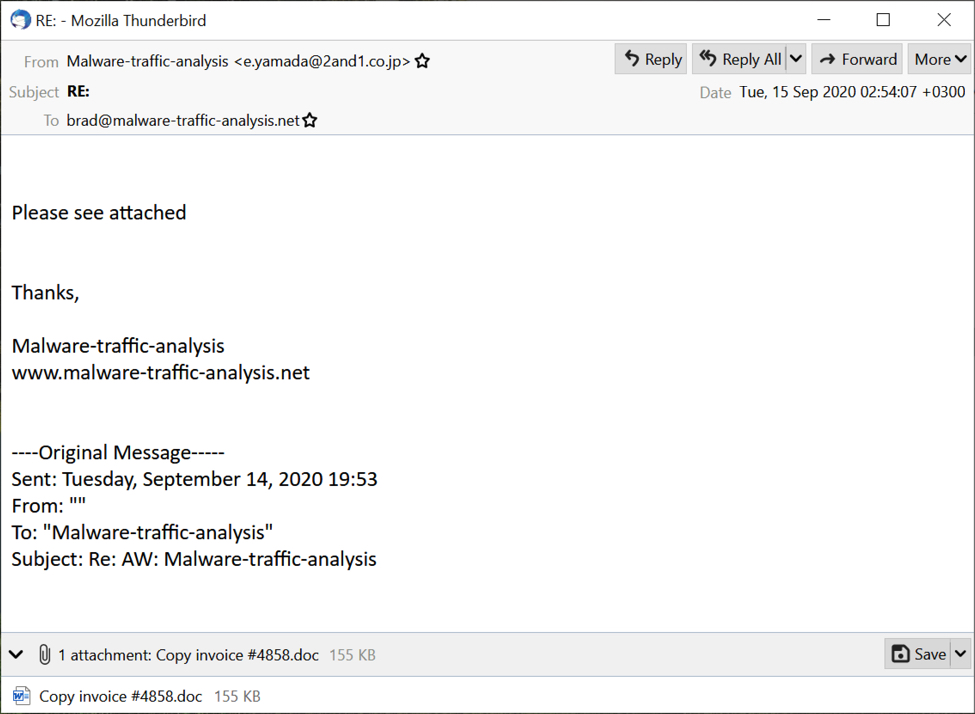
Shown above: A recent email that made it past my spam filters to my inbox.
Apparently, if malware distributors send out enough spam, some of it's bound to reach somebody, somewhere. This malware is updated often enough, that someone might receive it, click their way through some warnings, and infect their computer.
I guess that's why we still have a thriving market for security vendors and endpoint protection.
Reviewing the Pcap
I went over some of the basics last time, so I won't do that here today. The alerts should let you know what type of malware is involved, and if more than one type of malware is involved.
Final words
As usual, this quiz might not be hard for an experienced malware analyst, but some of you might find this interesting. The alerts really give this one away.
Again, a pcap of the traffic and a jpeg image showing associated alerts can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net

Comments