Odd "Protest" Spam (Scam?) Targeting Atlanta Police Foundation
After the killing of Rayshard Brooks by Atlanta police this week, a lot of protests and anger was directed at the Atlanta police department and its officers. Yesterday, we received an odd spam message, that may be targeting the Atlanta Police Foundation. The Atlanta Police Foundation is a not-for-profit organization collecting funding for various causes related to the Atlanta police. The Atlanta Police Foundation has been quoted in several news reports regarding the low morale of officers and officer resignation. It is no surprise that it is within scope for protests online.
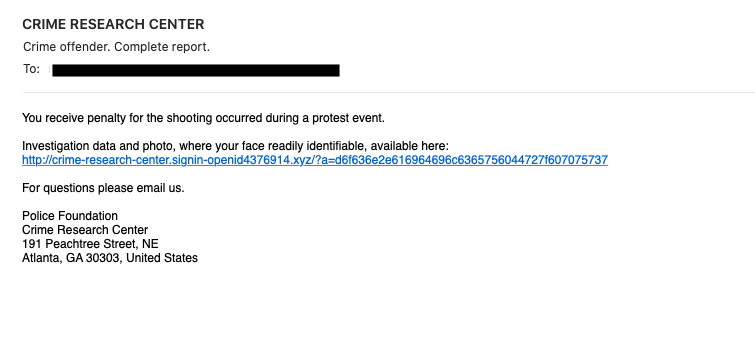
The initial message was a very clumsy piece of spam, that at first looked like an extortion scam or maybe an attempt at phishing
The poor grammar, and the fact that police is unlikely going to email you a warning if you shot someone at a protest, should make it obvious that this is a fake. The address of the "Police Foundation" (which is called the "Atlanta Police Foundation") is correct, even though the addition of "United States" may indicate that this email was not created by someone in the US.
Click on the link will lead (most of the time) to another similar message:
.png)
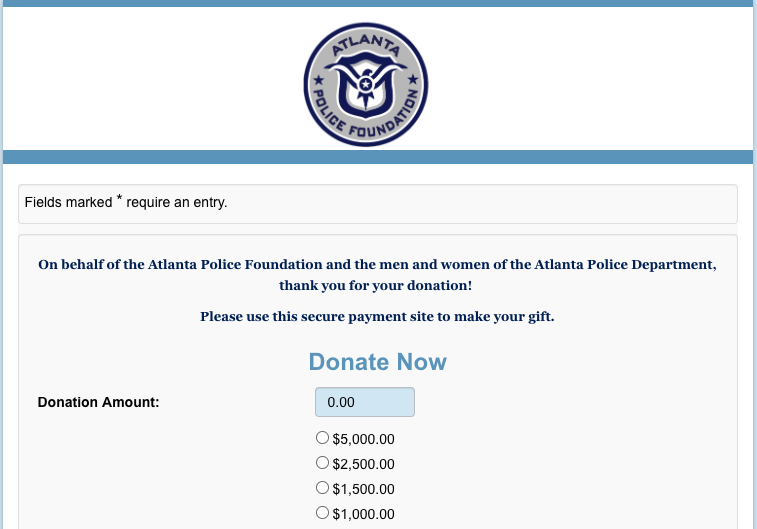
At this point, I expected a good old word document and a macro to get the latest version of some type of ransomware or trojan. No... instead, I got redirected to a donation page.
Ok... it must be a fake donation page. They are after money! Wrong again... this page is a legit donation page for the Atlanta Police Foundation.
So why would anybody do this? I very much assume that the initial email was not sent by the Atlanta Police to raise funds to survive the much talked about defunding of police. There are a few theories I have as to what could be happening here:
- Maybe the browser or IP I used was on some kind of blocklist that prevented me from seeing the actual scam. Some attackers have gotten pretty good at blocking researchers. I doubt this is the case here as nothing suggests that this attack is overly sophisticated (but then again: maybe they want you to think they are not sophisticated). I accessed the page from various IPs via VPNs. The page uses some simple obfuscated JavaScript that appears to detect fake user-agents to possibly detect an analyst. But the two URLs it directs to appear to be identical (it is possible that similar tests are performed server-side).
- At different times, I got slightly different behaviors. Sometimes I do not see the intermediate "threat" page, but instead, I am directed to the donation form directly, or to the home page of the Atlanta Police Foundation. So maybe the attack you receive is a bit up to the luck of the draw and some browser fingerprinting. The initial redirect uses lengthy obfuscated JavaScript.
- Or maybe someone is just trying to cause a "Layer 8" (human) denial of service against the Atlanta Police Foundation. With many recipients receiving an obviously fraudulent message leading to a donation form, they may report it as fake (that was my initial gut feeling) and cause the donation form to be shut down. This is currently my "most likely" explanation.
What's your guess as to what is the goal of the attack?
Some of the URLs used in the attack:
Link in the email: hxxp[:]//crime-research-center[.]signin-openid4376914[.]xyz
First Redirect: hxxps[:]//crime-research-center[.]sign[.]me/id/case/3890193
Threat Page: hxxps[:]//crime-research-center[.]sign[.]me/dt/t
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS Technology Institute
Twitter|
Sextortion to The Next Level
For a long time, our mailboxes are flooded with emails from “hackers” (note the quotes) who pretend to have infected our computers with malware. The scenario is always the same: They successfully collected sensitive pieces of evidence about us (usually, men visiting adult websites) and request some money to be paid in Bitcoins or they will disclose everything. We already reported this kind of malicious activity for the first time in 2018[1]. Attacks evolved with time and they improved their communication by adding sensitive information like a real password (grabbed from major data leaks) or mobile phones.
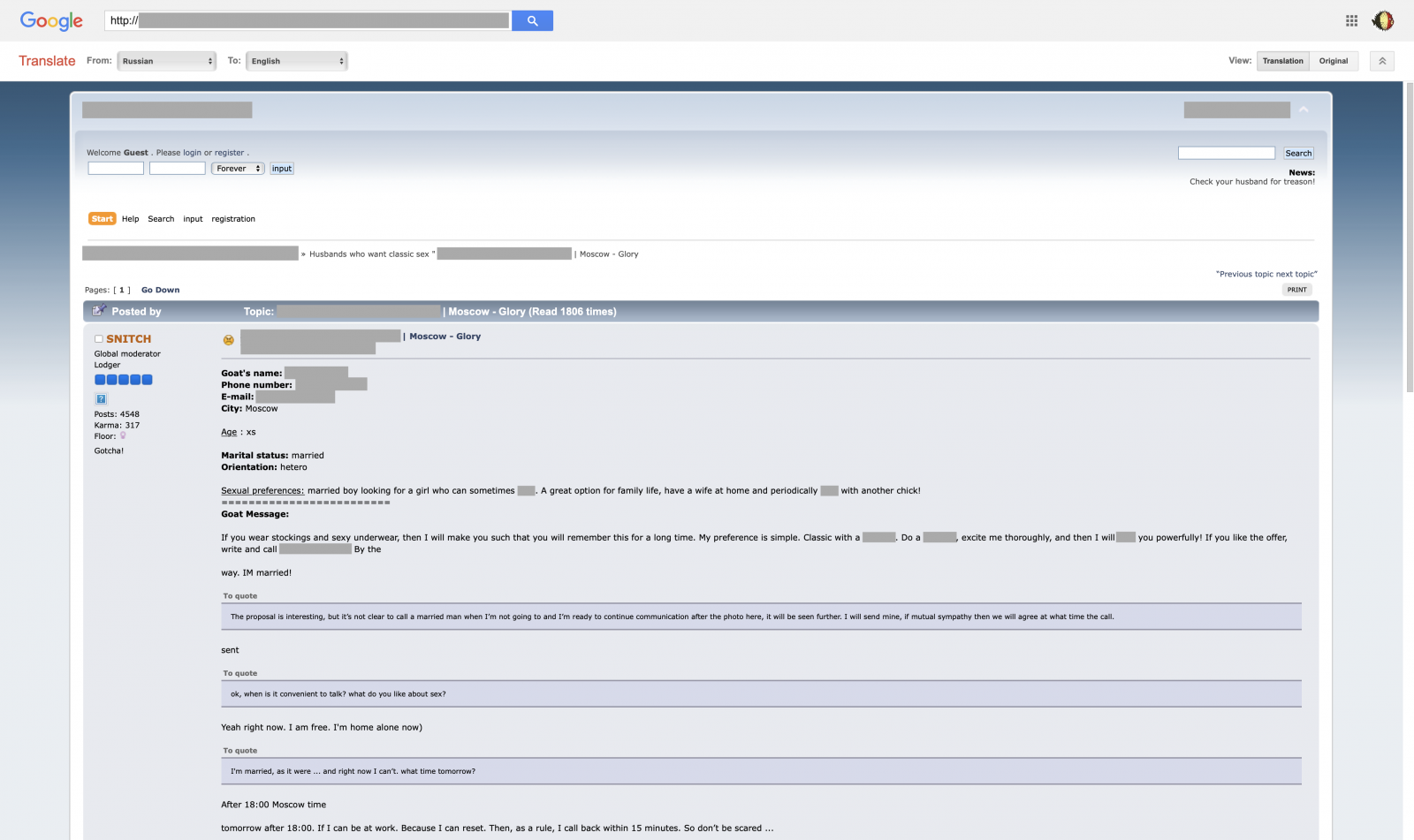
Now, they are going one step further and use more nasty ways to collect information about their victims. They use social engineering techniques in a bad way. We are been notified by one of our readers of a Ukrainian forum containing information about people looking for "good times". How do they work?
The bad guys create fake accounts on dating websites pretending to be young women looking for new contacts and probably more. It's clear that it does not take a while before being contacted by people looking for extramarital relations. They initiate contact and grab interesting information about the victim. In such a scenario, collected pieces of evidence are totally legit: name, mobile phone, location, sexual preferences, etc. Details are published on the forum, as well as conversations and pictures. To be "unlisted", they have to register on the forum and pay some money to "help the project".
Here is a screenshot of the forum's main page. As you can see it is quite active:
Notes:
- The forum has been visited through Google Translate
- The way it works is based in translated pages, some details might be wrong
- I tried to remove all offensive words from the screenshots, apologize if some remain
.png)
Once they caught a potential victim, they start cheating and collect as much information as possible. Everything is posted on the forum.
They provide information about the process to be unlisted (once the victim paid):
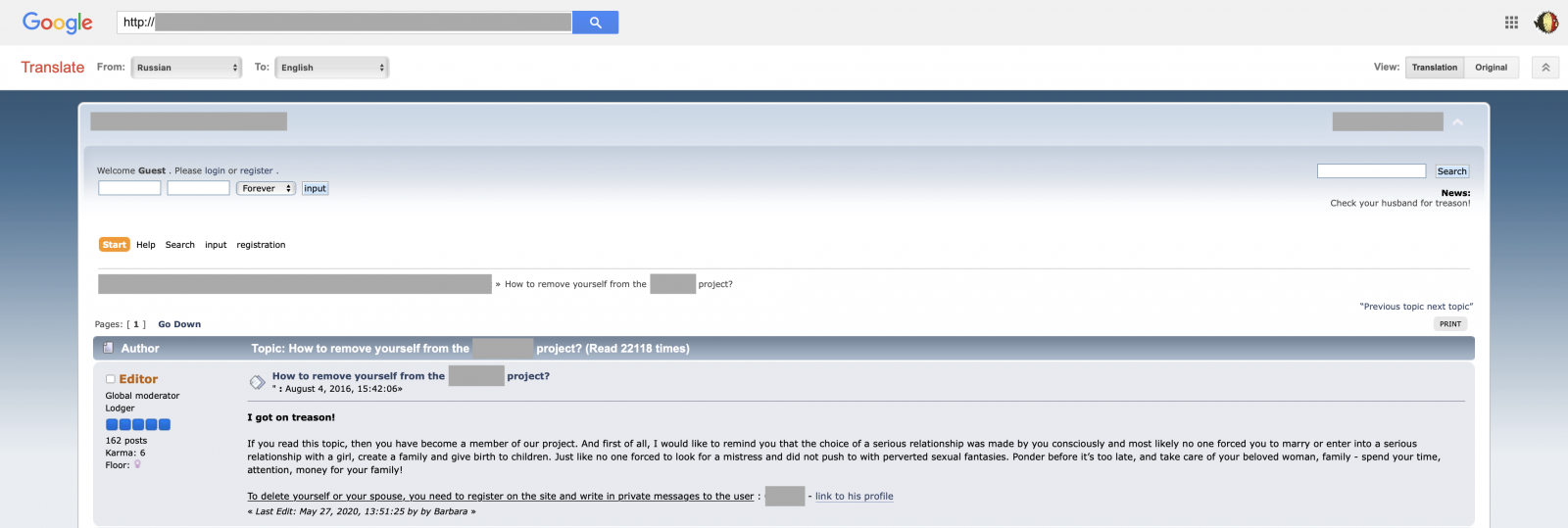
The forum seems to be online for a while but is still filled with new data. The problem is that, even if the victim pays, the forum is indexed by Google and other search engines (like the very popular yandex.ru). This makes the process to be unlisted very difficult, if not impossible!
People are free to act as they want on the Internet, our goal is not to blame anybody but, at least, we must warn you. Be very careful when you browse dating websites looking for new contacts. This reminds me of the story of the Ashley Madison breach[2] when high-profile people were found in the leaked database and they registered with their corporate email addresses...
[1] https://isc.sans.edu/forums/diary/Sextortion+Follow+the+Money/23922
[2] https://en.wikipedia.org/wiki/Ashley_Madison_data_breach
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key

Comments