Behavioural Malware Analysis with Microsoft ASA
When you need to quickly analyze a piece of malware (or just a suspicious program), your goal is to determine as quickly as possible what’s the impact. In many cases, we don’t have time to dive very deep because operations must be restored asap. To achieve this, there are different actions that can be performed against the sample: The first step is to perform a static analysis (like extracting strings, PE sections, YARA rules, etc). Based on the first results, you can decide to go to the next step: the behavioural analysis. And finally, you decide to perform some live debugging or reverse-engineering. Let’s focus on the second step, the behavioural analysis.
To perform the analyze, the malware must be executed in an air-gapped system or a sandbox (please be careful about this!) and tools can be used to detect what actions are performed and what changed on the infected system. To achieve this, you need tools. The easier way is to analyze the malware in an automated sandbox that will give you a detailed report but sandboxes aren’t always the best option. Why? If the sandbox is running in the cloud or operated by a third-party provider, can you trust it? Often the sandbox does not mimic exactly a corporate device with your own tools and configuration.
To perform behavioural analysis, there are common tools like ProcessMonitor[1], ProcessHacker[2], APIMonitor[3] or Regshot[4] (to check what’s happening at system level). There are many more, the most important is to build your personal toolbox that you can deploy in no time when required. One of the tools that I like most is RegShot. It takes a “snapshot” of the Windows registry at a time ’t’, take a second one at a time ’t+1’ (when the malware has been executed) and displays the differences between the two captures.
In 2012, Microsoft released a tool called “Attack Surface Analyzer”. The idea is, like Regshot, to search for differences between two snapshots when installing a new application in a Windows environment. The good news, they released the version 2.0 last month! Why not use the tool to detect changes in a system infected by a piece of malware?
Here is an example. Take the first snapshot (let’s call them “Before” and “After”):
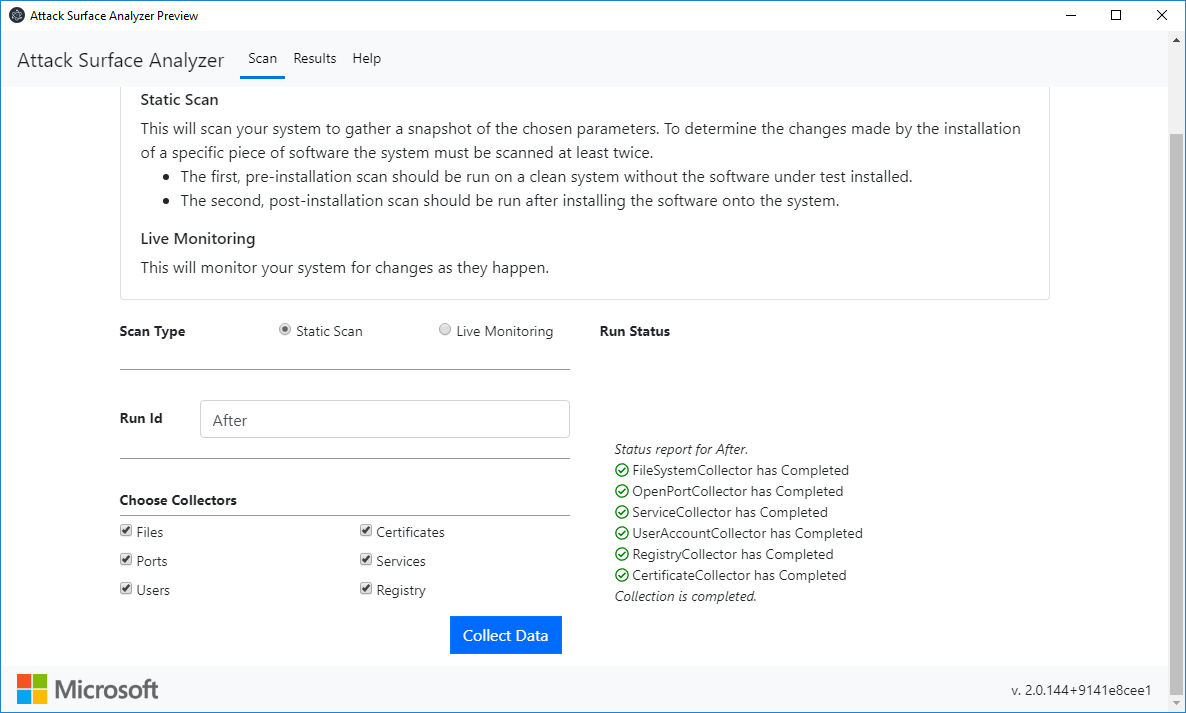
Infect the system by the malware sample and take the second snapshot. Now we can search for infection pieces of evidence:
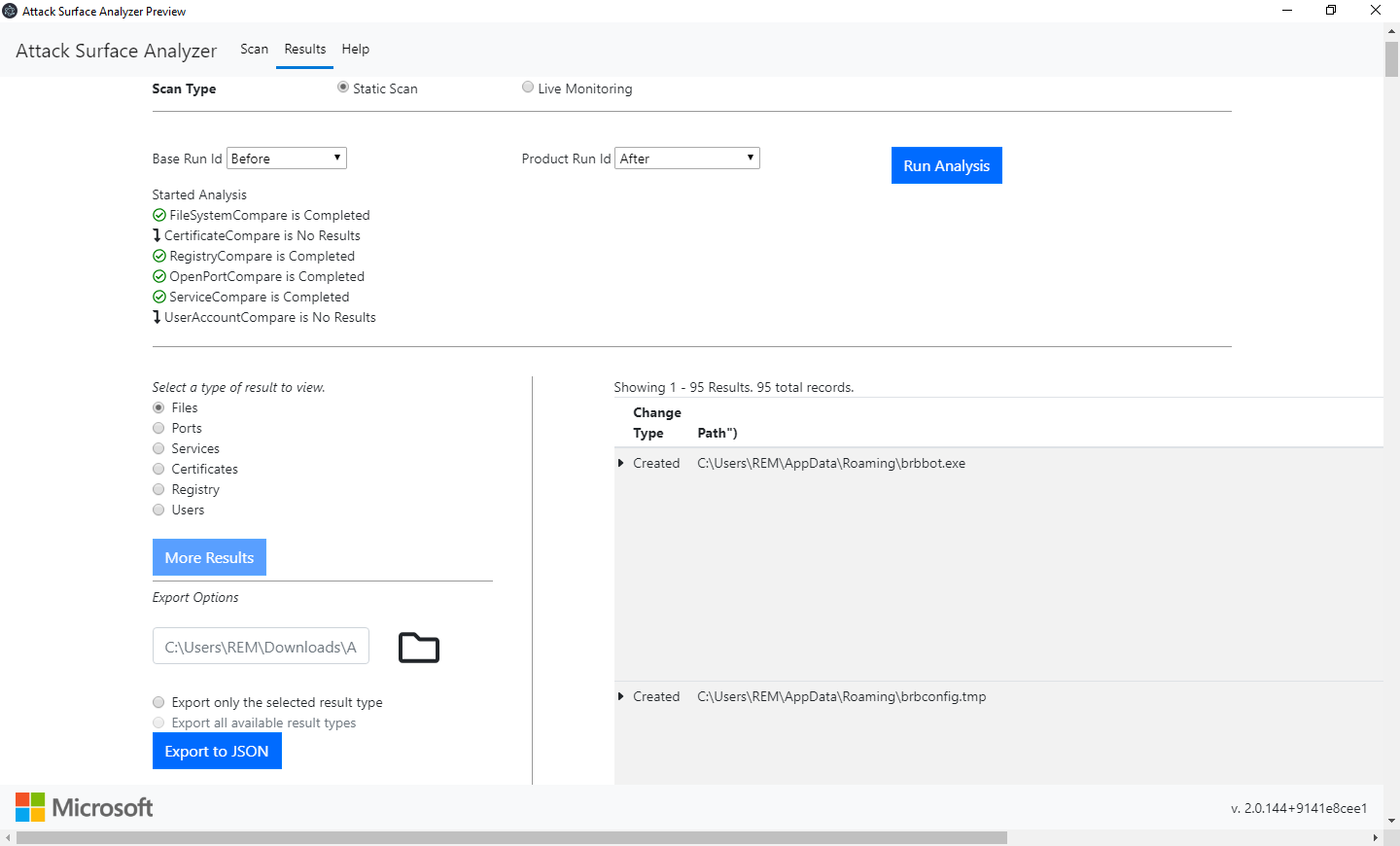
If you need to exchange data with another tool or platform, it’s possible to export data in JSON:
{
"Compare": {
"Path": "C:\\Users\\REM\\AppData\\Roaming\\brbconfig.tmp",
"Permissions": "O:BAG:S-1-5-21-1866265027-1870850910-1579135973-513D:(A;;FA;;;SY)(A;;FA;;;BA)(A;;FA;;;S-1-5-21-1866265027-1870850910-1579135973-1000)",
"Size": 73,
"RowKey": "usO+caB0ykbh9JRLCjwzMw=="
},
"BaseRowKey": "",
"CompareRowKey": "usO+caB0ykbh9JRLCjwzMw==",
"BaseRunId": "Before",
"CompareRunId": "After",
"ChangeType": "CREATED",
"ResultType": "FILE"
}
Currently, ASA logs the following artefacts:
- File system (static snapshot and live monitoring available)
- User accounts
- Services
- Network Ports (listeners)
- Certificates
- Registry (Windows only)
It does not log created processes, threats, MUTEX or network traffic but Microsoft could add more data in a future version (as they explain on the project page).
Some good points for ASA:
- It’s not well-known by malware developers and I never see a sample looking for it as an anti-debugging technique
- You just need to unzip the archive to run it, GUI and a command line versions exist
- Microsoft provides versions for Windows, MacOs & Linux!
The tool is available on the Microsoft GitHub page[5].
[1] https://docs.microsoft.com/en-us/sysinternals/downloads/procmon
[2] https://processhacker.sourceforge.io/
[3] http://www.rohitab.com/apimonitor
[4] https://sourceforge.net/projects/regshot/
[5] https://github.com/microsoft/AttackSurfaceAnalyzer
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key

Comments