A Comparison Study of SSH Port Activity - TCP 22 & 2222
I added a while ago to my honeypot TCP 2222 usually associated with SSH traffic to compare the amount of scans targeting port 22 and 2222 over a period of 7 days. What I have noticed, only about 50% more of the traffic is going to TCP 22 the default SSH service. The activity reported for the past month to DShield has been pretty consistent for TCP 2222[1]. I used the latest version of rockNSM released a few weeks ago with the new added dashboard to track the activity.
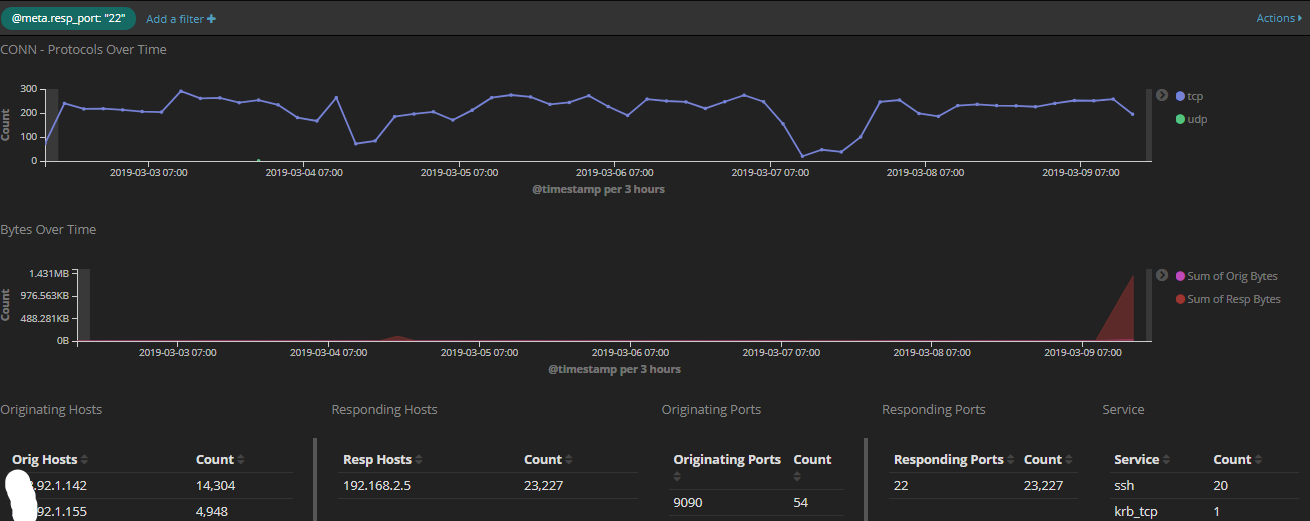
This graph shows port 22 over the past 7 days
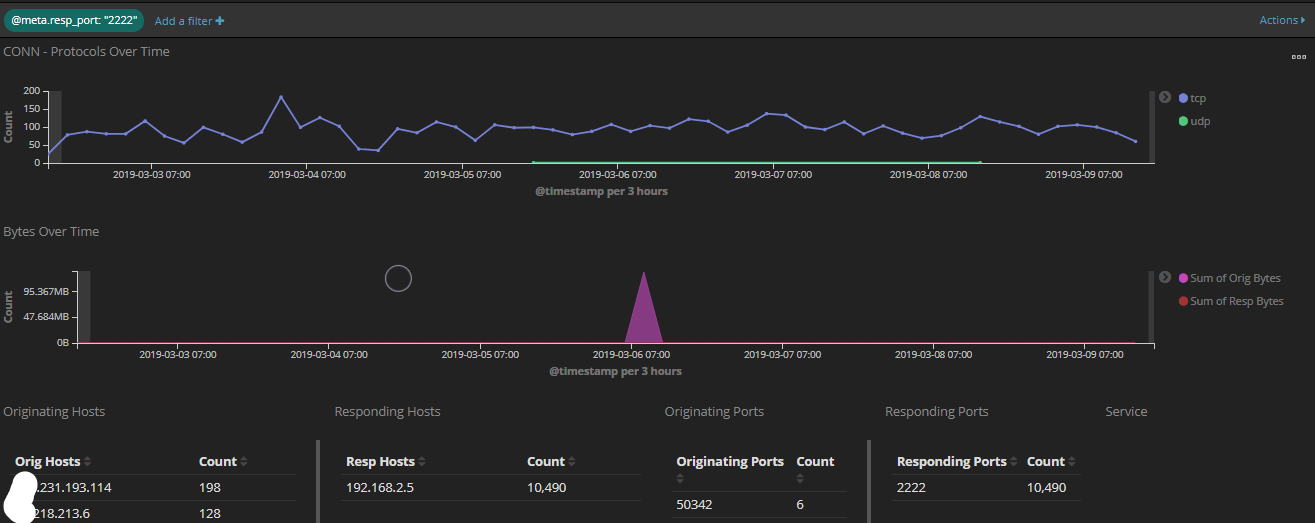
This graph shows port 2222 over the past 7 days
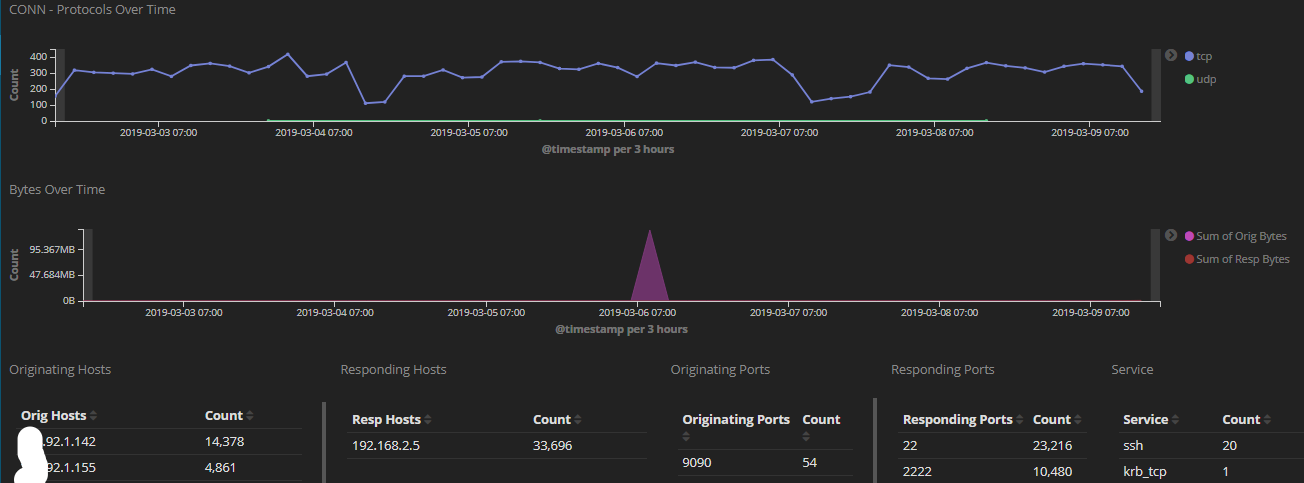
This graph show both 22 and 2222 over the past 7days
I wrote a diary last year where I posted a list of various client types and versions. Over the past several weeks, I received 9664 SSH probe to TCP 2222. This is the breakdown of the various SSH clients used:
SSH-2.0-libssh-0.6.3 8060
SSH-2.0-libssh2_1.8.0 567
SSH-2.0-libssh_0.8.2 519
SSH-2.0-libssh-0.2 298
SSH-2.0-Go 107
SSH-2.0-libssh2_1.4.3 66
SSH-2.0-sshlib-0.1 18
SSH-2.0-libssh-0.6.5 8
SSH-2.0-paramiko_2.1.3 5
SSH-2.0-paramiko_2.0.2 3
SSH-2.0-libssh2_1.7.0 3
SSH-2.0-paramiko_2.1.2 2
libssh 0.6 and later is vulnerable to CVE-2018-10933 and the most common hasshServer values posted here.
If you are interested in trying out the latest version of rockNSM 2.3, I recently updated my step-by-step guide and posted it here on the handlers server.
[1] https://isc.sans.edu/port.html?port=2222
[2] https://rocknsm.io/
[3] https://handlers.sans.edu/gbruneau/rockNSM_2.3.htm
[4] https://isc.sans.edu/forums/diary/SSH+Scans+by+Clients+Types/23201
[5] https://gist.github.com/0x4D31/35ddb0322530414bbb4c3288292749cc
-----------
Guy Bruneau IPSS Inc.
My Handler Page
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu

Comments