Text Banking Scams
Over the past few days I have been getting a few phone text scams that kind of look realistic except for certain flaws that are fairly easy to pick out, however this is where it is important to read the whole URL. First, if you don't have a banking account with the bank that appears to be texting you, you would just ignore and delete it. Most bank won't text or email you regarding issues with your account. However, if you do online banking with this bank you might be tempted to check it out.
.png)
The example that I picked is a text with this URL www.13bm0-olbanking-rec0nfirm-l0gin-secured.ml [1]. When you examine closely the details in the URL, it contains several errors; where it should be an "o" in bmo is has been replaced by a zero "0", the same with reconfirm and login and the country code is incorrect, it should be a dot com. Analysis of the site by urlscan shows the site is located in Amsterdam not in Canada but the picture of the scam [2] site looks very realistic compared to the real site [3].
Most banks have a mechanism to report such scams, BMO has a help page to either call or send them an email about this kind of scams [4] so other don’t get caught. If you are uncertain about your bank fraud policy, they usually have an online page about what to do.
[1] https://urlscan.io/result/78cc141d-5cb9-49c1-bd94-b44121042b2c/#summary
[2] https://urlscan.io/screenshots/78cc141d-5cb9-49c1-bd94-b44121042b2c.png
[3] https://www1.bmo.com/onlinebanking/cgi-bin/netbnx/NBmain?product=5
[4] https://www.bmo.com/home/popups/about/report-fraud
-----------
Guy Bruneau IPSS Inc.
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu
SMBLoris - the new SMB flaw
While studying the infamous EternalBlue exploit about 2 months ago, researchers Sean Dillon (zerosum0x0) and Zach Harding (Aleph-Naught-) found a new flaw in the Server Message Block (SMB) protocol that could allow an adversary to interrupt the service by depleting the memory and CPU resources of the targeted machine on a Denial of Service (DoS) attack.
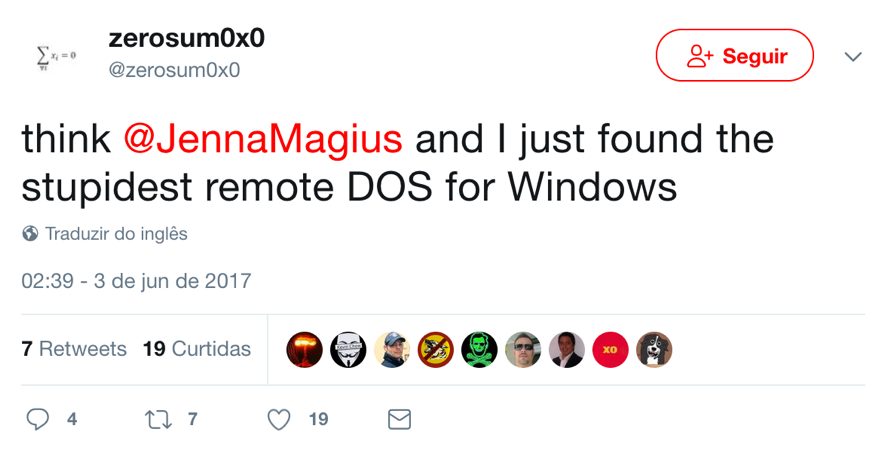
Tweet used to announce the flaw [2]
According to an article posted by ThreatPost [1], the flaw called SMBLoris was privately reported to Microsoft in early June, but the company considered it to be of moderate impact and that it would not be considered a security breach. In addition, it would probably not even be fixed.
As announced, some bug details were presented yesterday during a presentation at DEFCON 25 in Las Vegas. The attack is similar to another called SlowLoris [4] (hence also the similarity of the name) by allowing an attacker with a single machine and low bandwidth to be able to interrupt a service through a DoS attack. The difference is that SlowLoris affected Web servers.
Technically speaking, the problem occurs with the accumulation of a 4-bytes buffer called NBSS used during SMB session establishment which are allocated in the physical RAM and can not be swapped out. Triggering this, an attacker who initiates a large amount of connections to the service will be able to deplete the memory resources and after the CPU on the target.
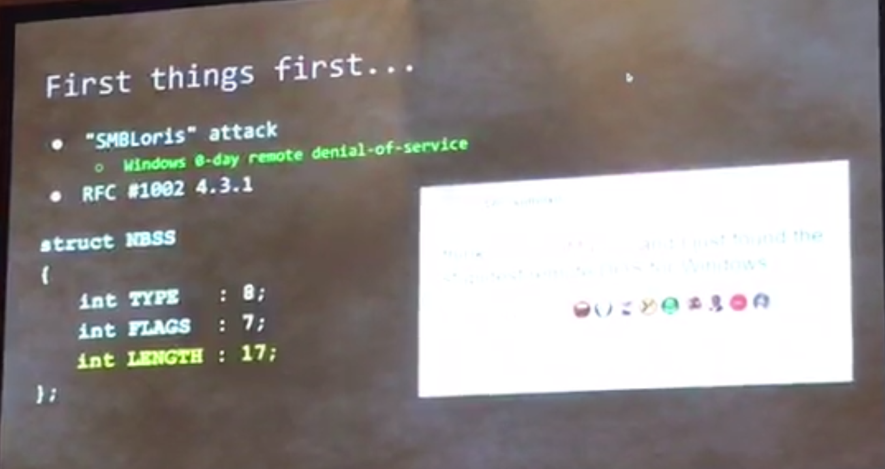
NBSS buffer details
In the demonstration, an 8 GB memory server became unresponsive in a few seconds - note in the following figure the rapid increase in memory consumption during the attack.
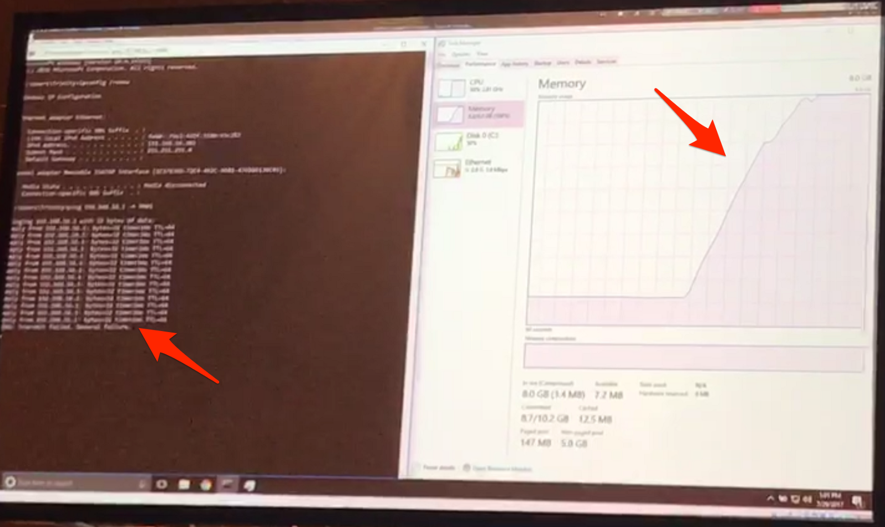
SMBLoris attack demonstration
There is no update from Microsoft to fix the problem - so it has been considered a zero-day. For now, as a mitigation measure, the recommendation is to use a packet filter, like a Firewall, to limit the number of connections from a same source to the Windows servers on port 445 (SMB).
References
[1] https://threatpost.com/windows-smb-zero-day-to-be-disclosed-during-def-con/126927/?utm_source=kasperskysocialchannel.com&utm_medium=REAL%20Solutions%20Technologies,%20LLC&utm_campaign=kasperskysocialchannel.com
[2] https://twitter.com/zerosum0x0/status/870862422327689216
[3] https://www.defcon.org/html/defcon-25/dc-25-speakers.html#Dillon
[4] https://web.archive.org/web/20090822001255/http://ha.ckers.org/slowloris/
--
Renato Marinho
Morphus Labs | LinkedIn | Twitter

Comments