Malspam on 2017-04-11 pushes yet another ransomware variant
Introduction
I ran across some interesting malicious spam (malspam) on Tuesday morning 2017-04-11. At first, I thought it had limited distribution. Later I found several other examples, and they were distributing yet another ransomware variant. I personally haven't run across this paricular ransomware until now.
The ransomware is very aware of its environment, and I had use a physical Windows host to see the infection activity. This diary examines the malspam and its associated ransomware.
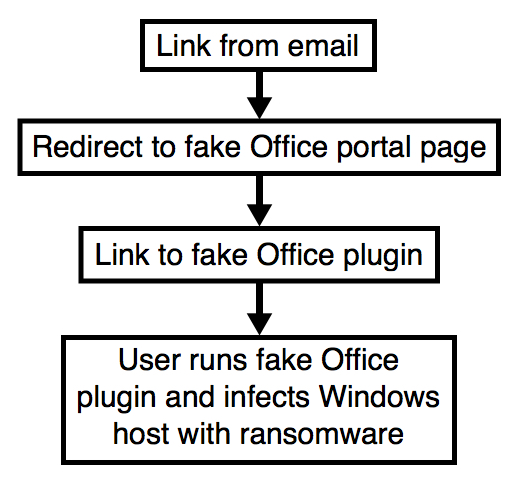
Shown above: Chain of events for an infection from this malspam.
The emails
I collected 14 samples of the malspam on Tuesday 2017-04-11. It started as early as 14:12 UTC and continued through at least 17:03 UTC. Each email had a different subject line, a different sender, different message text, and a different link to click.
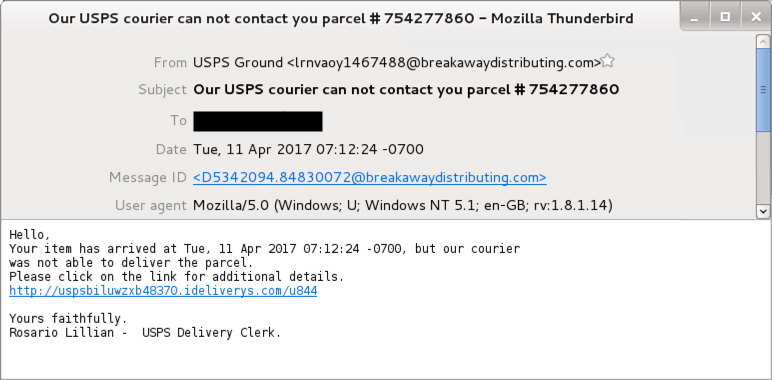
Shown above: An example of the malspam.
Senders:
- "USPS Ground" <lrnvaoy1467488@breakawaydistributing.com>
- "USPS Station Management" <oh53@fullertonautoservice.com>
- "USPS Priority" <jzj8127@holdintogold.com>
- "USPS Ground" <ritimyza607@rcn.cl>
- "USPS International" <n6784@atkinsonlandleveling.com>
- "USPS Ground" <osy7@brucezone.com>
- "USPS Priority Delivery" <w45@hhydro.com>
- "USPS Ground" <qucup08565428@rodarmex.com>
- "USPS SameDay" <ik844547@sheldons.com>
- "USPS Priority" <aohmiid6332@zvizdez.ru>
- "USPS Ground" <cjl66732@remiolofa.com>
- "USPS Ground" <pyasuj51@pffindia.com>
- "USPS Express Delivery" <utujim74880307@flyjetpool.com>
- "USPS Ground" <dip023221@mycanadore.ca>
Subject lines:
- Delivery problem, parcel USPS #07681136
- Delivery problem, parcel USPS #766268001
- Delivery problem, parcel USPS #886315525
- New status of your USPS delivery code: 74206300
- New status of your USPS delivery code: 573677337
- New status of your USPS delivery code: 615510620
- Our USPS courier can not contact you parcel # 754277860
- Please recheck your delivery address USPS parcel 67537460
- Please recheck your delivery address USPS parcel 045078181
- Re:
- Status of your USPS delivery ID: 45841802
- We have delivery problems with your parcel # 30028433
- We have delivery problems with your parcel # 48853542
- We have delivery problems with your parcel # 460730503
The traffic
The following links were in the emails. All are subdomains of ideliverys.com on 47.91.88.133 port 80. The domain ideliverys.com was registered the day before on Monday 2017-04-10.
- uspsbiluwzxb48370.ideliverys.com - GET /u844
- uspsecjyuqke13584571.ideliverys.com - GET /tiyau72
- uspsnhes06611040.ideliverys.com - GET /p41733
- uspsoefi471.ideliverys.com - GET /zjhyi265
- uspsreoyohme58288.ideliverys.com - GET /yxot3007
- uspsrojafav558540.ideliverys.com - GET /qnympenw4
- uspsueyrbti3030420.ideliverys.com - GET /avega046508
- uspsuuougdeb13563307.ideliverys.com - GET /hip44
- uspsuxsazui65.ideliverys.com - GET /zuhjxai826625
- uspsvavy3.ideliverys.com - GET /qlwevgya2715078
- uspsvhxenco218438.ideliverys.com - GET /fgl0067027
- uspsvreid556443.ideliverys.com - GET /acai8521471
- uspsyvponyfu63.ideliverys.com - GET /ysiwc47537447
- uspszoaoohan13382521.ideliverys.com - GET /uzoxy330
Any given moment, each email link led to a 404.html page that redirected to the same fake Office portal URL. The following were Microsoft Office portal pages with links to the ransomware:
- 194.30.251.100 port 80 - digitalecosystems.com - GET /wp-content/plugins/counter/1.htm
- 217.112.180.3 port 80 - network.mrtg.belcenter.net - GET /.simg/counter/1.htm
- 103.16.146.2 port 80 - brutenutrition.net - GET /temp_cms/libs/sysplugins/counter/1.htm
- 207.5.165.140 port 80 - bettermannow.com - GET //wp-content/counter/1.htm

Shown above: Example of a 404.html page leading to a fake Office portal URL.
These fake portal pages all had links for Google Docs URLs that returned the ransomware. The ransomware was disguised as an Office plugin. Those URLs (at least the ones I've seen so far) were all reported to Google.
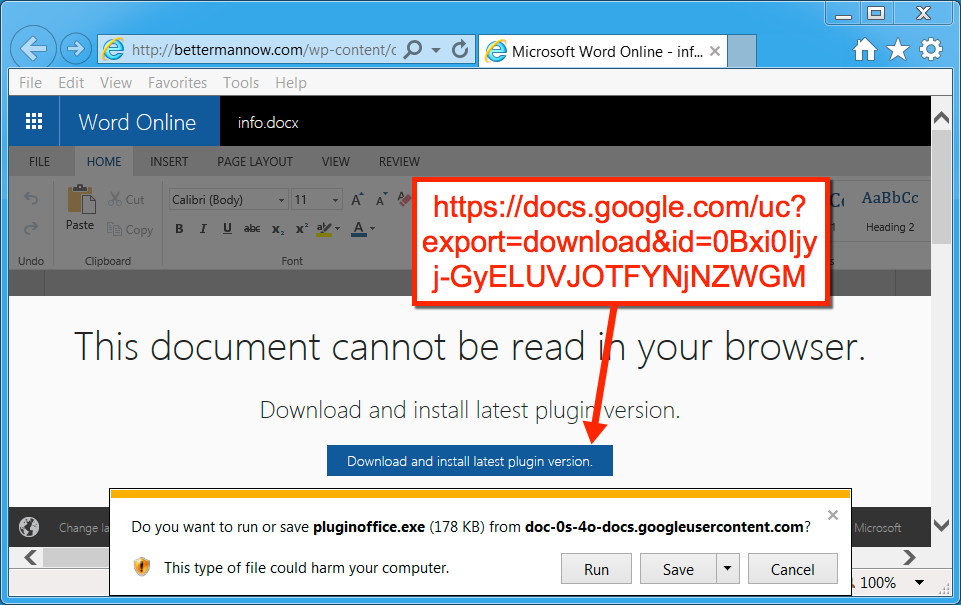
Shown above: One of the fake Office portal pages with a Google Docs link for the ransomware.
The ransomware
The ransomware samples didn't run properly on my virtual machine (VM). The samples also didn't run properly on free sandbox tools like malwr.com and reverse.it. I finally got an infection using a physical Windows host. The encrypted files were all renamed with .MOLE as a file extension. Decryption instructions were dropped as a text file named INSTRUCTION_FOR_HELPING_FILE_RECOVERY.TXT to the desktop and any directory with encrypted files. Email addresses from the instructions were oceanm@engineer.com and oceanm@india.com.
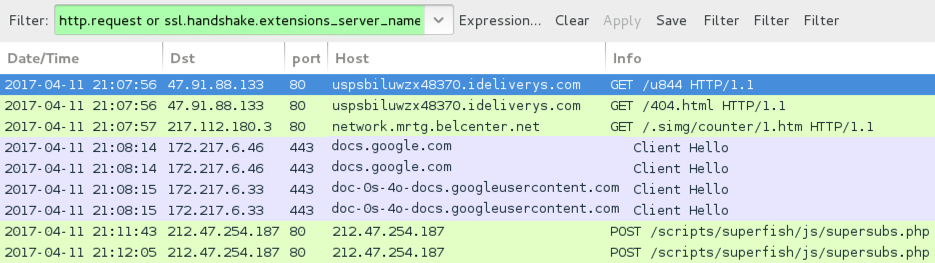
Shown above: Traffic from the infection filtered in Wireshark.
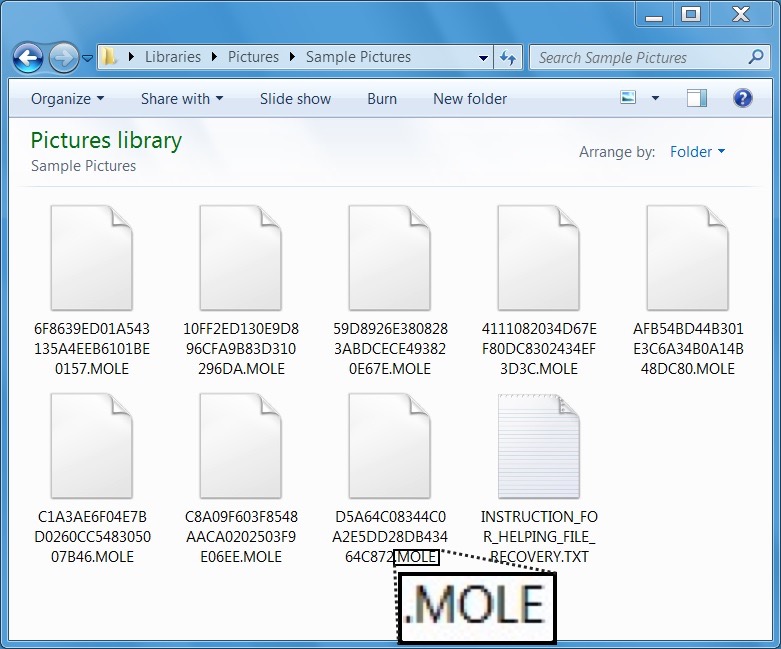
Shown above: Personal files on my infected host had .MOLE for a file extension.
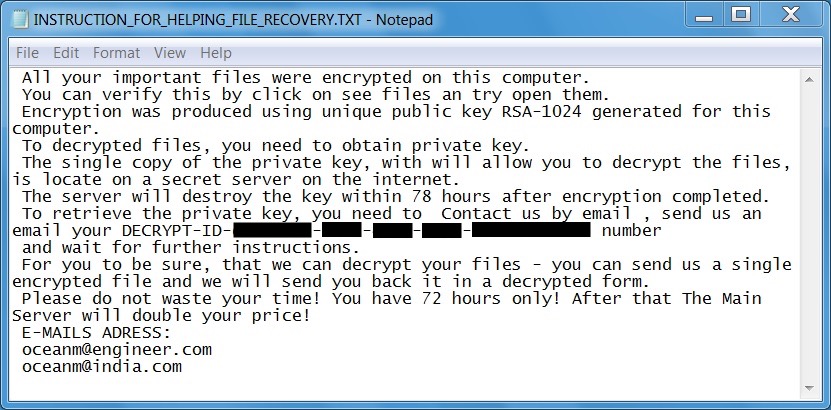
Shown above: Screen shot of the decryption instructions.
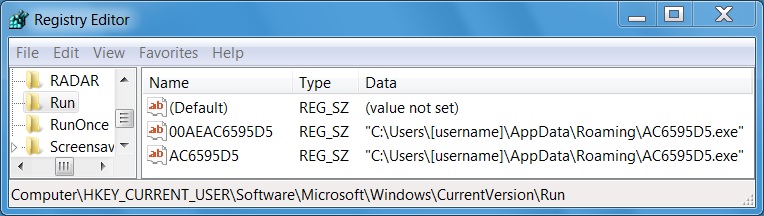
Shown above: Registry entries created for persistence.
There wasn't much on the post-infection traffic. The infected host merely retrieved a public key and provided a file count (for the encrypted files) during the ransomware callback. Characteristics of the ransomware binaries follow.
First example:
- SHA256 hash: e6591a9389c7b82d59949b8c5660e773b86dff1fa3909f780cb8c88bbc85646c
- File name: plugin-office.exe
- File size: 376,832 bytes
Second example:
- SHA256 hash: 5ca18c9f5ec26a30de429accf60fc08b0ef785810db173dd65c981a550010dde
- File name: pluginoffice.exe
- File size: 182,272 bytes
Post-infection callback by the ransomware:
- 212.47.254.187 port 80 - 212.47.254.187 - POST /scripts/superfish/js/supersubs.php
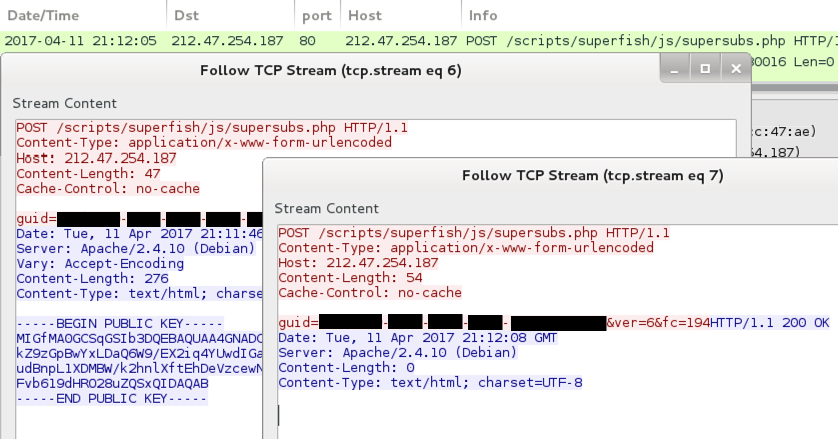
Shown above: Callback traffic from the pcap in Wireshark.
Final words
My final words today are similar to my final words for yesterday's diary on Dridex malspam.
As usual, humans are the weakest link in this type of infection chain. If people are determined to bypass all warnings, and their systems are configured to allow it, they will become infected. Unfortunately, that's too often the case. I don't believe the situation will improve any time soon, so we can expect these types of malspam campaigns to continue.
Emails, malware samples, and pcaps associated with the 2017-04-11 ransomware malspam can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net

Comments