"Blank Slate" malspam still pushing Cerber ransomware
2017-03-22 Update: This diary was posted earlier, but we had some technical issues, and the previous diary disappeared. I had to re-post this as a new diary with a new story ID and URL.
Introduction
Cerber ransomware has been a constant presence since it was first discovered in February 2016. Since then, I've seen it consistently pushed by exploit kits (like Rig and Magnitude) from the pseudoDarkleech and other campaigns. I've also been tracking Cerber on a daily basis from malicious spam (malspam).
Some malspam pushing Cerber is part of the "Blank Slate" campaign. Why call it Blank Slate? Because the emails have no message text, and there's nothing to indicate what, exactly, the attachments are. Subject lines and attachment names are vague and usually consist of random numbers.
An interesting aspect of this campaign is that the file attachments are double-zipped. There's a zip archive within the zip archive. Within that second zip archive, you'll find a malicious JavaScript (.js) file or a Microsoft Word document. These files are designed to infect a computer with ransomware.
Blank Slate has pushed different types of ransomware. However, the vast majority of ransomware from this campaign has been Cerber. I wrote an in-depth article about Blank Slate earlier this month, and it's changed very little since then.
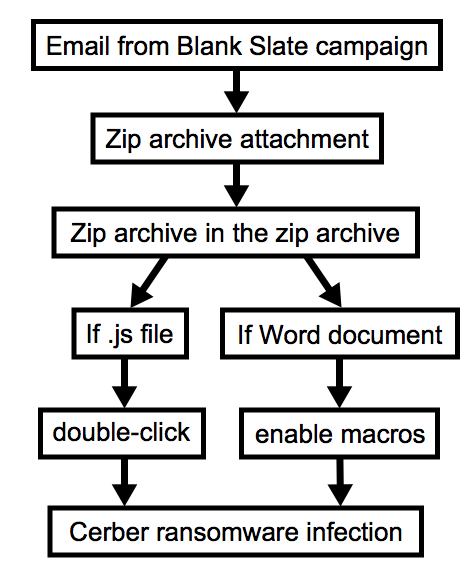
Shown above: Chain of events for a Blank Slate Cerber infection.
Let's look at some examples from Monday and Tuesday of this week (2017-03-20 and 2017-03-21).
The emails
Like other malspam campaigns, Blank Slate emails come from numerous hosts across the globe. I always think of this as botnet-based malspam, but I don't have any visibility on the sending side.

Shown above: Ten emails from this campaign on 2017-03-20 and 03-21.
Sending email addresses are always spoofed. The only reliable source data consists of IP addresses for sending mail servers, specifically the one that directly contacted the recipient's mail server, as noted in the email headers. Everything else in an email can probably be spoofed.
What does one of these emails look like? Below is a screen shot with the recipient's information redacted.

Shown above: An email from the Blank Slate campaign.
What's in the zip file attachment? Another zip file!
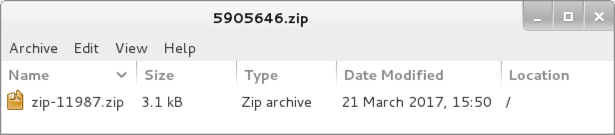
Shown above: Contents of the zip attachment from a Blank Slate campaign email.
What's in that zip within the zip? It's either a Microsoft Word document, or it's a .js file. In this case it's a .js file. I've seen many more .js files than Word documents in recent weeks from this campaign.
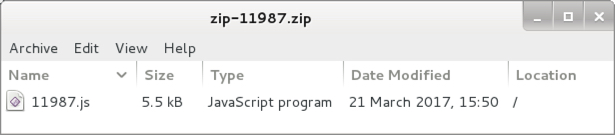
Shown above: Contents of the zip archive within the zip archive.
The .js file contains obfuscated script. If you double-click the file on a default-configured Windows host, Microsoft Windows Script (WScript) Host will execute the code and try to infect the computer.
Shown above: Start of obfuscated script in the .js file.
The traffic
On Monday 2017-03-20, I ran one of the extracted .js files on a vulnerable Windows host. After an initial HTTP GET request for the ransomware binary, post-infection traffic was similar to several other recent examples of Cerber. You'll see UDP traffic from the infected host over port 6892. That's followed by HTTP traffic to a domain starting with p27dokhpz2n7nvgr and ending with .top. IP addresses for the UDP traffic changes every week or two (or longer). Post-infection HTTP domains change more frequently.
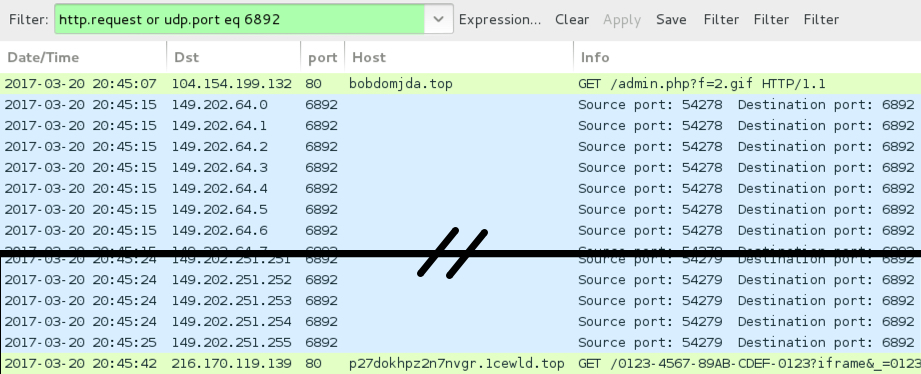
Shown above: Infection traffic from Monday 2017-03-20.
The infected Windows host acted similar to other hosts I've infected in previous months. Along with the desktop background, decryption instructions were dropped to the desktop in three different files. File names began with _READ_THIS_FILE_ and consisted of a text file, an image file, and an HTA file.

Shown above: An infected Windows host from Monday 2017-03-20.
The decryption process hasn't changed in recent months. Recently, whenever I've checked Cerber decryption instructions, the ransom was consistently $500 US dollars. The bitcoin amount had always reflected that $500 dollar value. But this week's example was different. This week, the ransom was 1 bitcoin.

Shown above: Cerber decryptor page with the ransom cost.
Indicators of Compromise (IoC)
The following IP is traffic generated by the extracted .js files that downloaded Cerber:
- 54.68.27.226 or 104.154.199.132 - sonicfopase.top - GET /admin.php?f=2.gif
- 54.68.27.226 or 104.154.199.132 - bobdomjda.top - GET /admin.php?f=2.gif
- 54.68.27.226 or 104.154.199.132 - dboosajqn.top - GET /user.php?f=2.gif
- 104.199.9.203 - letrockstadawsa.top - GET /search.php
- 104.199.9.203 - yunityreyrehol.top - GET /search.php
Post-infection Cerber traffic:
- 149.202.64.0 to 149.202.64.31 (149.202.64.0/27) UDP port 6892
- 149.202.122.0 to 149.202.122.31 (149.202.122.0/27) UDP port 6892
- 149.202.248.0 to 149.202.251.255 (149.202.248.0/22) UDP port 6892
- HTTP traffic to a domain starting with p27dokhpz2n7nvgr and ending with .top
Cerber samples collected using this batch of emails:
SHA256 hash: 92135e39f2e0db1aaf6605446e24fc9aedc36eb4bed9e7cdad1e92e4d387ed04
- File description: Cerber sample from bobdomjda.top on 2017-03-20
- File size: 264,378 bytes
SHA256 hash: 035d137592a7f6ce707739ceecb09db517587bcb0100254c3dd8ee4a262603af
- File description: Cerber sample from letrockstadawsa.top on 2017-03-20
- File size: 264,377 bytes
SHA256 hash: ee6b4e29aac7ca55a19265728d484221956b1b11c4961b60dd70137316bde245
- File description: Cerber sample from sonicfopase.top on 2017-03-20
- File size: 264,378 bytes
SHA256 hash: 0456237db4444582d94f4231824bdc09475d844820f14fcd2172ccdc13bddbf3
- File description: Cerber sample from dboosajqn.top on 2017-03-21
- File size: 273,618 bytes
SHA256 hash: d3a6ab8e8f6eb49cba032208d04d7105ac764982ca56fcaf1a421396e1adadfa
- File description: Cerber sample from yunityreyrehol.top on 2017-03-21
- File size: 273,617 bytes
Final words
I always wonder how effective campaigns like this are. Potential victims must open an attachment from a blank email, go through two zip archives, then double-click the final file. If the final file is a Word document, the victim must also enable macros.
And that works on default Windows configurations. But properly-administered Windows hosts and decent email filtering are enough, I think, to keep most people from worring about it. I'm far more interested in the cycle of abuse targeting hosting providers. Without web servers to host ransomware binaries, Blank Slate cannot continue its current method of operations.
For more details on Blank Slate, see my previous writeup about it. Pcap and malware samples for this ISC diary can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments