SSH Honeypots (Ab)used as Proxy
$ ssh -L 8443:192.168.254.10:443 user@192.168.254.2
$ ssh -D 8080 user@192.168.254.10
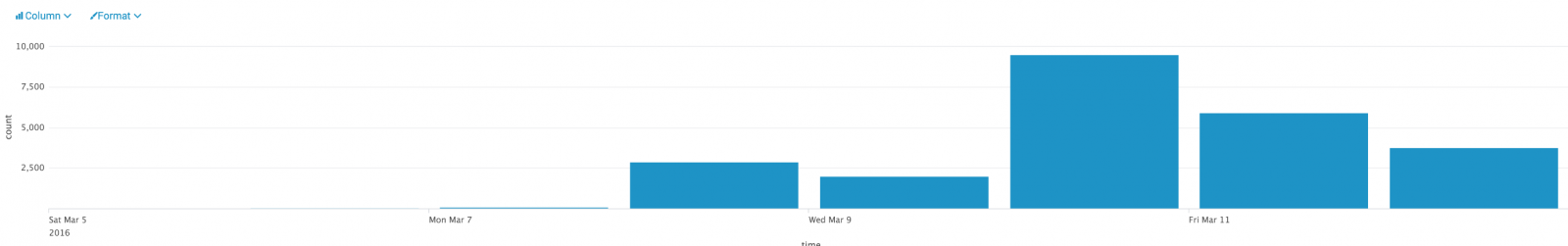
| Event | Hits |
| cowrie.direct-tcp.request | 24242 |
| cowrie.direct-tcp.data | 22967 |
| cowrie.log.open | 15130 |
| cowrie.log.closed | 14679 |
| cowrie.session.connect | 13882 |
| cowrie.session.closed | 13877 |
| cowrie.command.success | 11563 |
| cowrie.client.version | 9019 |
| cowrie.login.success | 8652 |
| cowrie.command.failed | 3948 |
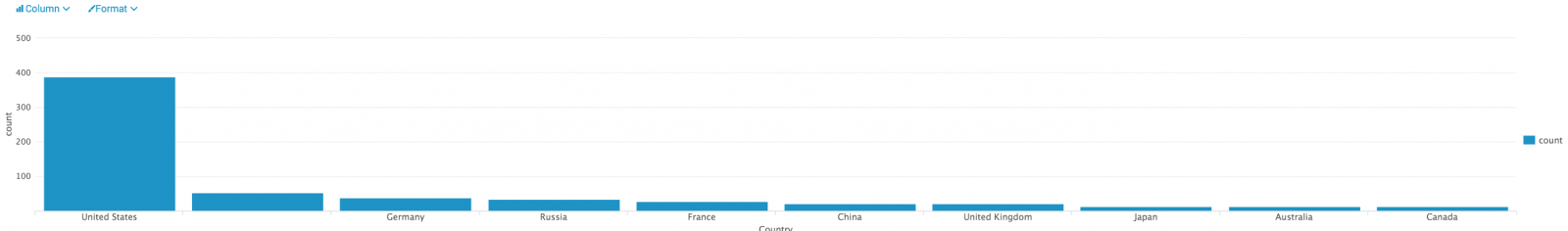
| Country | Hits |
| Germany | 22405 |
| Russia | 1295 |
| United States | 267 |
| Argentina | 76 |
| France | 51 |
| Switzerland | 35 |
| Netherlands | 26 |
| Ukraine | 20 |
| India | 16 |
| Iran | 16 |
| TCP Ports | Hits |
| 80 | 31431 |
| 25 | 1428 |
| 587 | 383 |
| 443 | 271 |
| 465 | 160 |
| 110 | 30 |
| 143 | 13 |
| 1101 | 4 |
| 1102 | 4 |
| 89 | 1 |
If we analyze the relations between the honeypots, sources and destinations, we see that some destinations (blue) were targeted by more than one attacker (green) connected on different honeypots (red):
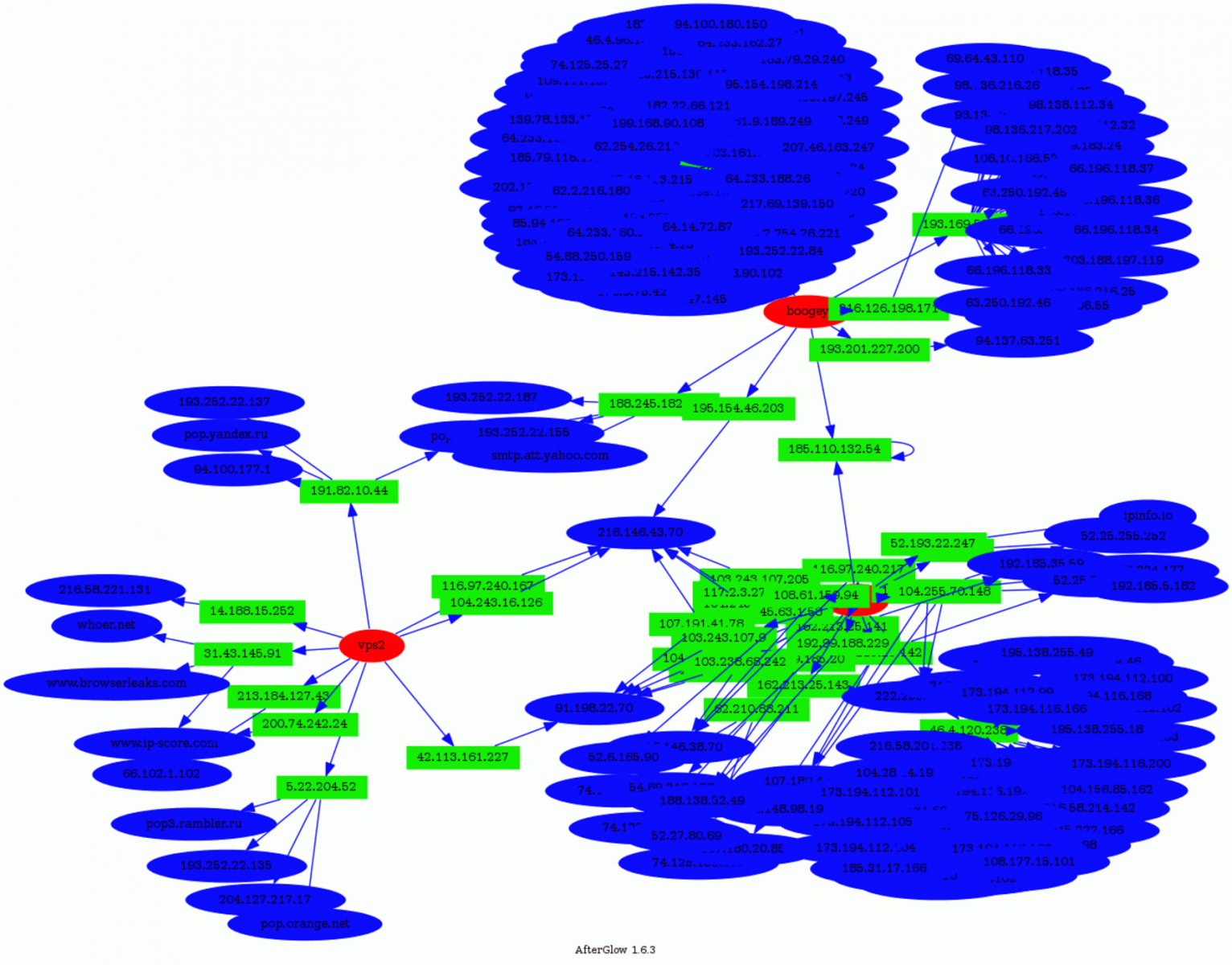
- www.google-analytics.com
- tags.tagcade.com (an ads tag management system)
Some people trying to abuse those services? Feel free to share your findings if you also detected such kind of activity!
To conclude: attackers are not only scanning the Internet to find vulnerable hosts and turn them in bots. They are also looking for ways to hide themselves to perform (maybe) more complex or dangerous attacks.
And keep in mind that if you allow users to SSH to systems that can access the Internet, they can be used as a solution to bypass classic controls in place!
Xavier Mertens
ISC Handler - Freelance Security Consultant
PGP Key
A Look at the Mandiant M-Trends 2016 Report
Mandiant released their 2016 threat reports last month and highlighted some interesting trends: more breaches were made public and location and motive of attackers were more diversified. Handlers have posted over the past week diaries on various threats; attempt to exploit MacOS [2], fishing campaigns [3] and exploit kits [4] to name a few which in a way isn't really anything new. The attacks are now more in your "face" and going after the mainstream applications, encrypting files for money and mobile devices.
The report also contains some interesting statistics, "The median number of days an organization was compromised in 2015 before the organization discovered the breach (or was notified about the breach) was 146."[1] That is a long time, that is almost 5 months before a breach is discover. One of the new trends has been an increase in user held to ransom with critical files encrypted with Cryptolocker [5], loss of personal information or the exploit of network gears [6].
The report ends with an upbeat tone where it highlight the fact that security teams are getting better at detecting and combating attacks by malicious actors. The median time to detect system compromised has been steadily declining, however, there is still have a lot of work to do to detect and remediate the attack much sooner. What do you think a reasonable time should be? Hours, days, or less than a month.
[1] https://www2.fireeye.com/rs/848-DID-242/images/Mtrends2016.pdf
[2] https://isc.sans.edu/forums/diary/OSX+Ransomware+Spread+via+a+Rogue+BitTorrent+Client
[3] https://isc.sans.edu/forums/diary/Paypal+Phishing+landing+pages+hosted+at+HostGator/20803/
[4] https://isc.sans.edu/forums/diary/Recent+example+of+KaiXin+exploit+kit/20827/+Installer/20811/
[5] https://isc.sans.edu/forums/diary/Do+Extortionists+Get+Paid/20223
[6] https://isc.sans.edu/forums/diary/Port+32764+Router+Backdoor+is+Back+or+was+it+ever+gone/18009
-----------
Guy Bruneau IPSS Inc.
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu

Comments