Gameover Zeus reported as "returned from the dead"
As reported by Sophos and submitted by multiple ISC readers (thank you), Gameover Zeus is resurfacing.
According to the Sophos post, they have "only seen a few samples of the new version, but it has been distributed through widespread spam campaigns, so the number of infections may already be large. Typical Gameover spams include an attachment pretending to be an account statement."
Malcovery has a related post for your review as does StopMalvertising.
If you spot what you belief are related SPAM samples or actual binaries, please send them our way for analysis.
Keeping the RATs out: **it happens - Part 2
As we learned in Part One of our exploration of Hazrat Supply's series of unfortunate events, our malicious miscreants favored multiple tools. We first discussed developing IOCs for HackTool:Win32/Zeloxat.A which opens a convenient backdoor on a pwned host. One note on that front, during analysis I saw network calls to zeroplace.cn (no need to visit, just trust me) and therefore added matching URI and DNS items to the IOC file. Again, I'll share them all completed for you in a day or two.
I know I promised you an analysis of the svchost dump file Jake provided using Volatility but unfortunately that effort did not bear much fruit; the imagecopy module didn't return actionable results. The actual svchost.exe sample is still an analysis work-in-progress as well given, while certainly malicious, the file we have was not an original payload and is exhibiting limited functionality. I do hope to have insight on that front tomorrow.
That said, one of the other tools that was found on the server by Jake was PWDump7. This is a commonly used tool and is often part of larger hacker or pentester kits; you should be detecting and blocking them both equally :-).
By definition, PwDump7.exe is not malware per se, it's simply a tool that can be used for malicious purposes. It doesn't make file system changes, it doesn't phone home, it doesn't change the registry, but it sure does dump password hashes as seen in Figure 1.
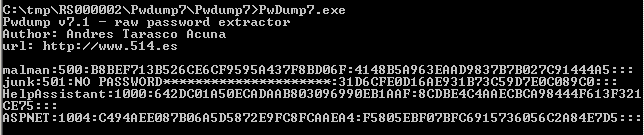
Figure 1
The first reader who emails me (russ @ holisticinfosec dot org) my clear text password from the 500 hash as seen in Figure 1 wins a prize of my choosing (probably shwag or a book), I'll Tweet out the winner. *UPDATE* - We have a winner as of 0146 PST last night, thank you, Martin R. The password for you all is IveBeenHacked.
In the absence of particularly interesting artifacts, can we still create IOCs for hack tools such as PwDump?
But of course!
File name, file size, and hashes are obvious, but what else can we use when so little presents itself with a hack tool that is standalone and basically just runs?
Tools such as PEStudio can give us additional options if we look beyond the obvious. PEStudio, by default, will sort by color coded (red), flagged items. Often this presents some obvious enough indicators but with PwDump7, not so much. But sorting by something different such as Value under Strings and Unclassified gives us a perfectly unique indicator not likely to occur very often, particularly in the context of established file name and hashes. Figure 2 exemplifies.
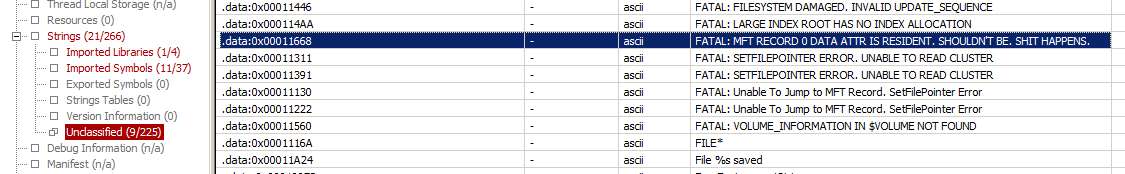
Figure 2
As such, our IOC elements would be derived as seen in Figure 3.
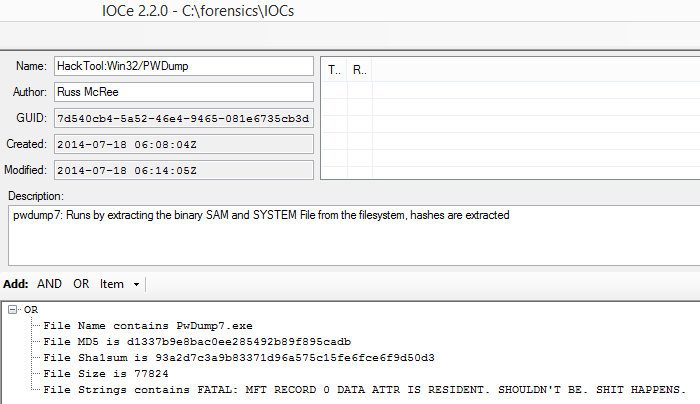
Figure 3
Can't miss with strings keywords like that. :-)
I'll leave you with this. As we've been learning from the kind transparency of Jake and Hazrat Supply, **it happens, it really does.
Just another reason not to tailgate.
Cheers!


Comments