TCP/5000 - The OTHER UPNP Port
We've all read a lot about the scans and exploits of UPNP (Universal Plug N Play), on UDP port 1900. Jens, one of our readers, pinged us this morning with a question about an uptick he was seeing in TCP/5000, which is also listed as UPNP - who knew? (not me, that's who!)
After a quick check, I'm seeing an uptick in attack activity on TCP/5000 starting in mid-February, both in our dshield database and on various customer firewalls. Our reader was seeing his attacks come from an IP allocated to China, but I'm seeing more attacks sourced from the US.
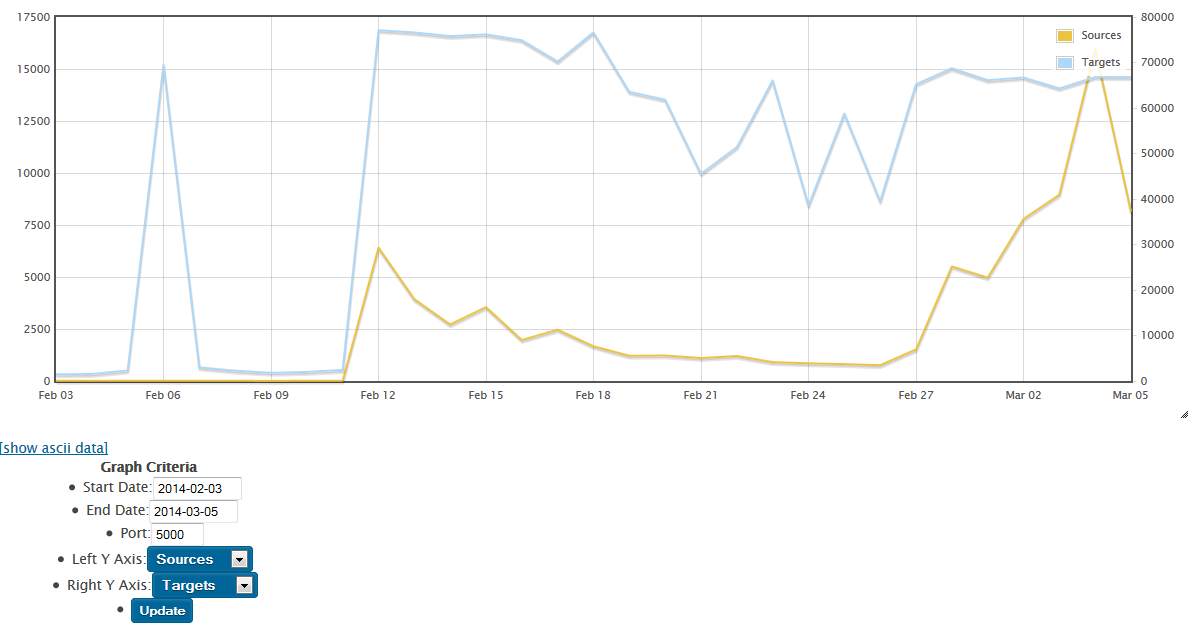
Does anyone have any of these attack packets captured, preferably more than just SYN packets?
Or if anyone has a sample of the attack software or any malware involved, we'd of course love a sample of that as well !
===============
Rob VandenBrink
Metafore
Mitigation Fail for Gas Pump Skimmers
In late January we all heard about bluetooth enabled credit card skimmers on gas pumps. Since that story broke, I've been seeing some attempts at reassuring the public on this issue - I'm seeing pumps at multiple chains having their card readers taped and initialed.

I suppose they figure crooks don't have red tape, or pens. This really is more to reassure consumers, to say "yes, we do check these once in a while to make sure that your card isn't being skimmed". Though that assumes the person checking can tell a reader cover from a skimmer.
I was surprised also to find that this "breaking story" on skimmers which hit the news in January 2014 was first posted by Brian Krebbs way back in 2010 -
http://krebsonsecurity.com/2010/07/skimmers-siphoning-card-data-at-the-pump/
http://krebsonsecurity.com/all-about-skimmers/
... but by the time my brain caught up with who's page I found this on, I wasn't surprised at all.
The main protection we have against skimmers is the moral fortitude of the attendant working at the station. We're depending on that person doing the right thing when faced with a choice between a potentially very large bribe. Skimmer operations can easily net tens of thousands per week, or millions in this recent case https://krebsonsecurity.com/2014/01/gang-rigged-pumps-with-bluetooth-skimmers/. So the risk / reward proposition is a large bribe, often in the tens-of-thousands range, against being aprehended and charged/convicted if the operation is caught and apprehended before they shut down and move on to the next set of target gas stations.
Please, weigh in using our comment form. I'd be really interested if our readers might have solutions or preventitive measures that will work better than the red tape I described in this story!
==============
Rob VandenBrink
Metafore


Comments