NTP reflection attacks continue
Chris Mohan --- Internet Storm Center Handler on Duty
Scanning for Symantec Endpoint Manager
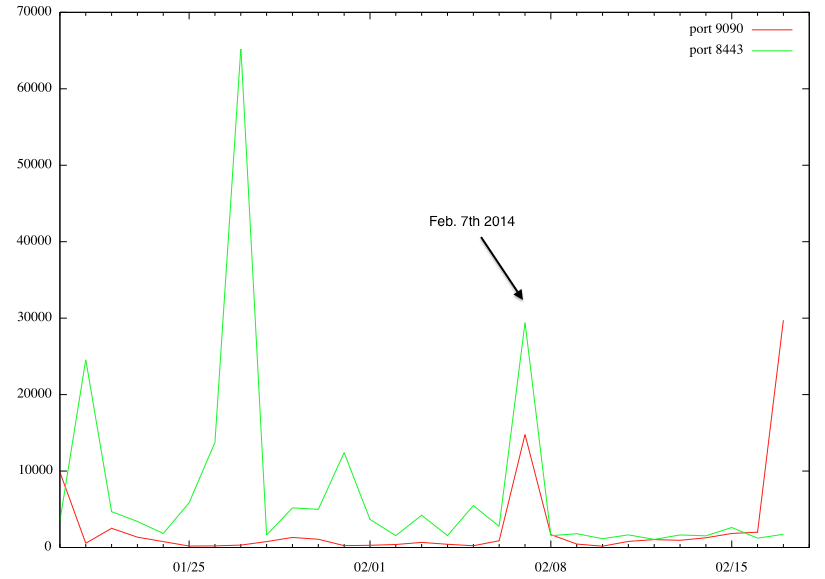
Last week, we mentioned a new vulnerability in Symantec Endpoint Protection Management [1]. According to Symantec's advisory, this product listens on port 9090 and 8443/TCP. Both ports are scanned regularly for various vulnerabilities, in particular 8443, being that it is frequently used by web servers as an alternative to 443. However, on February 7th, we detected a notable increase in scans for both ports.
(click on image for larger version)
Interestingly, it looks like two different IP addresses caused this increase, scanning for one port only each.
217.174.250.228 is the "heavy hitter" for port 8443, and 125.217.252.183 for port 9090. There is no organizational connection between the two IPs based on Whois.
125.217.252.183 is assigned to a University in China (the whois record contains a bit a weird looking "description": ~{;*DO@m9$4sQ'~} ).
217.174.250.228 is assigned to a british hosting company.
My assumption is that both hosts were compromised at the time.
Today, we are also seeing a large increase in scanning for port 9090, pointing to someone building a target list of vulnerable systems. Pretty much the only source scanning today is 113.010.155.079. This address is interesting in that it is not assigned according to APNIC (the RIR in charge of this address), but it does respond to pings. It runs a phpmyadmin website as default host, which pretty much guarantees that it is a compromised system (could actually also be a honeypot).
[1] http://www.symantec.com/docs/TECH214866
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter

Comments