Are Mobile Devices taking over your Corporate Network?
Last week I read an interesting article stating the PC is no longer the office primary device for accessing the Internet. With the influx of mobile devices into the enterprise, it is becoming more difficult to enforce corporate policies that are centrally managed. A recent survey by McAfee across "[...] 14 nations show 21% of companies have no restrictions on use of personal mobile devices, while 58% have lightweight policies, and only 20% have stringent guidelines.[2]" Each of these devices have different OS, software installed and ways of securing them (or none at all). If these devices aren't centrally controlled and have access to everything in the enterprise, it will become a "gold mine" for those looking for an easy to pick "low hanging fruit".
A recent study indicates that "Mobile internet traffic is set to grow 400% by 2015"[3] and the bulk will be in video consumption. Wireless carriers are starting to offer Long Term Evolution (LTE) devices (i.e. rocket stick) that are potentially capable of supporting speed up to 75 Mbps, crown jewels (i.e. source code) can be transferred quickly out of a corporate network. For example, Google Android and the Apple iOS [4] have already been targeted by cyberthieves. Government agencies are starting to provide hardening guide; for example, Australia's DSD just released a guide to harden the iOS 4 devices [5]. Incident Response will also become more complex if a mobile device has been compromised and is not owned by the enterprise. I can see Network Forensics becoming a crucial tool to aid reconstructing the events that lead to an incident.
Last year ISC posted a survey on "What is your biggest fear with Mobile Devices in your enterprise?"[6] and almost 50% of the respondent answered "Monitoring for information leak" followed with about 20% having issues with "Wireless access".If you don’t mind sharing, we would like to hear from you our readers, how your organization is currently dealing with Mobile Devices.
[1] http://www.networkworld.com/newsletters/sec/2011/070411sec1.html
[2] http://www.usatoday.com/money/workplace/2011-05-30-mobile-devices-in-the-workplace_n.htm
[3] http://econsultancy.com/us/blog/5683-study-mobile-internet-traffic-is-set-to-grow-400-by-2015
[4] http://isc.sans.edu/diary.html?storyid=11185
[5] http://www.dsd.gov.au/publications/iOS_Hardening_Guide.pdf
[6] http://isc.sans.org/poll.html?pollid=301&results=Y
[7] http://next-generation-communications.tmcnet.com/topics/nextgen-voice/articles/195439-rogers-brings-canadas-first-lte-network-ottawa.htm
[8] http://gigaom.com/mobile/verizons-lte-network-getting-10-devices-by-june/
-----------
Guy Bruneau IPSS Inc. gbruneau at isc dot sans dot edu
Community SANS SEC 503 coming to Ottawa Sep 2011
New Sguil HTTPRY Agent
I have tested a new Sguil agent released by Paul Halliday [1] last month to collect and store http traffic session into the Sguil database for web traffic analysis. If you are looking for a method to collect and mine web traffic session, this new agent is your tool. Here is an example how the httpry agent collects its log:
2011-07-13 00:36:47 192.168.48.138 50108 72.14.204.121 80 GET www.pintumbler.org /Code/dnsbl http://www.pintumbler.org/Code/hafs Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; WOW64; Trident/5.0)
2011-07-13 00:36:48 192.168.48.138 50108 72.14.204.121 80 GET www.pintumbler.org /_/rsrc/1303426214049/Code/dnsbl/dnsbh1.png http://www.pintumbler.org/Code/dnsbl Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; WOW64; Trident/5.0)
2011-07-13 00:36:48 192.168.48.138 50227 72.14.204.121 80 GET www.pintumbler.org /_/rsrc/1303426235351/Code/dnsbl/dnsbh2.png http://www.pintumbler.org/Code/dnsbl Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; WOW64; Trident/5.0)
2011-07-13 00:36:48 192.168.48.138 50228 72.14.204.121 80 GET www.pintumbler.org /_/rsrc/1303426262027/Code/dnsbl/dnsbh3.png http://www.pintumbler.org/Code/dnsbl Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; WOW64; Trident/5.0)
This Sguil client snapshot shows the traffic collected by the agent on a client and displayed in the order the web sites were accessed. Like other traffic collected by the Sguil framework, this traffic can request the packets to be analyzed with Wireshark.
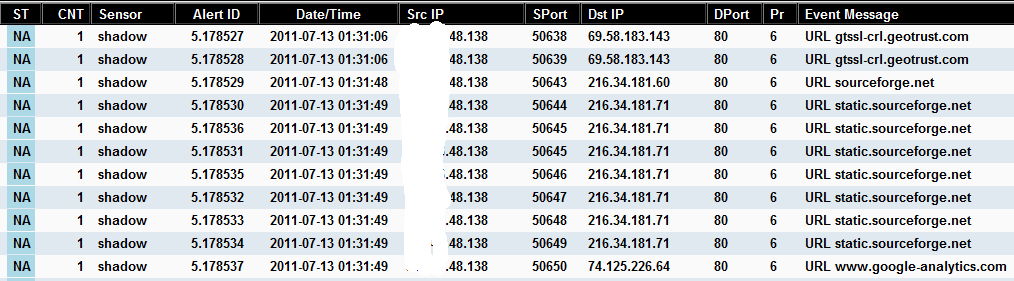
Follow Paul's instructions [2] on how to install and configured the agent to have the traffic report to the Sguil database. I would also suggest to run a cronjob to rotate the httpry service once per day to empty the logfile, otherwise it will grow exponentially and the agent will stop processing. Consider adding sites you consider of no value to the /etc/ httpry_agent.exclude file to carefully select what you insert in your database.
[1] http://www.pintumbler.org/Code/hafs
[2] https://github.com/int13h/httpry_agent/blob/master/README.md
[3] http://isc.sans.org/diary.html?storyid=9295
-----------
Guy Bruneau IPSS Inc. gbruneau at isc dot sans dot edu
Community SANS SEC 503 coming to Ottawa Sep 2011

Comments