Special SANSFIRE 2009 Podcast Presentations - State of the Internet Panel
Our third presentation is by all of the Internet Storm Center Handlers that were present (at the time) at SANSFIRE 2009. This is our annual "State of the Internet Panel" presentation.
I would suggest the way to get these podcasts is through iTunes (if you have iTunes) if not, then you can use whatever method works best for you and follow this link:
http://isc.sans.org/podcast.xml
In order to subscribe through iTunes click here:
There are no slides for this presentation.
-- Joel Esler | http://www.joelesler.net | http://twitter.com/joelesler
Michael Jackson Spam Distributes Malware
As we anticipated in our yesterday's diary, spammers are starting to exploit attention-grabbing headlines of recent celebrity deaths. Sophos described one such message, with the subject "Confidential===Michael Jackson", in their blog posting. Today we're starting to see reports of these messages directing viduals to websites that distribute malicious software.
For example, Steve Basford emailed us a link to his blog posting, where he discusses a spammed fake news item invites the victim to download a "video" to download. The message said: "As redes de televisão americanas CBS e ABC também estão noticiando a morte do cantor, assim como a versão online do jornal New York Times e da revista Variety..." (See screen shot below.)
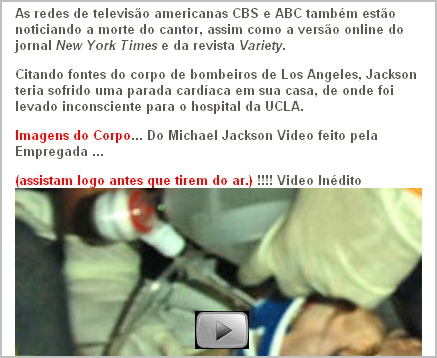
Liked this note? Tweet it!
-- Lenny
Lenny Zeltser - Security Consulting
Lenny teaches malware analysis at SANS Institute. You're welcome to follow him on Twitter. You can also track new Internet Storm Center diaries by following ISC on Twitter.
How Malware Defends Itself Using TLS Callback Functions
Malware authors employ numerous and creative techniques to protect their executables from reverse-engineering. The arsenal includes an anti-debugging technique called TLS callback. The approach is not new, yet it is not widely understood by malware analysts, so I'd like to describe in this note. (Thanks to Christian Wojner from CERt.at for his insights regarding this topic!)
What is TLS?
According to Microsoft, Thread Local Storage (TLS) is a mechanism that allows Microsoft Windows to define data objects that are not automatic (stack) variables, yet are "local to each individual thread that runs the code. Thus, each thread can maintain a different value for a variable declared by using TLS." This information is stored in the PE header. (Windows uses the PE header to store meta information about the executable to load and run the progrem.)
A programmer can define TLS callback functions, which were designed mainly to initialize and clear TLS data objects. From the malware author's perspective, the beauty of TLS callbacks is that Windows executes these functions before execuding code at the traditional start of the program.
How Can TLS Callbacks Confuse Debuggers and Analysts?
Analysts often examine the a malicious program's code by starting with the instructions located at the Entry Point of the executable. The Entry Point is a field in the PE header that stores the address of the "first" instruction in the program that Windows is supposed to execute; debuggers typically take us to that instruction after loading the executable. TLS callback functions allow malware authors to execute malicious code before the debugger has a chance to pause at the traditional Entry Point. This allows malware to infect the system or disable the debugger before the analyst has a chance to look at the sample's code.
Consider the TLS callback technique employed by the Nadnadzzz bot about a year ago. If you load the bot's executable into OllyDbg, you expect to have the debugger pause at its entry point. Instead, OllyDbg seems to immediately say that the process terminated. What happened? You just infected yourself!
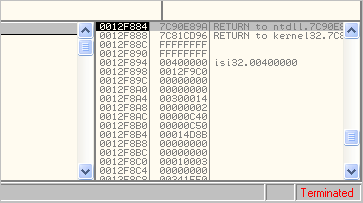
The problem is that before OllyDbg had a chance to pause at the traditional Entry Point instruction, it executed a TLS callback function.
How to Bypass the TLS Callback Defense
To bypass the TLS callback defense to debug the program starting from its "true" beginning of the TLS callback function:
- Configure the debugger to pause on the system entry point, instead of the traditional program entry point.
- Identify the address of the TLS callback function, instead of the traditional program Entry Point.
- Set the breakpoint on the TLS callback function, then run the program if you wish.
If using OllyDbg, you can tell it to pause before TLS callback by going to Debugging options > Events. By default, it's set to pause at "WinMain (if location is known)." Instead, set it to pause at "System breakpoint." This will allow you to control the program before TLS callback functions execute.
.png)
Now you will have a chance to set the breakpoint on the TLS callback function. You need to find it first, though. Ilfak Guilfanov describes a convenient way to do that with IDA Pro in his blog posting. To locate the TLS callback function, load the malicious executable into IDA Pro, then press Ctrl+E to view the executable's entry points. The address of the TLS callback function should be among them.
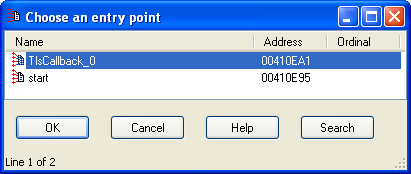
Now you know where to start debugging or otherwise analyzing the program's code. You can do this in IDA Pro. If you prefer OllyDbg, you can return to OllyDbg, and load the malicious program; OllyDbg will now pause at the "system entry point" in ntdll.dll. Press Ctrl+G and enter the address of the TLS callback function, which you located via IDA Pro; set a breakpoint there and continue the analysis.


For additional information about TLS callbacks used by malware for anti-debugging, see the links mentioned earlier, as well as:
- Manually create a Tread Local Storage (TLS) Callback
- How to execute code during an application's initialization
- TLS as used in Backlight
Update:
Sylvain Sarmejeanne reminded us that GRUM malware used TLS callback to execute its unpacking code, as outlined in this Websense blog posting. Sylvain also shared with us a link to his personal blog posting (in French), which explains how one could use TLS callbacks to create a UPX-packed file that runs differently depending on whether was statically uncompressed ("upx -d") or whether it dynamically uncompresses itself in memory. (Here's a link to the Google auto-translate of Sylvain's posting.)
If you have other tips and examples of TLS callbacks used by malware, please let us know.
Liked this note? Tweet it!
-- Lenny
Lenny Zeltser - Security Consulting
Lenny teaches malware analysis at SANS Institute. You're welcome to follow him on Twitter. You can also track new Internet Storm Center diaries by following ISC on Twitter.
PHPMYADMIN scans
We have received some reports (thanks Drew) of scanning for keyhandler.js which is part of PHPMyAdmin. The PHPmyAdmin site does not specifically mention this script. Scans look as follows:
aa.zzz.qqq.119 - - [24/Jun/2009:08:37:19 -1000] "GET HTTP/1.1 HTTP/1.1" 400 26 "-" "Toata dragostea mea pentru diavola"
aa.zzz.qqq.119 - - [24/Jun/2009:08:37:19 -1000] "GET /admin/js/keyhandler.js HTTP/1.1" 404 26 "-" "Toata dragostea mea pentru diavola"
aa.zzz.qqq.119 - - [24/Jun/2009:08:37:20 -1000] "GET /admin/pma/js/keyhandler.js HTTP/1.1" 404 26 "-" "Toata dragostea mea pentru diavola"
aa.zzz.qqq.119 - - [24/Jun/2009:08:37:21 -1000] "GET /admin/phpmyadmin/js/keyhandler.js HTTP/1.1" 404 26 "-" "Toata dragostea mea pentru diavola"
aa.zzz.qqq.119 - - [24/Jun/2009:08:37:21 -1000] "GET /db/js/keyhandler.js HTTP/1.1" 404 26 "-" "Toata dragostea mea pentru diavola"
aa.zzz.qqq.119 - - [24/Jun/2009:08:37:22 -1000] "GET /dbadmin/js/keyhandler.js HTTP/1.1" 404 26 "-" "Toata dragostea mea pentru diavola"
aa.zzz.qqq.119 - - [24/Jun/2009:08:37:22 -1000] "GET /myadmin/js/keyhandler.js HTTP/1.1" 404 26 "-" "Toata dragostea mea pentru diavola"
aa.zzz.qqq.119 - - [24/Jun/2009:08:37:23 -1000] "GET /mysql/js/keyhandler.js HTTP/1.1" 404 26 "-" "Toata dragostea mea pentru diavola"
aa.zzz.qqq.119 - - [24/Jun/2009:08:37:23 -1000] "GET /mysqladmin/js/keyhandler.js HTTP/1.1" 404 26 "-" "Toata dragostea mea pentru diavola"
aa.zzz.qqq.119 - - [24/Jun/2009:08:37:24 -1000] "GET /typo3/phpmyadmin/js/keyhandler.js HTTP/1.1" 404 26 "-" "Toata dragostea mea pentru diavola"
aa.zzz.qqq.119 - - [24/Jun/2009:08:37:24 -1000] "GET /phpadmin/js/keyhandler.js HTTP/1.1" 404 26 "-" "Toata dragostea mea pentru diavola"
aa.zzz.qqq.119 - - [24/Jun/2009:08:37:24 -1000] "GET /phpmyadmin/js/keyhandler.js HTTP/1.1" 404 26 "-" "Toata dragostea mea pentru diavola"
aa.zzz.qqq.119 - - [24/Jun/2009:08:37:25 -1000] "GET /phpMyAdmin/js/keyhandler.js HTTP/1.1" 404 26 "-" "Toata dragostea mea pentru diavola"
aa.zzz.qqq.119 - - [24/Jun/2009:08:37:25 -1000] "GET /phpmyadmin1/js/keyhandler.js HTTP/1.1" 404 26 "-" "Toata dragostea mea pentru diavola"
aa.zzz.qqq.119 - - [24/Jun/2009:08:37:26 -1000] "GET /phpmyadmin2/js/keyhandler.js HTTP/1.1" 404 26 "-" "Toata dragostea mea pentru diavola"
aa.zzz.qqq.119 - - [24/Jun/2009:08:37:26 -1000] "GET /pma/js/keyhandler.js HTTP/1.1" 404 26 "-" "Toata dragostea mea pentru diavola"
aa.zzz.qqq.119 - - [24/Jun/2009:08:37:27 -1000] "GET /web/phpMyAdmin/js/keyhandler.js HTTP/1.1" 404 26 "-" "Toata dragostea mea pentru diavola"
Modsecurity or suhosin should help you out keeping this away from your installation. PHPMyadmin should probably only be available from the internal network or limited external sources. So for most of you this shouldn't be an issue. If you do have some captures of what happens when there is a compromise, please use the contact form to let us know.
Mark H - Shearwater

Comments