Next-generation Web browsers?
A couple of weeks ago I was presenting at the III OWASP Spain Chapter Meeting about "Web security threats and incidents" (presentation in Spanish). I tried to emphasize one of the (if not THE) biggest security threats nowadays: Web-based attacks. Everybody runs at least an operating system, a mail reader (except for Web mail, so even this one is optional) and a Web browser; conclusion: the attackers are focused on breaking into computers through out the latter.
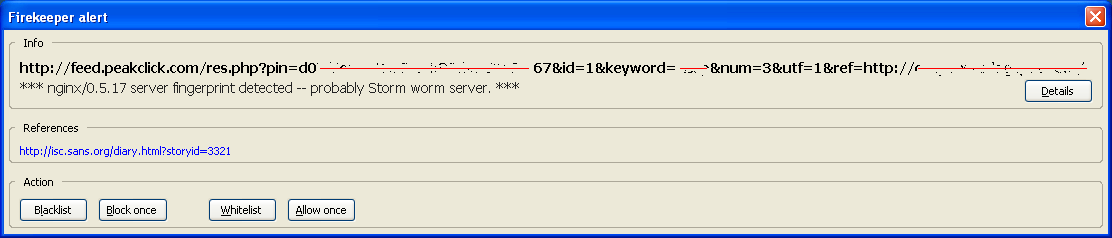
A few days after the conference, Jesus (who attended the meeting) wrote me in commenting about a specific case he saw when browsing what seemed to be a legitimate site. After browsing to the site, the main page contained an ads-related script tag loading ads contents from "feed.peakclick.com", specifically from "res.php" with some additional parameters like the subscriber id, keyword, and referrer:
<script>hxxp://feed.peakclick.com/res.php?pin=d0..67&id=1&keyword=isc&num=3
&utf=1&ref=hxxp://original_site</script>
At this point is when the user could get suspicious if he is using the Firekeeper Firefox extension, as it generates an alert:
Although Web-based malware is extremely common nowadays, as the alert signature referenced us (the ISC) directly, I decided to research it in-depth. Unfortunately (from a research perspective), it was a false positive and there was no malicious content loaded from peakclick. The script simply loads an ad and includes links to the company being announced. If the user click on these links, he can reach to the final ad content after five HTTP redirections (302 Found responses).
The alert is generated because there is a Firekeeper experimental rule that matches if any of the HTTP headers contain the string "nginx/0.5.17". This server string corresponds to the Engine X small Web server, widely used for malware distribution and the Storm Worm. However, the existence of this server does not directly mean malicious content, as in this case.
Although the signature is too generic, the idea behind the Firekeeper tool (we mentioned it a year ago) is great, as it provides IDS/IPS capabilities where they are required today, at the browser level, after decompression and decryption (https) have been applied. The tool is based on rules (similar to Snort), although it only implements a small set at this point. Unfortunately, the latest version, 0.2.14 (October 2007), is still in alpha status and somehow not very active.
Definitely, we need more tools like this one in order to enforce advanced security policies at the Web browser level (not talking about Web privacy or anti-phising toolbars). I guess we will start to see some compartmentalization built-in inside the browsers soon, trying to stop very common attacks such as CSRF (Cross-Site Request Forgery). Some Web browsing recommendations (some of them previously mentioned at the ISC) are:
- Run the latest Web browser version and apply all available security patches and updates.
- Secure your Web browser (US-CERT) and tweak the browser security settings.
- Increase the security stance of the browser using IE Zones (for Internet Explorer) or add-ons on Firefox, such as NoScript. Additionally, there are multiple ways of stopping Web scripts at the infrastructure (from a previous ISC post).
- Run the Web browser with a non-privileged user different from the one you run your OS session with, trusting OS filesystem ACLs. I'm assuming you are not running as Administrator / root, are you? :)
- Use two Web browsers: one just for critical access, and a different one for casual Web browsing.
- Run the Web browser inside an "isolated" environment (sandbox), such as SandboxIE, or with minimum privileges, using DropMyRights.
- Run the Web browser in a virtual machine, custom-made or a public one, such as the VMware Browser Appliance (Ubuntu + Firefox).
- Use more advanced add-ons, such as Firekeeper (still alpha), FlashBlock or Adblock (there are hundreds).
- Or a combination of some of the above...
Unfortunately, some of these recommendations only apply to the security or IT professional and cannot be applied yet to end users. We need to increase the usability of some of the currently available options for widespread usage. It is time for the next-generation Web browsers!
Happy and safe Web browsing! If you have other tips & tricks for safe Web browsing, let us know, and I'll update this post.
--
Raul Siles
www.raulsiles.com
UPDATE: Dave wrote in (thanks!) to mention a MS tool called MakeMeAdmin. As I denoted above, my post works under the assumption that you are using a regular user and running only specific tasks as Administrator (Windows) or root (Unix/Linux) using "RunAs" or "sudo" respectively. Sometimes you need to perform several high privilege tasks (or overcome some OS restrictions) and use "RunAs" to run explorer.exe or "su".
The main drawback of "RunAs" exists when you need to access network resources with a domain account, or you need to use settings from your (regular) profile. This is where MakeMeAdmin is extremely useful and provides you a command prompt with Administrator rigths (very similar to a Unix/Linux "su" command).
Overview of cyber attacks against Tibetan communities
On Friday we reported on targeted attacks against various pro-Tibet non-gouvernmental organizations (NGO) and communities, as well as Falun Gong and the Uyghurs. In this somewhat long diary entry, I’ll break down those attacks and identify the things we’ve seen in working on these since early 2007.
This hopefully helps you identify the risk similar attacks would pose to your organization. The diary does not deal with one incident, but looks at overall findings.
1. The message
The sole goal of the message is to transport the exploit, and to convince the reader to click on it, so the malicious code can execute.
Several social engineering tricks have been seen:
- Messages make a strong statement on a well known individual or group, but do not mention its name. The attachment is then named after that individual. A state of 'cognitive dissonance' arises between the reader's pre-existent beliefs and the statement. This urges the reader to click the message;
- The writing style of the purported sender is well researched and mimicked;
- The content of the document matches the topic of the e-mail message;
- Legitimate, trusted, users are sometimes convinced to actually forward along a message back to specific targets;
- In a number of cases, “memes” distributed within the community have been reused. For instance, in a “viral” Word document was grabbed from a forum, edited to include the exploit and Trojan code, and forwarded onto other members of the community.
Here’s a sample. This message was sent to someone very active within the Tibetan community, and was spoofed as originating from the Secretary of International Relations of the Central Tibetan Administration, the government in exile in Dharamshala, India. The name and contact details of the official were accurate:
All,
Attached here is the update Human Rights Report on Tibet issued by
Department of State of U.S.A on March 11, 2008.
You may also visit the site:
Tashi Deleg,
Sonam Dagpo
Secretary of International Relations
Department of Information & International Relations
Central Tibetan Administration
Dharamshala -176215
H.P., INDIA
Ph.: [obfuscated]
Fax: [obfuscated]
E-mail: [obfuscated]@gov.tibet.net or diir-pa@gov.tibet.net
Website: http://www.tibet.net/en/diir/
In some cases, messages were sent which addressed the recipient by his first name, and provided “clarification on a topic” which had previously been discussed between the sender and the recipient. While not evidence, there are specific instances in which it appears previously compromised accounts were re-used to engage in better social engineering.
2. The exploit
The messages contain an attachment which exploits a client side vulnerability. The most common vectors so far have been:
- CHM Help files with embedded objects;
- CVE-2008-0655: Acrobat Reader PDF exploit
- CVE-2006-2492, CVE-2007-3899: Word
- CVE-2006-3590, CVE-2006-0009: Powerpoint
- CVE-2008-0081: Excel
- CVE-2005-0944: Microsoft Access
- CVE-2006-3845: LHA files exploiting vulnerabilities in WinRAR.
The file exploits the vulnerability, and executes shellcode which generally unpacks at least two embedded components:
- The actual Trojan binary: Which can be packed (using UPX, Armadillo, FSG or PE-ARMOR), but in most cases is unpacked and easily retrievable from the file. It is described further in chapter 3 of this diary entry.
- A benign, non-malicious document of the same file type: upon successful execution of the exploit code, it generally “cleans up” and instead of showing an indication that the application has crashed, it drops a clean file to disk (be it either RAR, DOC, PPT or any of the other files affected) and opens it.
The second file shows context very valid to the message initially sent. An example image is included for reference below. This was grabbed from what was sent as a promotional flyer on a book on Tibet. In the background, it dropped a Trojan. Both the flyer and the book exist in real-life form, unbugged. This was an example of taking something which "exists" within the community, and republishing it with trojaned contents.
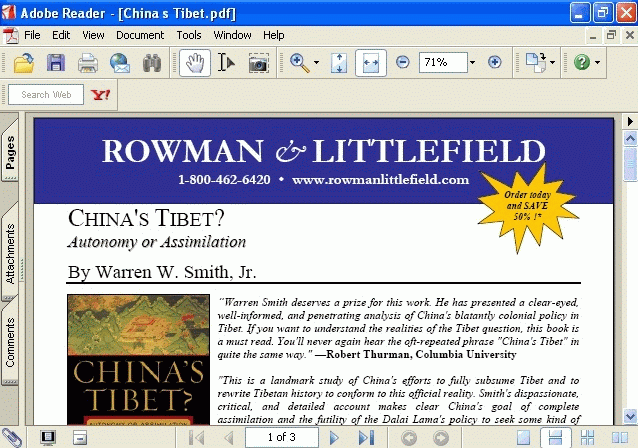
These files usually have very low AV coverage. Below is sample Virustotal output for the malicious PDF sample:
China’s Tibet.pdf
MD5 70d0d15041a14adaff614f0b7bf8c428
AhnLab-V3 2008.3.22.1 2008.03.21 -
AntiVir 7.6.0.75 2008.03.21 -
Authentium 4.93.8 2008.03.20 -
Avast 4.7.1098.0 2008.03.21 -
AVG 7.5.0.516 2008.03.21 -
BitDefender 7.2 2008.03.21 -
CAT-QuickHeal 9.50 2008.03.20 -
ClamAV 0.92.1 2008.03.21 -
DrWeb 4.44.0.09170 2008.03.21 -
eSafe 7.0.15.0 2008.03.18 -
eTrust-Vet 31.3.5631 2008.03.21 -
Ewido 4.0 2008.03.21 -
F-Prot 4.4.2.54 2008.03.20 -
F-Secure 6.70.13260.0 2008.03.21 -
FileAdvisor 1 2008.03.21 -
Fortinet 3.14.0.0 2008.03.21 -
Ikarus T3.1.1.20 2008.03.21 -
Kaspersky 7.0.0.125 2008.03.21 -
McAfee 5257 2008.03.21 -
Microsoft 1.3301 2008.03.21 -
NOD32v2 2966 2008.03.21 -
Norman 5.80.02 2008.03.20 -
Panda 9.0.0.4 2008.03.21 -
Prevx1 V2 2008.03.21 -
Rising 20.36.42.00 2008.03.21 -
Sophos 4.27.0 2008.03.21 Mal/JSShell-B
Sunbelt 3.0.978.0 2008.03.18 -
Symantec 10 2008.03.21 -
TheHacker 6.2.92.250 2008.03.19 -
VBA32 3.12.6.3 2008.03.21 -
VirusBuster 4.3.26:9 2008.03.21 Exploit.PDF.A
Webwasher-Gateway 6.6.2 2008.03.21 Exploit.PDF.ZoneBac.gen (suspicious)
3. The backdoor
Upon successful exploitation, the dropper installs a Trojan. We have monitored over 8 different Trojan families in use. Quite common are Enfal, Riler and Protux. In addition, control over some machines is maintained using the Gh0st RAT remote access tool.
These trojans generally allow close to unrestricted access to the system under the user account which installed the Trojan. Many machines involved in this incident are home desktops, as such this is often the administrator account. The Backdoor generally triggers a few generic signatures, but has very low AV coverage at the time of distribution.
Below is a sample extracted from a malicious Excel document:
event_0310_result.exe
MD5 7d62cec8f022e9599885ad7d079d2f60
AhnLab-V3 2008.3.4.0/20080310 found nothing
AntiVir 7.6.0.73/20080310 found [HEUR/Malware]
Authentium 4.93.8/20080307 found nothing
Avast 4.7.1098.0/20080309 found nothing
AVG 7.5.0.516/20080310 found nothing
BitDefender 7.2/20080310 found nothing
CAT-QuickHeal 9.50/20080308 found nothing
ClamAV None/20080310 found nothing
DrWeb 4.44.0.09170/20080310 found nothing
eSafe 7.0.15.0/20080309 found nothing
eTrust-Vet 31.3.5597/20080307 found nothing
Ewido 4.0/20080310 found nothing
F-Prot 4.4.2.54/20080309 found nothing
F-Secure 6.70.13260.0/20080310 found [Suspicious:W32/Malware!Gemini]
FileAdvisor 1/20080310 found nothing
Fortinet 3.14.0.0/20080310 found nothing
Ikarus T3.1.1.20/20080310 found nothing
Kaspersky 7.0.0.125/20080310 found nothing
McAfee 5247/20080307 found nothing
Microsoft 1.3301/20080310 found nothing
NOD32v2 2935/20080310 found nothing
Norman 5.80.02/20080307 found nothing
Panda 9.0.0.4/20080309 found nothing
Prevx1 V2/20080310 found [Heuristic: Suspicious Self Modifying File]
Rising 20.35.02.00/20080310 found nothing
Sophos 4.27.0/20080310 found [Mal/Behav-116]
Sunbelt 3.0.930.0/20080305 found nothing
Symantec 10/20080310 found nothing
TheHacker 6.2.92.239/20080309 found nothing
VBA32 3.12.6.2/20080305 found nothing
VirusBuster 4.3.26:9/20080309 found nothing
Webwasher-Gateway 6.6.2/20080310 found [Heuristic.Malware]
4. The control connection
In order for the Trojan to be effective, it needs to “phone home”. This usually (but not always) consists of two steps:
- A DNS lookup to acquire the address of the control server;
- The actual connection.
The DNS lookup occurs for a hostname embedded in the Trojan. So far, we have tracked over 50 unique hostnames. Some are used against a single organization or individual, others are used across the spectrum to many different targets.
Interestingly, attacks are “timed”. Let’s look at some DNS resolution logs:
+ 2008-03-22 06:05 | dns3.westcowboy.com | 210.162.89.242
- 2008-03-22 06:05 | dns3.westcowboy.com | 127.0.0.1
+ 2008-03-22 15:07 | dns3.westcowboy.com | 127.0.0.1
- 2008-03-22 15:07 | dns3.westcowboy.com | 210.162.89.242
+ 2008-03-23 07:18 | dns3.westcowboy.com | 210.162.89.242
- 2008-03-23 07:18 | dns3.westcowboy.com | 127.0.0.1
+ 2008-03-23 09:54 | dns3.westcowboy.com | 127.0.0.1
- 2008-03-23 09:54 | dns3.westcowboy.com | 210.162.89.242
When the hostname resolves to one of the above IP addresses, a connection is set up. When it resolves to 127.0.0.1 however, the compromised machine will no longer connects out.
As several IDS rules are available to trigger on lookups that result in 127.0.0.1, we are also seeing samples that contain a check for a specific ‘code’ IP. When the control server resolves to this address, the Trojan holds for a few minutes, then does another lookup. These “parking addresses” have included 43.44.43.44 and 63.64.63.64.
In the above example, this indicates that the team behind these attacks was busy gathering data from 06:05 till 15:07, only to start again almost exactly one day later, 07:18.
In a few cases, the control connection has been regular HTTP or HTTPS, set up using code injected into the Internet Explorer process. This allows the Trojan to be proxy-aware. In other instances, there have been control connections that were fully binary (such as Gh0st RAT) or encrypted using an obvious XOR key.
Some control connections can be detected on the network or proxy level, such as those of certain Riler and Enfal families:
When started, Enfal issues HTTP POST requests to the controller for:
/cgi-bin/Owpq4.cgi
/cgi-bin/Fupq9.cgi
The Riler Trojan family can also be identified through its connection protocol (bold is the infected client submitting data):
NAME:
NAME: [hostname].VER: Stealt h 2.6 MARK: fl510 OS: NT 5.0.L_IP: 10. 2.0.18.ID: NoID.
LONG:0501_LOG.txt
NULL
AUTO
ERR code = 02
SNIF
ERR code = 02
WAKE
WAKE
It also has a recognizable command set:
LOCK SEND WAKE NAME MOON KEEP DISK FILE
DONE DOWN LONG MAKE ATTR KILL LIKE SEEK
READ DEAD DDLL AUTO READY
5. The control server
The vast majority of control servers were identified on Chinese netblocks. However, servers have been identified in the USA, South Korea and Taiwan. The host names pointing to these servers are often configured on dynamic DNS services such as 3322.org. While these services in themselves are not malicious, they are heavily used in these specific attacks.
At the moment, it appears at least a number of the control servers have been compromised using open Terminal Services (RDP/3389) combined with weak passwords.
Based on the technical data, it is impossible to say who is the culprit in these attacks. What is however clear is that these NGOs are systematically hampered using malicious code, either with as goal to gain access to their communications, or to make them reluctant to use e-mail to begin with.
While this is not the full picture on the attacks, we hope this overview already proves useful, and please get in touch if you have questions or additional feedback.
Cheers,
Maarten Van Horenbeeck
Maarten at daemon.be
In short
A few things to look out for after the weekend.
- Ken mentioned that he saw an uptick in port 139 traffic over the weekend. The Dshield data supports this and also shows a spike in port 139 traffic on the 22nd. Port 139 is always busy, but it may be prudent to pay it some extra attention.
- In Oceania, Phising attacks have changed. Rather than the usual security upgrade, the message invites the user to answer a survey with 1 in 10 winning a Sony Laptop. Needless to say the first thing you have to do is enter all your details.
- Over the last week or two there have been more instances of the Death Threat SPAM emails. These particularly nasty messages explain how someone you know wants you dead and the hired killer is contacting you to make a deal. These can be very upsetting for the recipient. Whilst they are typically spam messages treat them seriously and report them if you feel it is necessary.
Other than that it is business as usual, PHP injection attacks, Malicious javascript. The usual.
Cheers
Mark.

Comments